But, let’s start by having a little bit of context:
During the past few days a colleague of mine (MarcoT.) gave me an interesting eMail attachment called: 71878378709_708463.zip (sha256:fdd1da3bdd8f37dcc04353913b5b580dadda94ba).
By unzipping the attachment, it was interesting to see a single .vbs file. By double clicking a .vbs file the victim would run it through microsoft wscript.exe which fires up the infection process. The eMail belongs to a more complex spamming set spread over USA and coming few days ago to Europe as well.
The visual basic script was obfuscated, as you may appreciate from the following image, but the used obfuscation technique was quite weak to reverse. In fact only one round of packing was adopted and after few substitutions “clear text strings” were observable.
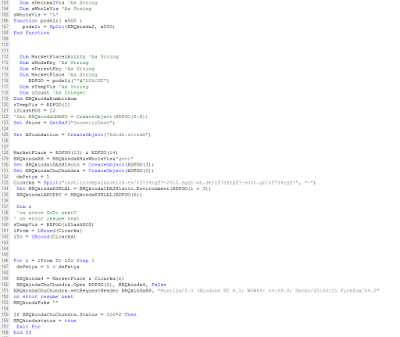 [出自:jiwo.org] [出自:jiwo.org] |
| Obfuscated Dropper |
Interesting techniques were introduced in this dropper. First of all a lot of junk code (apparently good code) was added in order to make reverse engineering process much harder. Very interesting the choice of such a code apparently taken from real droppers but not linked to the analized one. Another interesting adopted technique was on the “User-Agent” settings, which happened to be the key-factor to download the real payload. The dropper per-se is not interesting anymore. It basically uses a romantic WScript.Shell to execute a ‘MZ’ file once downloaded from compromised websites (IoC later on). The Dropped file is returned directly into the HTTP response body and saved with a static name in temporary user folder: saToHxy.exe. The dropper file renamed VB objects and VB functions to make everything a little harder.
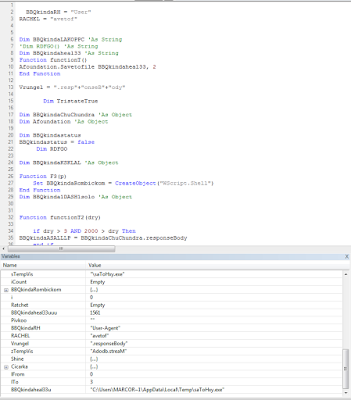 |
| Saving Dropper into user temporary file with static name |
As today the dropping URLs are the following ones:
- castillodepalazuelos.es/rf734rgf?
- 2010.sggt-wh.de/rf734rgf?
- actt.gr/rf734rgf?
As mentioned a romantic Shell.Run would execute the dropped payload. The Payload (sha356:6a51d0cd9ea189babad031864217ddd3a7ddba84) looks like a one-stager payload. No heavy encryption nor multi staging delivery is involved, clear and intuitive user functions within enabled debugging headers.

 |
| No Packing found |
Firing up IDA and reversing the sample showed up small encoded payload through XOR and some anti debugging tricks such as the timing control and performance monitoring as follows:
 |
| Anti-Debugging tricks: Timing and Performante control |
Following on the analysis it becomes clear the spread use of Secure Handler Exception Chain exploiting technique. By triggering exceptions the attacker calls modified exception handler functions able to decode the payload and to allocate it directly on the new memory pages, ending up on “call eax” section. The following image shows the decoding loop.
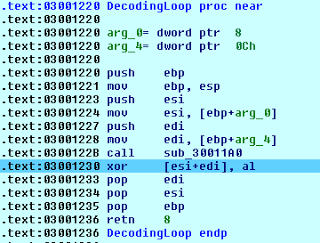 |
| Decoding Loop on 0x3001220 |
Following a piece of decoded memory area (configuration file), decoded by 0x03001220.
 |
| Decoded Memory Area |
Dynamic Analysis took out the evidence of a Ransomware payload. In fact following on the decoded payload by getting far on memory site the analyst could observe the ransom HTML page (next image). I would prefer to show out a rendered “ransom request page” rather than a junk of hexadecimal bytes. (sha256: cdb3fef976270ab235db623d6a4a97ea93c41dd1) The ransom page looks looks like the following image.
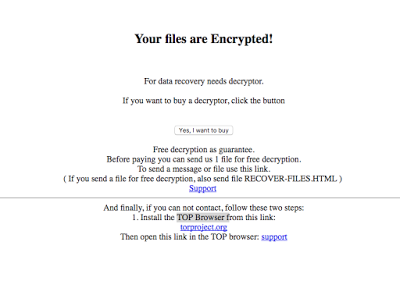 |
| Ransom Request Rendered File |
I will call this Ransomware the “TOPransom” since the funny and evident mistake the attacker made in writing the ransom request file in where he suggested to download the TOP Browser rather then the TOR Browser ![</div>
</td>
</tr>
</table>
<h3>评论</h3>
<div id=]() 暂无
暂无
发表评论
热度(1109)

