| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
A wide variety of threat actors began distributing HawkEye malware through high-volume email campaigns after it became available for purchase via a public-facing website. The actors behind the phishing campaigns typically used email themes based on current events and media reports that would pique user interests, with the “Subject” line typically containing something about recent news. Although HawkEye malware has several different capabilities, it is most often associated with credential theft.
In the middle of June, we observed a phishing campaign involving the distribution HawkEye malware. The threat actors behind this campaign are not targeting any specific group of industries or any specific region.
Infection Vector & Execution
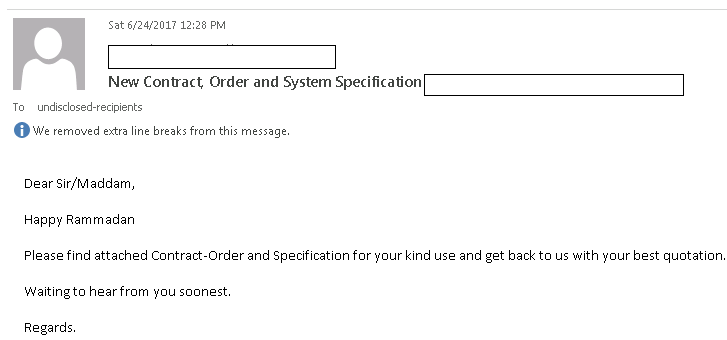
Figure 1 shows a sample phishing email used by HawkEye operators in this latest campaign. The message is designed to entice recipients to open the attachment. In this most recent campaign, the phishing email contained a DOCX attachment, and the attackers named the document appropriately so the recipient believed it involved a recent transaction or invoice.
 [出自:jiwo.org]
[出自:jiwo.org]
Figure 1: Sample phishing email
As seen in Figure 2, the deployment of the malware has several stages of execution, including the following:
- Phishing email containing a malicious DOCX file received by victim.
- DOCX file uses an OLE object, which contains an embedded Microsoft Intermediate Language (MSIL) executable. The MSIL file, or HawkEye malware, is dropped into the %temp% folder. The malware has an encrypted resource section, which contains additional payloads such as a password extraction tool and a decoy PDF document.
- On execution, HawkEye drops copies itself to the %AppData% folder with a random file name.
- The decoy PDF file is launched from the %temp% location.
- An XML file is created in the %temp% folder with a random file name. This XML file contains configuration details for scheduling a Windows task to execute during the user login process.
- For the sample analyzed, the malware is injected into VBC.exe (a Visual Basic Command Line Compiler). The injected code has data stealing capabilities and is designed to extract passwords from email clients and web browsers.

Figure 2: Infection Vector and Execution
Initial Payload: DOCX File
In the observed campaign, the actors used an embedded OLE object to deliver the payload to the victim’s machine. The malicious payload, HawkEye, is embedded in the DOCX file and dropped in the %temp% folder after the victim double-clicks on the object (Figure 3).

Figure 3: Embedded OLE Object
HawkEye Analysis
The HawkEye malware is primarily used for credential theft and is often combined with additional tools to extract passwords from email and web browser applications. These additional tools are contained in an encrypted resource section of the binary.
The HawkEye malware is capable of the following:
- Email password stealing
- Web browser password stealing
- Keylogging and taking screenshots
- Bitcoin wallet theft
- USB propagation
- Internet download manager stealing
- JDownloader password stealing
- Anti-virus checking
- Firewall checking
After initial checks and system enumeration, HawkEye sends the following data to the command and control (C2) server:
- Server Name
- Keylogger Enabled
- Clipboard-Logger Enabled
- Stealers Enabled
- Local Date and Time
- Installed Language
- Operating System
- Internal IP Address
- External IP Address
- Installed Anti-Virus
- Installed Firewall
USB Propagation and Bitcoin Wallet Theft
Along with its ability to steal sensitive information, HawkEye is capable of spreading through USB or removeable drives and can also steal Bitcoin wallets, as seen in Figure 4.

Figure 4 : USB spreading and Bitcoin Stealing
Encrypted Resource Section
The HawkEye malware in this campaign contained encrypted resources sections, which add functionality that enables the attackers to exfiltrate more data. FireEye observed the same pattern in previous HawkEye campaigns. The encrypted data is decrypted at run time and then injected in to the target process, vbc.exe. The encryption logic used is a custom algorithm and varies with the campaign. Figure 5 shows an example of the custom encryption algorithm.
