| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
Today, BleepingComputer discovered a new variant of the CryptoMix ransomware that is appending the .ERROR extension to encrypted file names. This article will provide a brief summary of what has changed in this new variant.
As we are always looking for weaknesses, if you are a victim of this variant and decide to pay the ransom, please send us the decryptor so we can take a look at it. You can also discuss or receive support for Cryptomix ransomware infections in our dedicated Cryptomix Help & Support Topic.
Changes in the ERROR Cryptomix Ransomware Variant
While overall the encryption methods stay the same in this variant, there have been some differences. First and foremost, we have a new ransom note with a file name of _HELP_INSTRUCTION.TXT. This ransom note contains instructions to contact either error01@msgden.com,error02@webmeetme.com, or error03@protonmail.com for payment information.
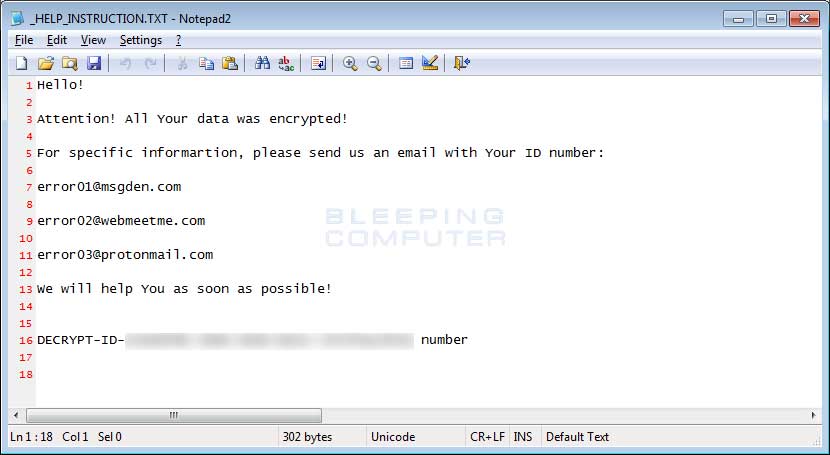 ERROR CryptoMix Ransom Note
ERROR CryptoMix Ransom Note
The next noticeable change is the extension appended to encrypted files. With this version, when a file is encrypted by the ransomware, it will modify the filename and then append the .ERROR extension to encrypted file's name. For example, an test file encrypted by this variant has an encrypted file name of 36C25A08104EA9E6B8B1F4AC14CC8926.ERROR.
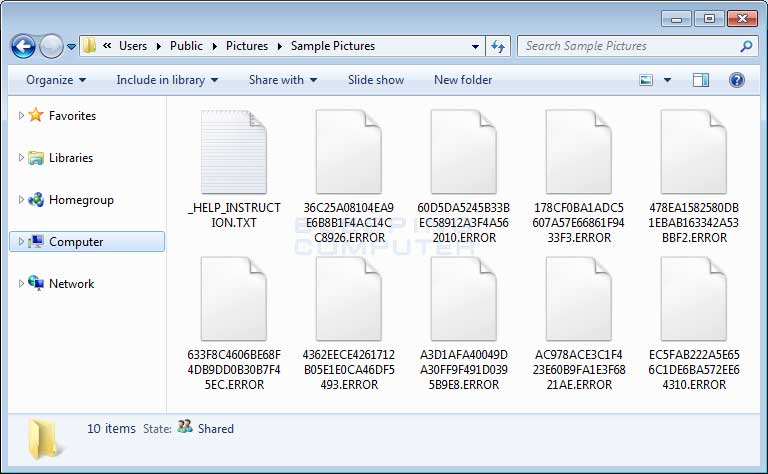 Folder of Encrypted ERROR Files
Folder of Encrypted ERROR Files
This variant contains 11 public RSA-1024 encryption keys that will be used to to encrypt the AES key used to encrypt a victim's files. This allows the ransomware to work completely offline with no network communication.
