| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
Executive summary
-
Akamai researcher Ben Barnea found an important vulnerability in the Windows Server service that was assigned CVE-2022-30216 and a base score of 8.8. [出自:jiwo.org]
-
The vulnerability takes advantage of an off-by-one error in a security callback procedure that the Server service implements.
-
We confirmed that the vulnerability exists in unpatched Windows 11 and Windows Server 2022 machines.
-
When combined with a New Technology LAN Manager (NTLM) relay attack on the Active Directory Certificate Services (AD CS), the vulnerability gives an attacker with domain credentials the ability to run code remotely on the domain controller.
-
We also believe that an attacker might be able to use this technique to modify a server’s certificate mapping and therefore perform server spoofing.
-
The vulnerability was responsibly disclosed to Microsoft and addressed in July’s Patch Tuesday.
-
We provide a proof of concept of the vulnerability in our Github repository.
Introduction
During the recent months, our team has conducted thorough research of Microsoft’s remote procedure calls (MS-RPC). Put simply, an RPC is used for efficient interprocess communications. It relies on a standard client-server model, and is one of the most widely used protocols in Windows today.
One of the more interesting aspects we have identified in the MS-RPC design is the security callback, which functions to restrict access to RPC servers, essentially providing security from unwanted, often remote, users. Many RPC servers implement a security callback, each server with its own logic and considerations.
Windows services make extensive use of RPC to make their functionality available for clients. This led us to investigate different services and the underlying logic of their security callback implementations. In one such service — the Server service — we were able to find a security flaw that could allow attackers to perform server spoofing or trigger authentication coercion on the victim.
In this blog, we will outline the aspects of RPC we have been researching that collectively contribute to this newfound bug: what the bug is, how it can be used, and how to mitigate it.
What is Windows Server service?
The Server service (also called LanmanServer) is a Windows service that is responsible for the management of SMB shares. Shares are resources — files, printers, and directory trees — that are made accessible over the network by a Common Internet File System server. Essentially, network shares allow users to utilize other devices on the network to perform various daily tasks.
The Server service allows a remote machine to create, configure, query, and delete shares through RPC over a named pipe (\\pipe\srvsvc). For the remainder of this post, we will refer to the service as srvsvc.
A vulnerability in srvsvc is impactful because the service provides core functionality and therefore runs by default on every Windows machine.
SMB over QUIC
From Windows 10 20H2 onwards, Microsoft introduced a new feature — SMB over QUIC. The feature allows access to SMB shares through QUIC, a new transport-layer network protocol. QUIC’s purpose is to provide a more reliable and secure connection while also overcoming common internet problems, such as latency and packet loss.
In a QUIC network interaction, as an additional security measure, the client verifies the identity of the server by checking the certificate provided by the server. With the addition of SMB over QUIC, the Server service became responsible for managing those certificates.
The vulnerability we found lies in this functionality. To understand it, we first need to explore one of the ways RPC servers perform access control.
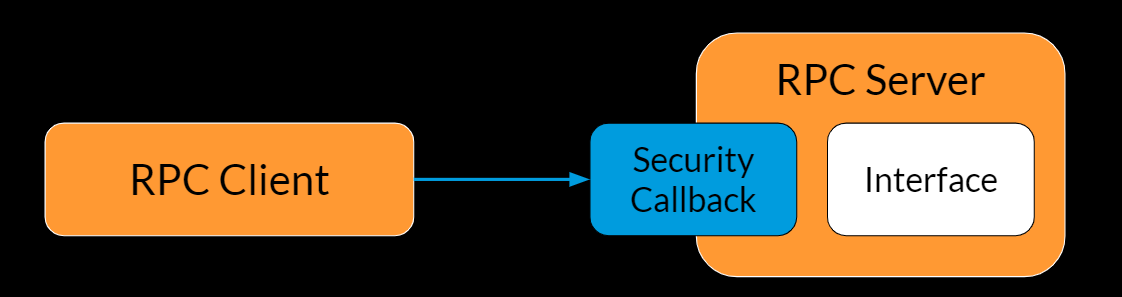
Security callbacks
Many Windows services, srvsvc among them, implement an RPC server to allow for interprocess communication and to provide access to their functionality to different clients. RPC in Windows utilizes various security mechanisms; we will focus on one called security callback.
A security callback’s goal is to restrict access to an RPC interface. The callback is implemented by the RPC server developer, and it allows each developer to apply their own logic to allow access to specific users or prevent access to specific functions. In RPC, functions exposed by the server are represented using opnums (operation numbers), which we will see shortly in srvsvc’s security callback.
