| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
AUGUST 1, 2017
[出自:jiwo.org]
CVE-2017-2840
Tested Versions
UltraISO 9.6.6.3300
https://www.ezbsystems.com/ultraiso
8.8 - CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
This vulnerability can be triggered by providing specially crafted .ISO file and opening it with UltraISO software.
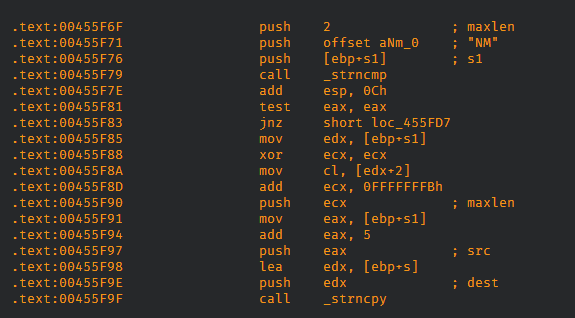
After the "NM" entry is located in the .ISO file UltraISO executes _strncpy function with maxlen argument calculated directly from the ISO header's byte field NM_hdr.len - the length of the alternate name.
UltraISO assumes this field is always larger than 5 bytes however if attacker forces it to be less than that value the maxlen parameter for the _strncpy function will be extremely big (NM_hdr.len - 5, result is unsigned).
Later the memset function (inside the _strncpy function) is executed where the extremely big size parameter is used which leads to memory corruption.
Crash Information