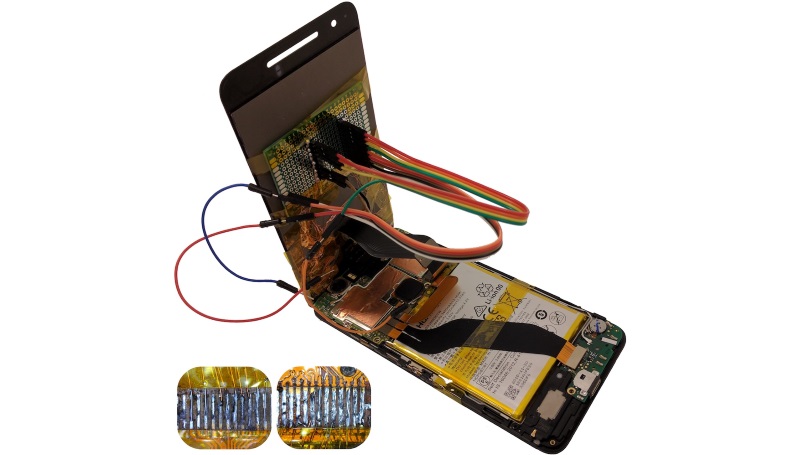
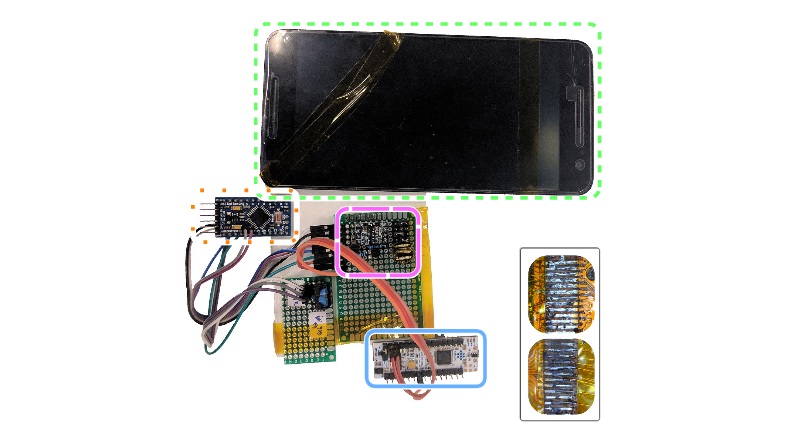
Attackers could hide malicious chips in phone spare parts
Researchers proved their theoretical attack true by building such malicious spare parts and using them to take over a test smartphone. Video proof is available at the end of this article.
While the attack looks complex, researchers said they used only off-the-shelf electronics that cost about $10. Although some practical skills in soldering and handling electronic parts are needed, the attack is not as sophisticated as some might think and does not involve complex machinery often installed in high-tech factories.
|
|
|
Two ways to carry out attacks via spare parts
With the malicious spare parts they created, researchers say they discovered two categories of attacks they could perform.
The first is a basic command injection into the communication streams between the phone and the spare component. This attack works best with malicious touchscreen displays because it allows the attacker to impersonate the user by mimicking touch actions and exfiltrating data.
The second method is a buffer overflow attack that targets a vulnerability in the touch controller device driver embedded within the operating system kernel. Attackers exploit this flaw to get elevated privileges on the phone and carry out attacks on the OS itself, without needing to mimic touch gestures. This second attack was specific to one set of device drivers, so it won't work universally.
The research team — formed by experts from the Ben-Gurion University of the Negev, Israel — present various hardware-based countermeasures for preventing attacks via spare parts in their research paper.
The countermeasures and other technical details are available in their paper titled "Shattered Trust: When Replacement Smartphone Components Attack," here and here. Researchers presented their work at the recently concluded USENIX W00T '17 security conference.
The five videos below show the research team carrying out chip-in-the-middle attacks on smartphones that contain malicious spare parts.