A chronicle of a security callback
To understand the bug, we first need to look at an older version of srvsvc’s security callback before the SMB over QUIC feature was added:
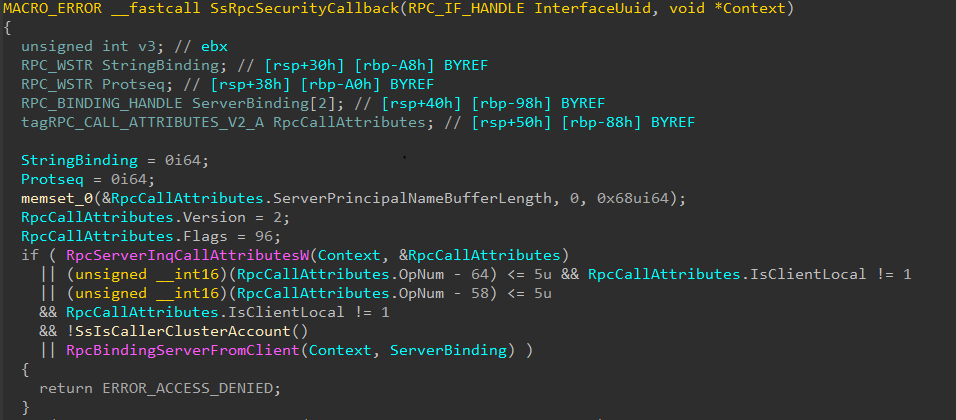 srvsvc security callback — Windows 10 19H2
srvsvc security callback — Windows 10 19H2
As seen above, srvsvc’s security callback has the following logic:
- If a remote client tries to access a function in the range of 64–69 (inclusive) — deny access
- If a remote client, which is not a cluster account, tries to access a function in the range of 58–63 (inclusive) — deny access
So, in essence, remote clients are prevented from accessing these particular functions of the interface. This range check hints that the restricted functions are sensitive and should be invoked by only expected (local) processes.
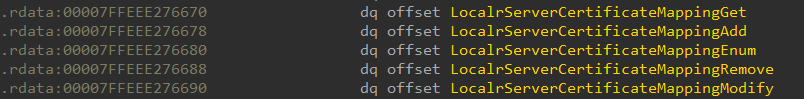
With the addition of SMB over QUIC, Windows 10 20H2 added four new functions to the srvsvc service:
- LocalrServerCertificateMappingGet
- LocalrServerCertificateMappingSet
- LocalrServerCertificateMappingEnum
- LocalrServerCertificateMappingRemove
Since it was undesirable for these functions to be accessed remotely, they were added to the range of local functions — functions that srvsvc's security callback prohibits for remote clients.
And, as seen below, the range was indeed changed to include the opnums for these new four functions, increasing the first local range from 64–69 to 64–73 and extending the security callback’s access control to these functions. So far, so good.
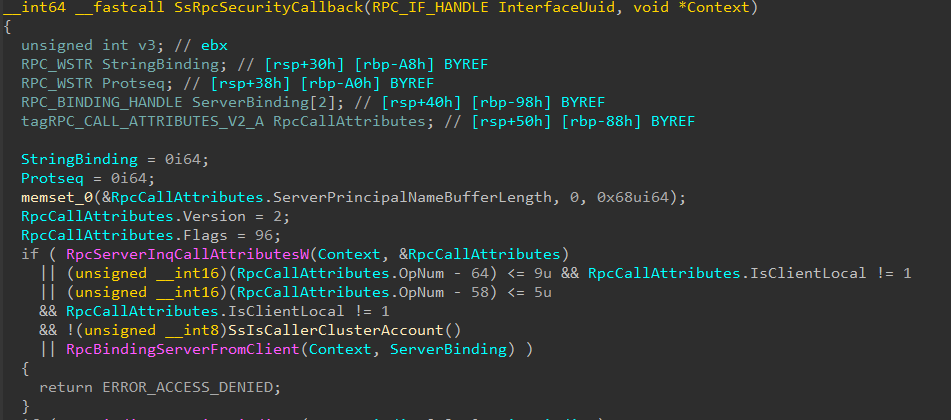 srvsvc security callback — Windows 10 20H2
srvsvc security callback — Windows 10 20H2
In Windows 11 and Windows Server 2022, Microsoft added a new function called LocalrServerCertificateMappingModify:
However, this time, the range of restricted functions has not changed in this newer version to include the newly added function:
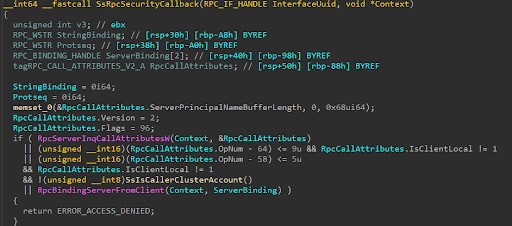 srvsvc security callback — Windows 11/Server 2022
srvsvc security callback — Windows 11/Server 2022
So, at the time when this function was added, it was not covered by the security callback, and was therefore accessible to remote RPC clients.
