| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
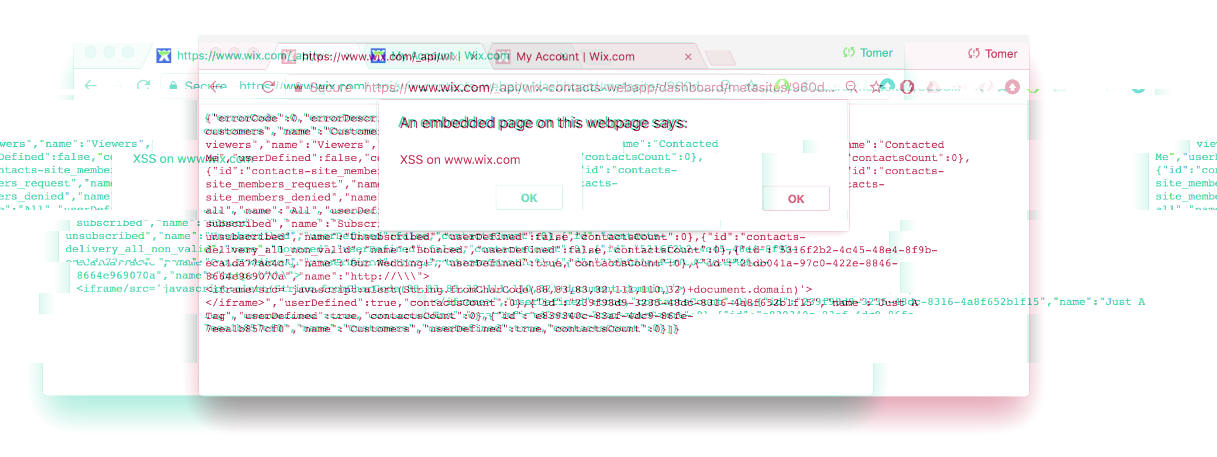
Website-building service Wix.com was the subject of a massive cyber-attack in April 2016 when a botnet of rogue Chrome extensions was creating Wix websites to spread itself to new users.
The attack went unreported at the time, but last week, speaking at the Black Hat and DEF CON security conferences that took place in Las Vegas, Tomer Cohen, lead for Wix's security team, revealed more details about the incident.
Botnet authors attacked Wix first, then Google Drive
According to Cohen's account, tens of thousands of users were infected with a rogue Chrome extension that downloaded malicious JavaScript code to create new Wix accounts, publish a free website, and spread a link to this new Wix site via the infected victim's Facebook Messenger service.
Victims who received the private message were lured to the malicious Wix pages where they'd be invited to install a copy of the rogue Chrome extension.
The botnet was clearly in an incipient stage and its authors were only interested in boosting numbers, but at one point the spam would have lured users to more dangerous sites. This didn't happen because Cohen and his team detected the botnet's actions and blocked any attempts to leverage their infrastructure any further.
Two months later, the same botnet authors launched a new attack, but this time they used Google Drive to host malicious websites instead of Wix. This second attack, which took place in June 2016, was observed and documented by Kaspersky Lab researchers in a report.
More trouble to come
In his Black Hat and DEF CON presentations [1, 2], Cohen argued that such attacks will intensify in the future because rogue Chrome extensions provide an easy avenue to execute code on any website.
Cohen also debates that attackers don't necessarily need to create and upload their own extensions to the Chrome Web Store — such as the 2016 threat actor — but they can take advantage of security flaws in existing Chrome extensions.
The expert points out to an XSS (cross-site scripting) flaw that affected the Chrome extension which Adobe shoved down users' throats during an Acrobat update this winter, or another XSS flaw in AVG Web TuneUp, a Chrome extension that the AVG antivirus forcibly installed on all customers' PCs.
"Such [an XSS] flaw leads to full and permanent control over the victim's browser, turning the extension into zombie," Cohen explains in his presentation, which also contains proof of concept code on how to take three benign Chrome extensions and weaponize them to carry out malicious operations.

