| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
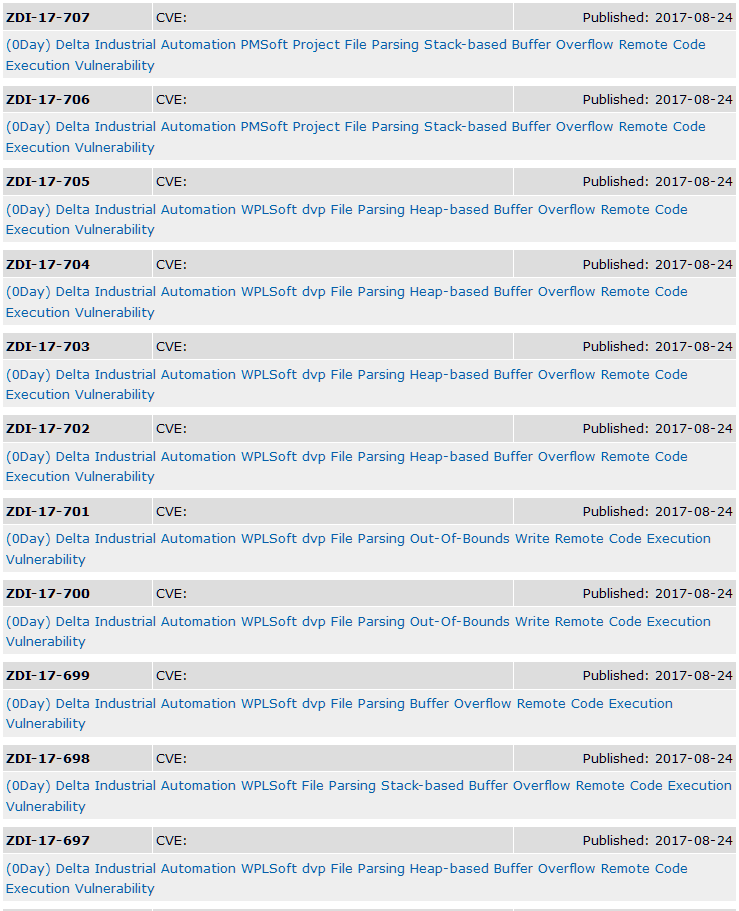
台达PLC编程软件PMSoft和WPLSoft爆出11个0Day漏洞,美国ICS-CERT已经获知漏洞情况,台达,这些0Day漏洞经过120天后,没有看到台达发布补丁,相关信息被公开。 [出自:jiwo.org]
台达是工业自动化厂商
据其官网资料显示
台达是全球电源管理及散热方案的领导厂商,二十多年来,目前共设有广东东莞、江苏吴江、安徽芜湖、湖南郴州四个主要生产基地;二十三个研发中心 (超过3,000名研发工程师)、49 个运营网点、73个服务网点,员工总数达5万余人。台达中国区2016年的营收超过397亿人民币。
台达PLC编程软件PMSoft 0Day漏洞列表
(0Day) Delta Industrial Automation PMSoft Project File Parsing Stack-based Buffer Overflow Remote Code Execution Vulnerability
漏洞描述:
This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Delta Industrial Automation PMSoft. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.
The specific flaw exists within parsing of information for a TTreeView object in a new-format ppm project file. The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a fixed-length stack-based buffer. An attacker can leverage this vulnerability to execute arbitrary code under the context of the current process.
缓解办法
Given the nature of the vulnerability the only salient mitigation strategy is to restrict interaction with the application to trusted files.
(0Day) Delta Industrial Automation PMSoft Project File Parsing Stack-based Buffer Overflow Remote Code Execution Vulnerability
漏洞描述:
This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Delta Industrial Automation PMSoft. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.
The specific flaw exists within parsing of information for a TTreeView object in a ppm project file. The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a fixed-length stack-based buffer. An attacker can leverage this vulnerability to execute arbitrary code under the context of the current process.
缓解办法
Given the nature of the vulnerability the only salient mitigation strategy is to restrict interaction with the application to trusted files.
台达PLC编程软件WPLSoft 0Day漏洞列表
由于内容较多,请参加直接查看
http://www.zerodayinitiative.com/advisories/published/