Exploitation opportunities
By invoking this function, an attacker can change configurations of certificate mappings on the server. A certificate mapping is a “symbolic link” between a server’s QUIC certificate and a certificate in the certificate store. We believe that an attacker might be able to use this function to add their own certificate mapping and therefore perform server spoofing. Be aware that this function does not add or modify a certificate in the Windows certificates store, but changes a mapping of the certificate used by the QUIC server to a certificate in the Windows store.
While trying to assess the impact of the vulnerability, we noticed that the struct that the function receives contains the certificate’s store location:
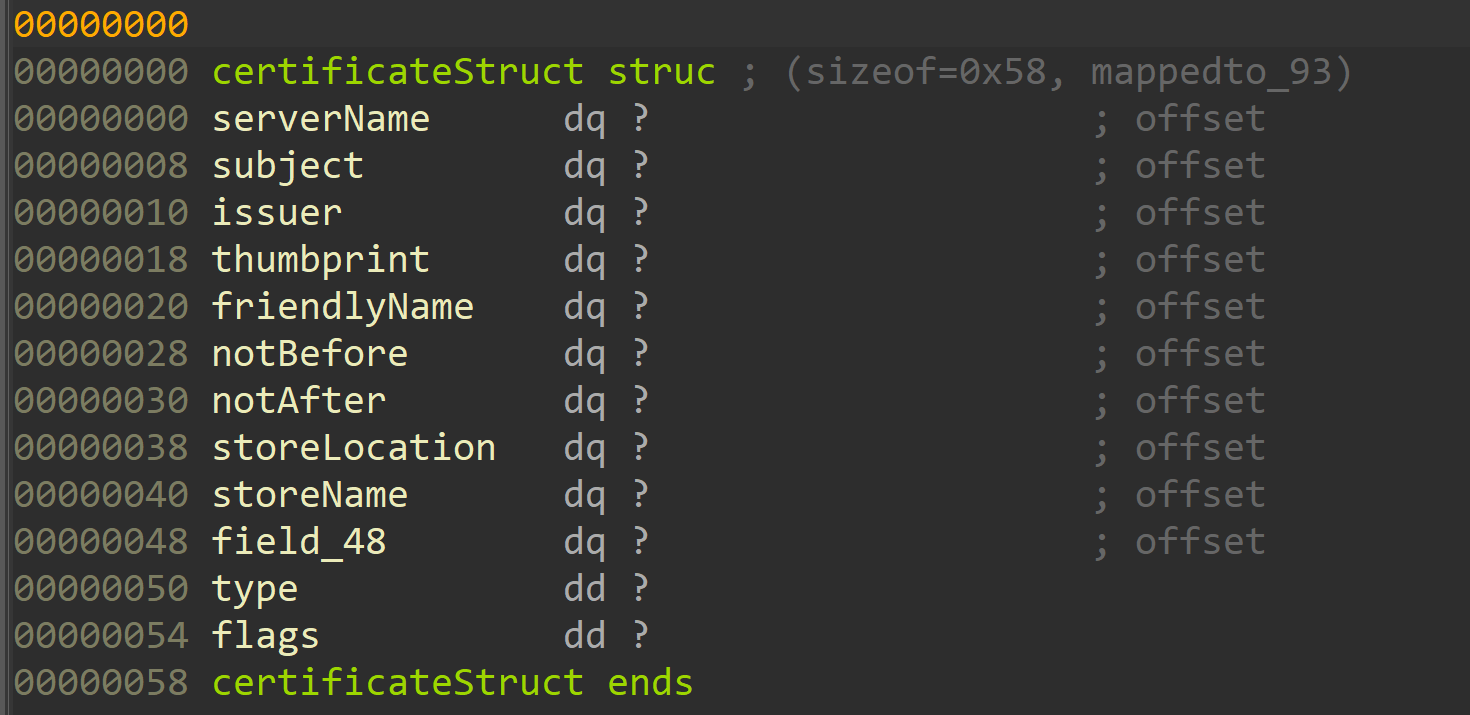
By supplying a UNC path as the storeLocation variable, an attacker can cause LocalrServerCertificateMappingModify to trigger an RPC request from the victim server to a machine that they control. The function flow that causes the request to be fired is:
LocalrServerCertificateMappingModify → SsValidCertandUpdateCertinfo → CertOpenStore → _CertDllOpenSystemStoreProvW → EnumPhysicalStore → FormatSystemRegPath → RegConnectRegistryExW → BaseBindToMachine → Rpc_OpenPredefHandle → NdrClientCall3
During the RPC request that is sent by the server to our machine, the server performs authentication against the attacker’s server. The attacker can now leverage the victim’s credentials to perform an NTLM relay attack.
