| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
Introduction
RustScan is a fast port scanner capable of scanning both IPv4 and IPv6 networks. The tool also claims to use Adaptive Learning to improve itself over time. This article features a short guide on setting up and using the RustScans port scanning capabilities. [出自:jiwo.org]
RustScan is the next tool on our list that can be used to scan for IPv6 addresses for open ports and to discover services running on them. RustScan internally uses nmap to do all the scanning and is more a multithreaded wrapper on top of nmap than an independent scanner in itself.
RustScan is an insanely fast scanner. The documentation pegs the scanning speed at all 65k ports in 3 seconds! All of this is possible using Rust’s threading capabilities that allows multiple instances of nmap to run in parallel and manage their socket connections.
This article will guide you through the installation of RustScan and how to use the tool to scan an IPv6 network.
Notes:
- RustScan has support for most Linux operating systems, though the tool does not officially support Windows. However, it is possible to run RustScan on Windows (and other OSes) using Docker.
- RustScan requires nmap since it is the scanning engine it uses.
- Make sure that the scans are conducted on the networks where you are allowed to do so with appropriate permissions.
Before we begin
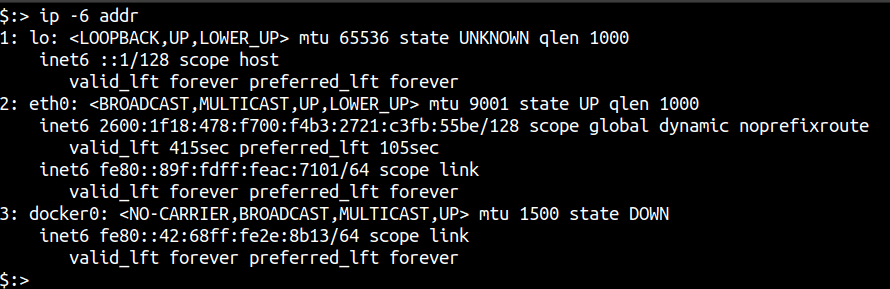
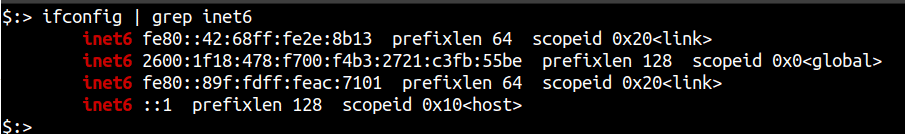
Like any other IPv6 scanning tool, your system needs to support IPv6 in order to utilise RustScan’s scanning capabilities. To verify that your system and network are properly configured to have IPv6 access, you can run either of the following commands:
-
ip -6 addr
-
ifconfig | grep inet6
Setting up RustScan
According to the documentation, Docker is the recommended way of installing RustScan. The following advantages are highlighted in the documentation regarding the same:
- Docker has a high open file descriptor limit, which is one of the main problems with RustScan.
- Docker works on all systems, regardless of OS. Even Windows, which is not officially supported.
- The Docker image uses the latest build from Cargo, which provides the latest version of RustScan.
