| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |

AhnLab, a South Korea-based cyber-security firm, has released today a vaccine app that blocks the GandCrab ransomware from taking root and encrypting users' files.
This vaccine app works by creating a special file on users' computers that the GandCrab ransomware checks before encrypting user data.
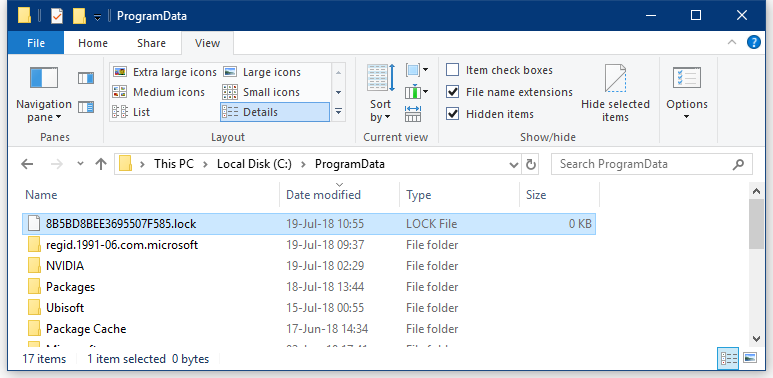
Win 7, 8, 10: C:\ProgramData
Vaccine app tricks GandCrab ransomware
The hexadecimal ID is generated based on the computer's volume information of the root drive and a custom Salsa20 algorithm and is unique per user.
GandCrab creates this file to know if a computer has already been infected and prevent users from running the ransomware executable twice and double-encrypting and permanently destroying their data.
The AhnLab vaccine app can create this file in advance, before a user might get infected, hence tricking the ransomware into thinking it has already locked the victim's data.
Only works with GandCrab v4.1.2
Unfortunately, this vaccine app works only with the latest version of the GandCrab ransomware, version 4.1.2, the version that's currently distributed in the wild since this week, July 17.
The addition of this .lock file mechanism appears to have been added with the release of GandCrab v4, at the start of July, as detailed in these Fortinet and Morphisec reports.
While the current vaccine app blocks GandCrab v4.1.2, it may also be possible to backport the app and prevent older GandCrab v4 versions from infecting users as well.
This is because older GandCrab versions used even a simpler method of creating the .lock file. "Before it was just plain shifted-right volume serial number," the Fortinet team said on Twitter.
Users can download AhnLab's GandCrab 4.1.2 vaccine app from here [or here].
No SMB spreader
The GandCrab ransomware has slowly become the most widespread ransomware strain in use today. Version 4.1.x, in particular, has recently grabbed some headlines.
Back at the start of the month, a security researchers spotted that GandCrab added support for the EternalBlue NSA exploit, suggesting the ransomware could use it to spread to other nearby computers on the same network via the SMB protocol. But in a later report, Fortinet said this self-propagation routine doesn't seem to be used by the ransomware at all.
#Gandcrab new internal version 4.1.2, with a new msg mixed in the code:
[+] #fortinet & #ahnlab, mutex is also kill-switch not only lockfile ;)
MD5: 0301296543c91492d49847ae636857a4 (unpacked) pic.twitter.com/T8KRtSrgd6— Marcelo Rivero (@MarceloRivero) July 17, 2018
原文链接:https://www.bleepingcomputer.com/news/security/vaccine-available-for-gandcrab-ransomware-v412/