Exploiting the vulnerability and performing the NTLM relay flow, we managed to replicate the PetitPotam attack scenario of abusing the AD CS and taking over the domain controller.
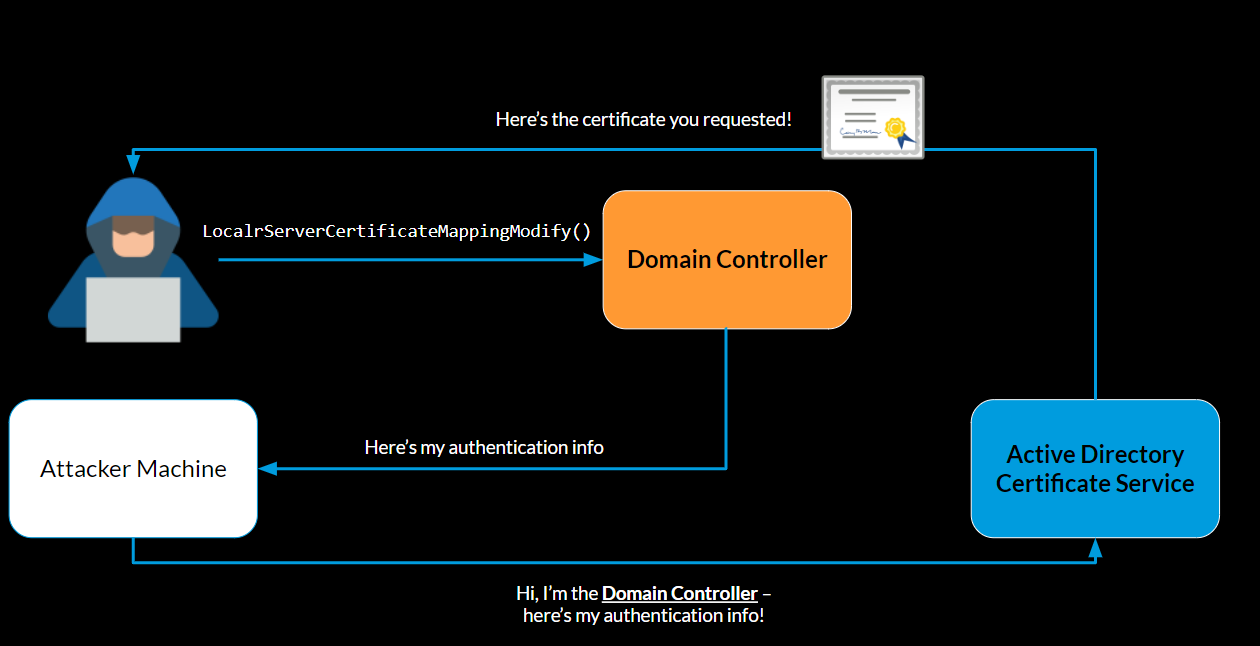
Triggering the vulnerability requires that the attacker have access to a machine in the domain. For the NTLM relay scenario, the AD CS role needs to be added, along with one of its services that are prone to NTLM relay (Certificate Authority Web Enrollment, Certificate Enrollment Web Service).
