| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
Cofense Intelligence™ has uncovered a recent AZORult stealer phishing campaign that delivers the malware via malicious attachments. Older versions of AZORult stealer have been delivered via intermediary loaders, typically Seamless or Rammnit malware. In this latest campaign, the attached documents use multiple techniques to download and execute an AZORult sample, indicating a shift by the threat actors behind the campaign to adopt more evasive delivery techniques. [出自:jiwo.org]
This shift in the transportation mechanism is important because the malware’s successful delivery is no longer contingent on a first-stage infection of the targeted machine by different malware. AZORult can simply rely on tried-and-tested mechanisms such as vulnerabilities or macros to download and execute the malicious payload.
AZORult has been observed using email-attached documents that exploit one of multiple, common vulnerabilities to download and execute the payload. In most cases, the document reaches out to an external network location to pull down the binary to be executed. The payload is typically an MSI (Microsoft Installer) and a little over 2 MB in size. Cofense Intelligence™ has found that AZORult Version 3 is most often delivered via malicious Office Macros or Dynamic Data Exchange (DDE) abuse—both of which are often-abused features that allow the running of arbitrary code—when delivered as a first payload via attachment.
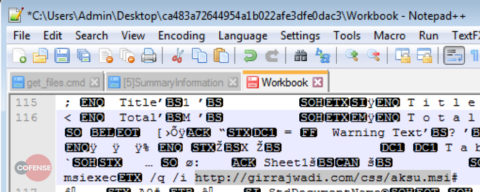
Figure 1: Office Macro URL Payload
A More Effective Rapid Compromise
By removing any reliance on intermediary payloads and adding evasion features, AZORult can more efficiently and effectively compromise its targets. Once an attachment is opened and AZORult is downloaded and executed, it only communicates twice with its C2 to complete its mission before deleting its own binary. This is a big difference from other information stealers that are designed to maintain persistence for ongoing information stealing. This tactic also enables AZORult to evade network logging systems that are not tuned for such little communication or rely on event sequences that involve many external connections. Further, the self-deleting function makes it harder for digital forensics and incident response teams to investigate. Without proper logging on the endpoint and the network, it would be difficult to know what data the malware had successfully exfiltrated or, indeed, that the malware had ever been on the system. This reliance on stealth and evasion is extremely derivative of classic banking trojans, and breaks the modern status quo.
Version 3 of AZORult has been given upgraded capabilities to cope with the improved security of web browsers. This newest version includes improvements such as:
- Uses many commonplace anti-analysis techniques, such as anti-debugging, and environment integration that is indicative of anti-VM and anti-sandbox behaviors.
- Includes certain notable updates to its codebase, which saw the addition of features such as taking screenshots and harvesting Skype, Jabber, and other chat program logs and chat histories.
- Supports blockchain-based DNS infrastructure – such as those supporting the .bit and .coin TLDs – which can make attacker-controlled infrastructure far more robust than standard DNS-based communication.
- encrypted communication between the infected endpoint and the management panel for further obfuscation.
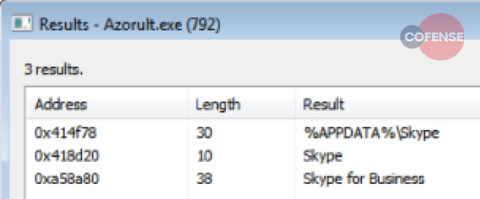
Figure 2: Shows memory strings for Skype
Features of AZORult
All versions of AZORult can collect cookies, saved passwords, credit card information, and auto-complete data from most major browsers. AZORult targets Bitcoin wallet information, FTP, email, and XMPP client credentials, and can be configured to grab files from Desktop with specified extensions; the latter being a somewhat unusual feature amongst information stealers.
Upon execution, AZORult will spawn and hollow out a legitimate Windows process, injecting into it code decrypted from its own body. After passing control to the injected code and terminating the original process, AZORult will gather and send four pieces of information to its C2: cryptographic machine generated GUID, OS information, user name, and machine name. This information serves as a unique identifier for the infected host. Upon retrieving further instructions from the C2, the sample will retrieve the public IP address of the infected machine with a call to hxxp://ip-api[.]com/json. Employing a novel approach to data obfuscation, AZORult will store snippets of harvested data in different text files, located in completely different folder structures throughout the system. Figure 3 details the various text filenames used by AZORult.
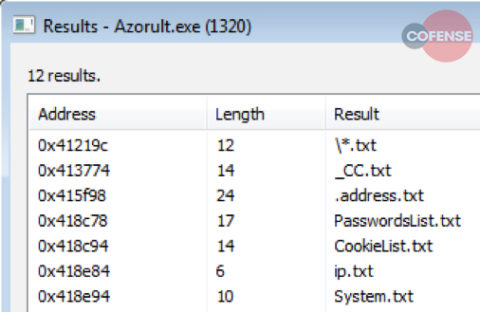
Figure 3: The text file names used to store various pieces of harvested data
Finally, AZORult will delete its original binary by executing a simple command line function.
This newest version indicates that the actors distributing AZORult are investing and improving its delivery mechanism. It is entirely possible that they will look to exploit other known vulnerabilities to deliver the malware, such as CVE-2017-11882, CVE-2017-0199, and CVE-2017-8750.
As malicious actors find new ways to more effectively deliver malware via phishing, it is critical to remain informed on emerging tactics, techniques, and procedures. And by ensuring that document-related patches are applied and Anti-Virus signatures and heuristics are tracked, you can take important steps to provide layered protections against this type of phishing campaign.
For a look back and look ahead at malware and phishing trends, view the 2017 Cofense Malware Review.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.
Related IOCs
hxxp://kosovo.duckdns[.]org/file/index.php
Kosovo[.]duckdns[.]org
hxxp://aksuperstorecom/fh8nzhme/gate.php
aksuperstore[.]com
au3_exe.exe|5829b77898d5acff0b0fbd87deb6b9cb
cartwheels.dll|48a801a908d44f1770d19f5569663f98
chrom.exe|5829b77898d5acff0b0fbd87deb6b9cb
Reveille.cab|305c699a84ad3fe04ca083ad499d32b3
FWLosDEdtZ.exe|05763c6632fcaaad57ba632788aa5a34
https://cofense.com/azorult-malware-finds-new-ride-recent-stealer-phishing-campaign/