- No need to install Rust, Cargo, or Nmap
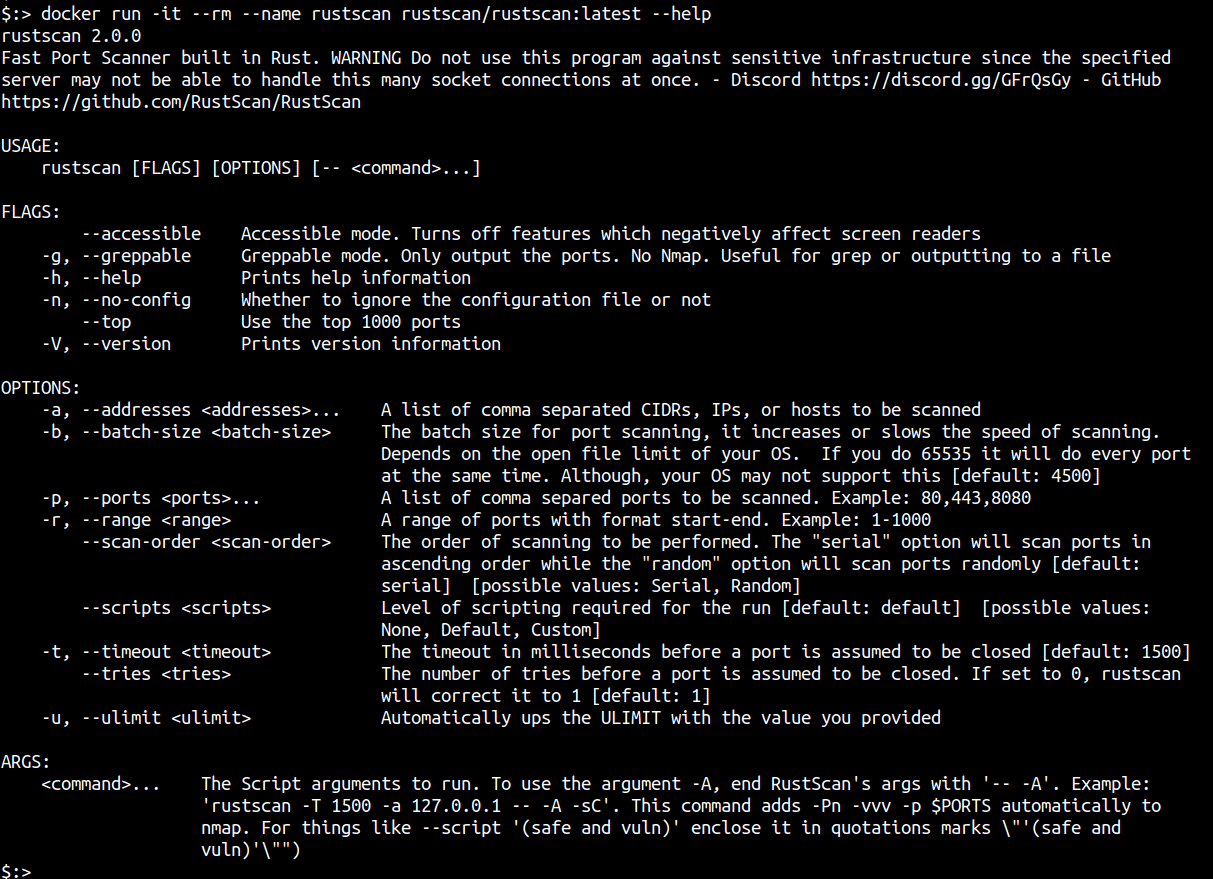
Using Docker, the following command can be used to run RustScan
docker run -it --rm --name rustscan rustscan/rustscan:latest --help
Scanning IPv6 with RustScan
The GitHub documentation is a little vague about how to operate RustScan with docker and IPv6 addresses. However, some experimentation led us to the following results:
- Like all IPv6 scanners, RustScan also needs the host to support IPv6 addresses. The easiest way on Docker (although not the most secure way) is to share the host system’s networking stack with the container (assuming the host already supports IPv6). This can be achieved with the --net=host argument to docker run.
- Also, since RustScan uses nmap as the underlying engine, all of nmap’s arguments are available by passing a — to denote completion of RustScan arguments and to begin nmap arguments.
- Additionally, the default ports per second that RustScan scans for is 4500, this can be controlled to slow or hasten up the scans by using the -b option (batch size). Theoretically, an option of -b 65535 will scan all ports in 1 second.