Fix
Microsoft released a patch for this vulnerability in July’s Patch Tuesday. The issue was fixed by:
-
Correcting the range of local functions in the security callback, thus preventing remote access to LocalrServerCertificateMappingModify
-
Adding an access check in each of the newly added local functions
Disclosure timeline
-
April 26, 2022: A report has been sent to Microsoft
-
April 26, 2022: Status changed from New to Review / Repro
-
May 9, 2022: Status changed from Review / Repro to Develop
-
July 12, 2022: Patch has been released
Mitigation and detection
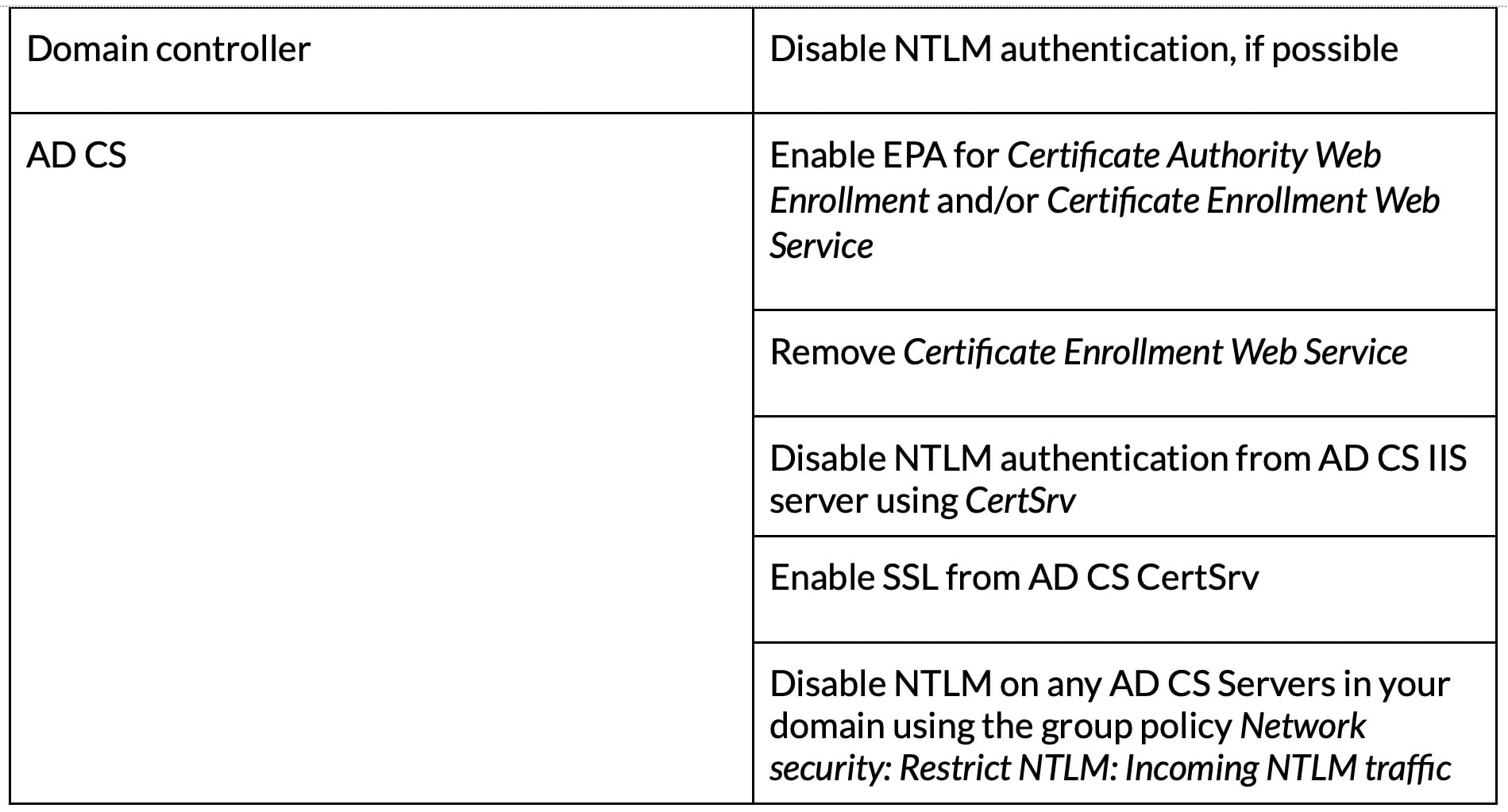
The following are the recommendations to mitigate NTLM relay:
Often, an NTLM relay attack that abuses the AD CS will involve a TGT request. The event log (EventID 4768) will include the requesting machine’s IP address. Malicious TGT requests can be detected if a TGT is requested for a domain controller from a machine that is not a domain controller itself.
A proof of concept available in the Akamai Security Research repository.
Summary
When new features are added, it is important to be mindful of the potential consequences they have — not only in the feature’s functionality itself, but also in the way it is made accessible to users. In our case, SMB over QUIC was added in Windows and introduced new functions to the Server service. However, the vulnerability lay not in the implementation of SMB over QUIC, but rather in the way an older function restricted access to the respective RPC interface.
The Akamai Security Research team has conducted several pieces of research on MS-RPC, starting with an analysis of an RPC runtime vulnerability in April’s Patch Tuesday, as well as an outline of another CVE we found in May. Ben Barnea and Ophir Harpaz presented the Server service vulnerability research at DEF CON 30 in Las Vegas.