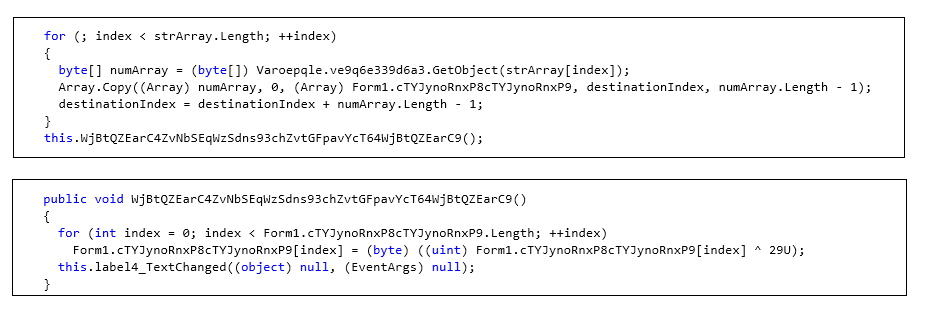
Figure 5: Custom decryption routine
After decrypting the resource section, the following files can be extracted:
- Decoy pdf file.
-
<Random_Name>.XML
- Contains configuration data for a Windows task creation
- CMemoryExecute.dll
- WebBrowserPassView.exe
- MailPV.exe
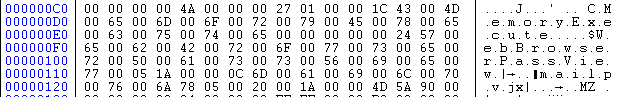
Figure 6: Components of malware
Task Scheduler – Persistence Mechanism
The payload uses the Windows task scheduling feature for its persistance mechanism on the victim’s computer. It schedules a task to execute on user login. The configuration data shown in Figure 7 is used to schedule the task.
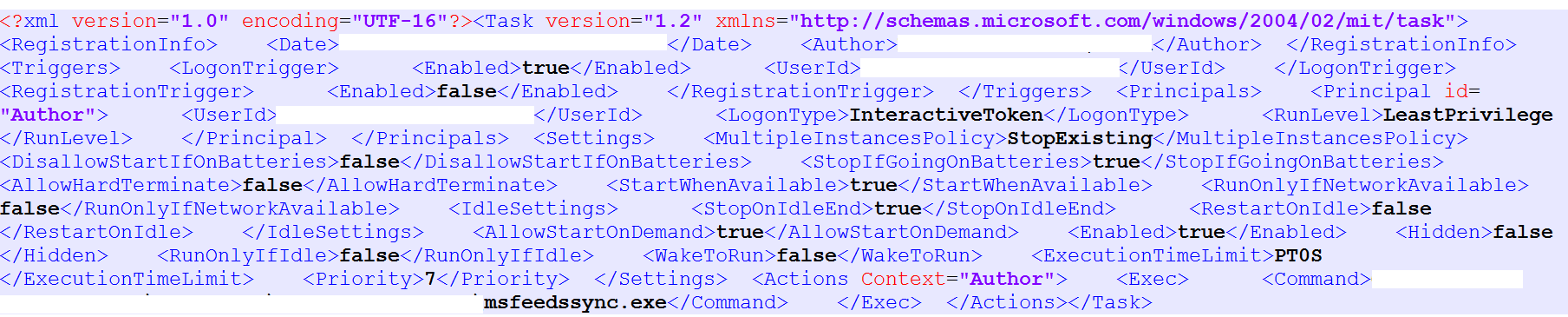
Figure 7: Task Scheduler.xml
CMemoryExecute.dll
CMemoryExecute.dll is responsible for running a .NET executable capable of using the Windows Native API to inject MailPV.exe and WebBrowserPassView.dll into VBC.exe, which the Visual Basic Command Line Compiler. MailPV and WebBrowserPassView are used in order to extract credentials from the list of email and web browser clients noted in the following section.
WebBrowserPassView
WebBrowserPassView.dll, extracted from the resource section, is a password recovery tool that extracts passwords stored in the following web browsers:
- Internet Explorer (Version 4.0 – 11.0)
- Mozilla Firefox (All Versions)
- Google Chrome
- Safari
- Opera
The extracted passwords are stored in a created text file: “%temp%\holderwb.txt”
MailPV
The MailPV.exe file is password recovery tool that extracts password for following email clients:
- Outlook Express
- IncrediMail
- Eudora
- Group Mail Free
- MS Outlook
- MS Outlook 2002/2003/2007/2010
- Gmail
- Hotmail/MSN
- Yahoo! Mail
- Netscape Mail
- Thunderbird
- Google Desktop
- Windows Mail
- Windows Live Mail
- Outlook 2013
The extracted passwords are stored in a created text file: “%temp%\holdermail.txt”
Command and Control Communications
The first C2 traffic observed is the malware’s check to get the external IP address of the infected machine. Figure 8 shows an example of the external IP address query.