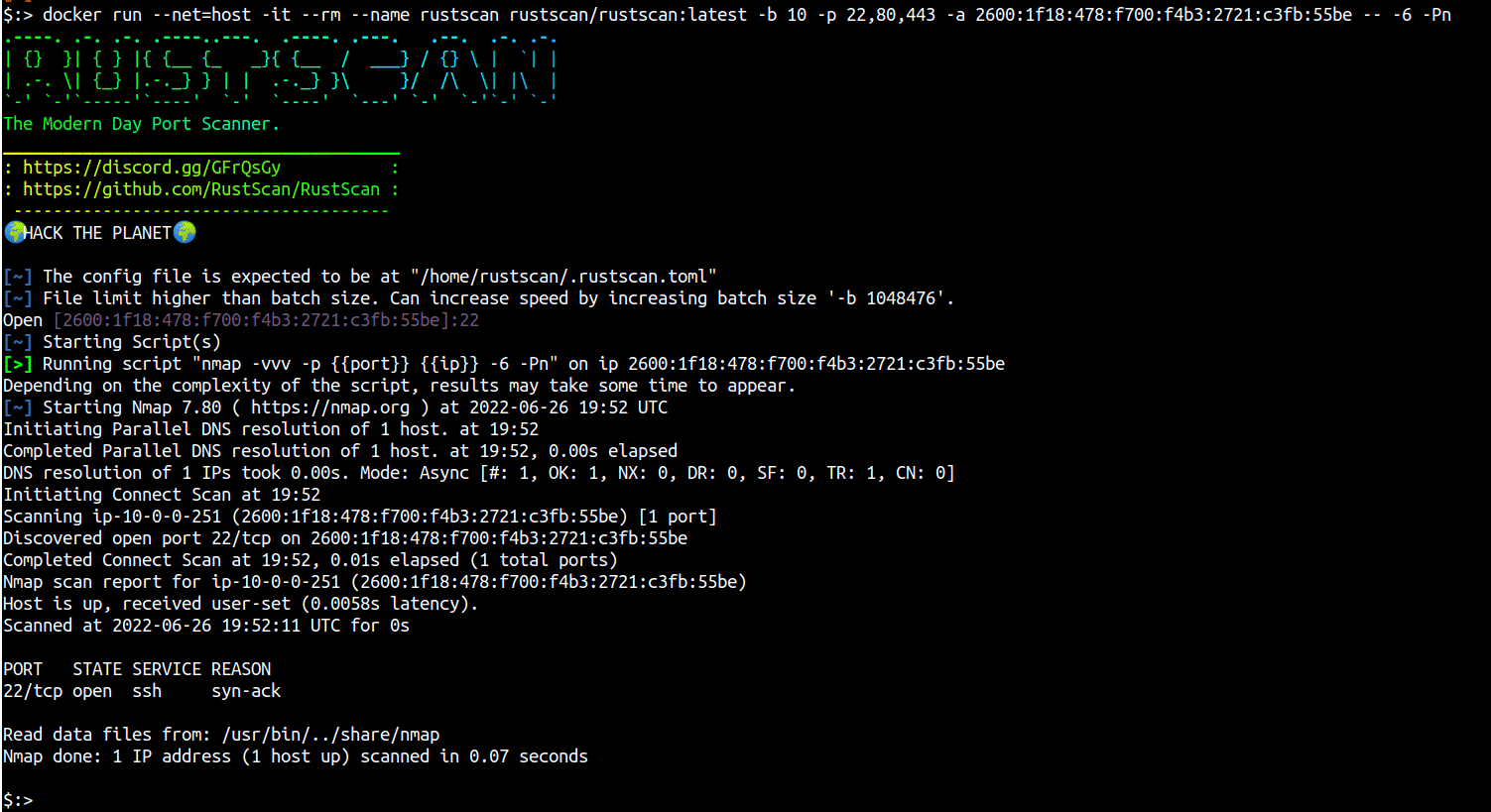
Let’s take an example, the following docker command will pull the latest image of RustScan, share the host networking stack with the container and perform an IPv6 scan on the address 2600:1f18:478:f700:f4b3:2721:c3fb:55be for TCP ports 22,80 and 443 by assuming the system is online (no ping scan confirmation before port scan - nmap specification).
docker run --net=host -it --rm --name rustscan rustscan/rustscan:latest -b 10 -p 22,80,443 -a 2600:1f18:478:f700:f4b3:2721:c3fb:55be -- -6 -Pn
Conclusion
In this article we looked at RustScan, which is essentially a wrapper on top of nmap that is written to utilise the operating systems capabilities of sending many network probes without being restricted by nmap’s limitations.
The most recommended way of running RustScan is using its Docker image. RustScan supports all nmap flags and its reporting capabilities are the same as that of nmap.
This article is part of a series on scanning IPv6 addresses. Come back for our next article in the series in which we will take a look at another IPv6 scanner - masscan.