As this is just a cursory analysis of this new variant, if anything else is discovered, we will be sure to update this article.[出自:jiwo.org]
IOCs
File Hashes:
SHA256: 9583a703f23f03aad5541c363aa2495a6497aa0091d75d46a4adf469d5c520b2
Executed Commands:
sc stop wscsvc
sc stop WinDefend
sc stop wuauserv
sc stop BITS
sc stop ERSvc
sc stop WerSvc
cmd.exe /C bcdedit /set {default} recoveryenabled No
cmd.exe /C bcdedit /set {default} bootstatuspolicy ignoreallfailures
C:\Windows\System32\cmd.exe" /C vssadmin.exe Delete Shadows /All /Quiet
Filenames associated with the ERROR Cryptomix Variant:
_HELP_INSTRUCTION.TXT C:\ProgramData\[random].exe
Registry entries associated with the ERROR CryptoMix Variant:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[random]"="C:\ProgramData\[Random].exe""
ERROR Ransom Note Text:
Hello! Attention! All Your data was encrypted! For specific informartion, please send us an email with Your ID number: error01@msgden.com, error02@webmeetme.com error03@protonmail.com We will help You as soon as possible! DECRYPT-ID-[id] number
Emails Associated with the ERROR Ransomware:
error01@msgden.com, error02@webmeetme.com error03@protonmail.com
Bundled Public RSA-1024 Keys:
-----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCyagbOaf3s/ePCxre9cs9BwaX3 D40qF7jAzB/xoWktfDlY2PVslZ2reYhQC9dSIvkEtuZqlUUYgFUdaaqTsE7pA8ik 2zXI5Ou7I0YtwWRoFNCl8YlMTRKgDHRQhclPNbtpi2ucm507Unr8EnT2ZzcTOYv1 7ITFgkBdNr4zHLFrpQIDAQAB -----END PUBLIC KEY----- -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDChVnFfbDa3rp1sug7tbE6ba/O RWAwsk6WQ21XHgAXF7dKuEtG/4q7QJyHahQvys2oLkJ4Et2+S4YS3FSYXYqNOq/e 5ahdS19KiuGLnf1u7acnsGvikJgvXiwe/NH2h48ZtK0Uyn1Q1ijVNU66f1pehSmB YQupamnC2XkV9d6Z0wIDAQAB -----END PUBLIC KEY----- -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDXbf7u6Pq5kB+O1Cb9GIG9GlVG Mswk342Er1HMiHFXUsVMlljLFTJPz5rdcVB4QAXsOynm67uw8yEAlNC90AHohuIV dGDNVoQuuyNvanI1Ur4cA4aKqpJZKbkVauTpCDdEAse4LSH4NrGTgCao42jiaksj pZvKyFK8yvdoAwd3JQIDAQAB -----END PUBLIC KEY----- -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCetENrtjivjYOthpX2yTlYKJ0x gZ0R367J8tSFikEhVoko4SKRmN9Y1s88iCdeRPUZh2Q0rHOesf/AxONK1buzygXl BkE5X86I3EFUFbPjyOnIgEKFru728aLlwkslqYPIWS29DZUCboHzv1YWU8gtFkwL 5bUEB444se2UXi+pjwIDAQAB -----END PUBLIC KEY----- -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCQa9aSkupoA7jxeOhS/mbRvy4u H/hI6XbTsv+ilfj8v9XHBaptsExUvCDG3fXvDKxSLxa6HBXnemM3weUDS0njH9Sb MJjImRjQ+OambwAYaj/hnFM3TYWU4KhPPKWrsxHT1ReSo1i+G2bNxr2gyS2D606N xaN4LNmYw3PLL2omGQIDAQAB -----END PUBLIC KEY----- -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCIiEAs1V5JBCLKmDy0Il6rfC4w pQm0s9224Yvxs5pRRic3IQwAJ6wWw0Nrl42LxiA88jggso2EZ05lAl9FIuCNvzCr PO2QOjRLT0w2bYEEneK+rQR9sexZSI90zYVjziI26muOG1M8neAHqWkPvZI1a1sd hG5MwboKBkPYbtXI1wIDAQAB -----END PUBLIC KEY----- -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC4ShCcW3W2gmG5HT/Vcrzf4HKi OXAmVWpTRkyqxkw/wU7Ax+A63Fgo5tV4psuxHcJUGYQv4B8+Ag+POHmE4a7Vd4Ra 7tVXBEoyl1ZKF8fFCAAaw6G/ALCL0LEQiTLaqQuIjNXRo7S4Mt/alOM18uMP/kEA mqnGDXEblePIsMUzkQIDAQAB -----END PUBLIC KEY----- -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDOXllDk/itDr0oW7hxm01XLeEo pVCg63jWxr5ZEKMU3zmYPtIPGayJbOacU+pPf6t77IMR8ainmJXjAK1c0V07XJv2 UrRsQARYDGEnItYphiYI7t1AgXSPoUi8pvQJrpja3WpuFNmhsWE2lz5uEO7QeejG jSToXALGsvmgvGq5SQIDAQAB -----END PUBLIC KEY----- -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCWeBww97UHcRLjztOKvXB0xzRC LcZGov/Y/6x/m8uo42nLkyPgUjrqR7EAzB6bbB6L6aOgCJb2WyffOaNN5df07gIV f1Ea8u/jMIr5uhR+pnFMNB0jQIqqU9/slURM+U7dFvELbli5HL+7Ac/EehJNjLNW bpB5dTPCSSpKFoeoxQIDAQAB -----END PUBLIC KEY----- -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCIX+Ay2zjnnViZsCDCk/TS2wZV 85YVVWpAXzsu4wzJzo4Mux2PK5pW0+i6+O1KZLcu+d5xElKM0KgrmE8uY1xylA18 SMBHHhBNhJdYXIaARFNp1uRG+kR8IDgT3sDrSseTt//l2tn8oo5xxw6UHtsBqRwF KP3u+Vspd+gFRsTC5wIDAQAB -----END PUBLIC KEY----- -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCxsV6vYenwHV4noHlPuOL/Dc7b dcLDWzJCmCToF5wCnUdkeifop7s6Kuz4nujPWq+6/foz5od8GySTtKiZtoq3lcmI 04RMzKqvo1PkR4RzfXGBLVk6EqeCrueY86l8Gu71oiPois8jJV6VQ96IJuc0HNRb IVKuPQZRttC1CjuZHQIDAQAB -----END PUBLIC KEY-----

