| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
A new ransomware is being distributed by the Magnitude exploit kit: Magniber (detected by Trend Micro as RANSOM_MAGNIBER.A and TROJ.Win32.TRX.XXPE002FF019), which we found targeting South Korea via malvertisements on attacker-owned domains/sites. The development in Magnitude’s activity is notable not only because it eschewed Cerber—its usual ransomware payload—in favor of Magniber. Magnitude now also appears to have become an exploit kit expressly targeting South Korean end users.
The Magnitude exploit kit, which previously had a global reach, was offered as a service in the cybercriminal underground as early as 2013. It then left the market and became a private exploit kit that mainly distributed ransomware such as CryptoWall. At the start of the second half of 2016, Magnitude shifted focus to Asian countries, delivering various ransomware such as Locky and Cerber. More recently though, we noticed that Magnitude underwent a hiatus that began on September 23, 2017, and it then returned on October 15. With help from Kafeine and malc0de, we were able to uncover Magnitude’s new payload, Magniber.
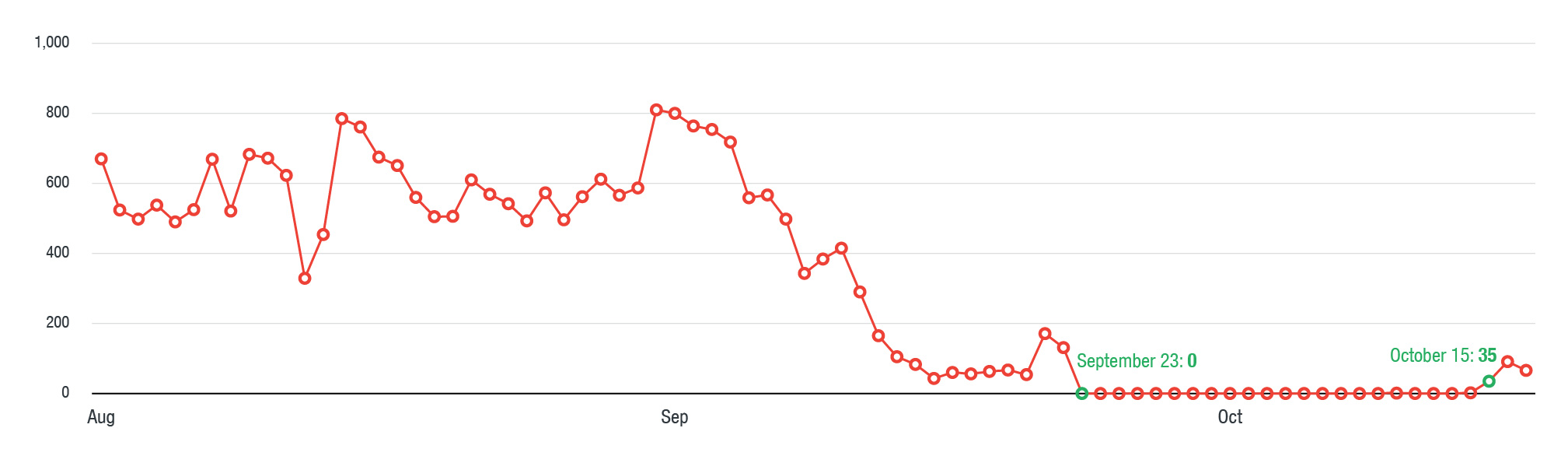
Figure 1. Timeline of Magnitude exploit kit’s activity from August 1 to October 18, 2017, showing its decline in activity before resurfacing with Magniber as payload
Where has Magnitude gone?[出自:jiwo.org]
Taiwan represented 81 percent of Magnitude-based attacks from August 1 to October 17. Starting October 15, however, it has focused on targeting South Korea, as shown by the timeline of its activity.
Magnitude delivers its payload via malvertisements that filter victims using the geolocation of the client IP address and system language. It’s a staple technique used by exploit kits and other cybercriminal campaigns to evade detection and hide their activities from security researchers.
For now, Magnitude only exploits one vulnerability to retrieve and execute the payload: CVE-2016-0189 (patched last May 2016), a memory corruption vulnerability in Internet Explorer. This flaw is also used by other exploit kits like Disdain, Sundown-Pirate, Sundown, and Bizarro Sundown, as well as by other threat actors.

Figure 2. Magnitude exploit kit’s infection chain (top) and CVE-2016-0189 exploited to run Magniber (bottom)
Magniber Ransomware
Magniber checks the language installed in the infected system, as shown in the screenshots below. Magniber will only fully execute if the installed language matches the locale identifier string 0x0412, which is the identifier for Korean.
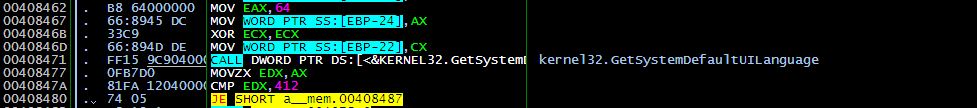
Figure 3. Code snippets of the file loaded in the memory (top), and a snapshot of Magniber’s infection routine once the system matches the UI langugae (bottom)
It appears that Magniber may be one of the few country- or language-specific ransomware. While many ransomware families like Cerber, SLocker, and Locky are increasingly pinpointing their targets, they’re still distributed globally. They typically integrate multilanguage checklists and functionalities in their codes, such as when serving ransom notes and redirecting victims to their payment pages. Some borrow a publicly available source code and just customize it depending on their target. Last year, for instance, we saw KaoTear, a Korean language-specific ransomware based on Hidden Tear.
And based on the code we’ve so far seen within Magniber, the ransomware can also be taken as still in experimental stages—perhaps under the auspices of Magnitude’s developers. Indeed, we’re bound to see more developments in both Magnitude and Magniber as their capabilities and tactics are fine-tuned.
While Magnitude’s distribution of Magniber is still relatively muted, their ability to exploit security gaps in the system and encrypt its files makes their combination a credible threat. Apply best practices to mitigate damage. Minimize your system’s attack surface by keeping it and its applications updated and regularly backing up files. Enterprises should also secure their gateways, endpoints, networks, servers, and other parts of their IT infrastructure that manage business processes.
Trend Micro Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by ransomware such as Magniber. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users. At the endpoint level, Trend Micro™ Smart Protection Suites, powered by XGen™ Security, deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimize the impact of this threat. Trend Micro™ Deep Discovery Inspector™ detects and blocks ransomware on networks, while Trend Micro™ Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro™ Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware. For home users, Trend Micro™ Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat. Our machine learning capabilities, powered by XGen™ security, detect this threat even without the need of an update.
Indicators of Compromise:
Hash detected as RANSOM_MAGNIBER.A (SHA256):
- 2e6f9a48d854add9f895a3737fa5fcc9d38d082466765e550cca2dc47a10618e
C&C domain and IP address related to Magniber ransomware:
- psuutsnokbe6k8ody24[.]bankme[.]date
- 185[.]99[.]2[.]183
Malvertisement domains/IP addresses related to Magnitude exploit kit:
- fastprofit[.]me
- 9kedm134f0[.]artedit[.]today
- 213[.]32[.]105[.]224
- 51[.]254[.]93[.]62
Domain/IP address related to Magnitude exploit kit:
- 8c00sfm2rf27war27eue[.]bypint[.]schule
- 5[.]135[.]10[.]44
With additional analysis by Edmark Dungca and Matthew Camacho
We would like to acknowledge the contributions of Kafeine and @malc0de whom we worked with in this research.
Updated as of October 18, 2017, 8:05PM PDT to include our machine learning-based detection and solution.