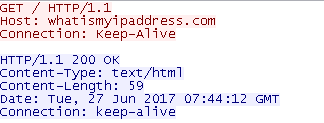
Figure 8 : External IP Address Query
As noted, the malware sends gathered system information and security program data to the C2 server after the external IP address is known. HawkEye can be configured to send this information through multiple methods, including via email or FTP.
In addition to the system data, the malware will upload any collected credentials from email and web browser applications. To do this, the malware will validate that holdermail.txt and holderweb.txt exist and send the data to the C2 server. After the data is exfiltrated, the TXT files are deleted from the victim’s machine.
In this campaign, the HawkEye payload was configured to upload the data via email. Once the extracted data is received by the C2 server, the server sends emails to the threat actors behind the campaign to notify them that new stolen information is available. Figure 9 shows some of the email templates used in this campaign and Figure 10 shows the SMTP traffic on the network.
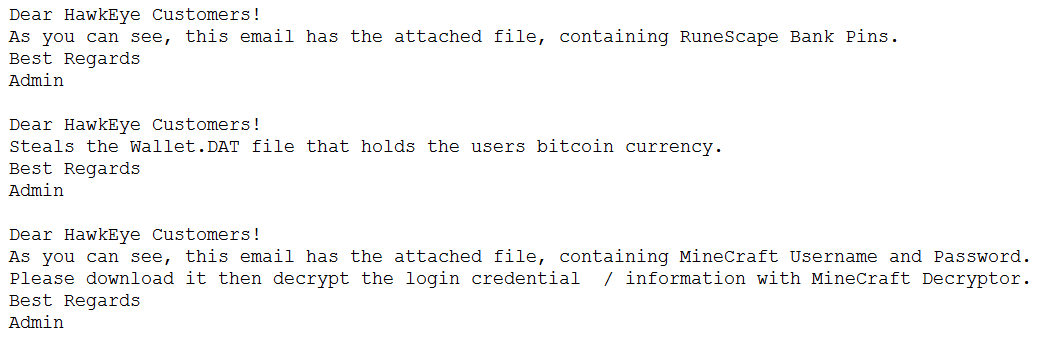
Figure 9: Email notification to HawkEye Customers
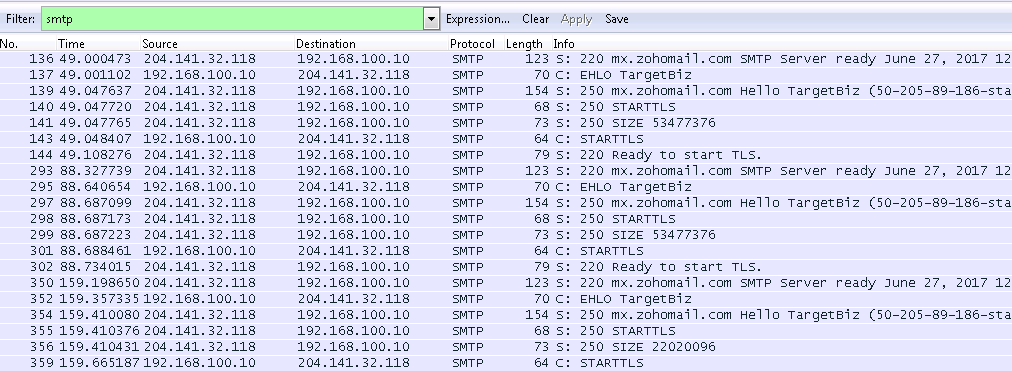
Figure 10: SMTP Handshake
HawkEye User Base
HawkEye is a versatile Trojan used by diverse actors for multiple purposes. The malware has been sold through a public-facing website, which has allowed many different operators to use it. As is often the case with commercial Trojans, HawkEye offers a variety of functions for stealing stored data, grabbing form data, self-spreading, and performing other functions. Consequently, HawkEye may facilitate a number of different exploitative operations in compromised environments, and can be used by actors with a wide range of motivations. We have seen different HawkEye campaigns infecting organizations across many sectors globally, and stealing user credentials for diverse online services. This particular campaign represents one segment of the numerous HawkEye activity sets.
Some notable threat operations where we have previously reported HawkEye use include business email compromise campaigns, phishing against Middle Eastern organizations, and prolific spam operations (get an iSIGHT intelligence subscription to learn more about these campaigns).
Conclusion
Based on previous observations, the phishing and lure techniques used in these recent HawkEye campaigns have remained consistent, as have the HawkEye binaries and associated payloads. However, the attackers have altered the initial delivery method to use an embedded OLE object, as opposed to past methods such as a macro embedded in a Word document. The threat landscape is continiously evolving, and we expect to see more new tricks and tactics being used by the actors using this malware family.
FireEye Multi Vector Execution (MVX) engine is able to recognize and block this threat.

