| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
安全研究人员发现一个来自中国的、修改计算机主引导记录(MBR)的锁屏勒索软件DexLocker。根据研究人员的分析,可以输入ssssss密码访问计算机,如果密码不起作用则可以通过引导至Windows故障恢复控制台,使用以下命令恢复主引导记录:bootrec /RebuildBcd;bootrec /fixMbr;bootrec /fixboot。执行后重启机器即可访问计算机。 [出自:jiwo.org]
A
new Chinese MBRLocker called DexLocker has been discovered that asks for 30 Yuan to get access to a computer. First discovered by security researcher JAMESWT, this ransomware will modify the master boot record of the victim's computer so that it shows a ransom note before Windows starts.
Unfortunately, I was not able to get this sample to run, so I have no first hand analysis of this ransomware. The AnyRun video posted by JAMESWT, though, shows that once you install the ransomware, it immediately reboots the computer and the victim is greeted with an ascii skull and a message to send 30 yuan
to the 2055965068 qq address in order to get access to their computer again.
Microsoft's Windows Defender Security Team saw Jame's tweet and tweeted that they have labeled the MBRLocker as Ransom:DOS/Dexcrypt.A and that it can be detected by Windows Defender.
ICYMI: New #ransomware writes code to the Master Boot Record (MBR) and immediately restarts computer to show a note that asks for 30 yuan as ransom. Windows Defender AV detects and blocks this ransomware as Ransom:Win32/Dexcrypt and its MBR-writing code as Ransom:DOS/Dexcrypt.A. https://t.co/wpD0wJeSIu
According to kangxiaopao, you can enter the ssssss password to gain access. If this password does not work and it does only replace the MBR, it can be fixed by booting up into the Windows Recovery Console and restoring the Master Boot Record using the following commands:
Once you enter these commands, you can reboot and get access again to Windows again.
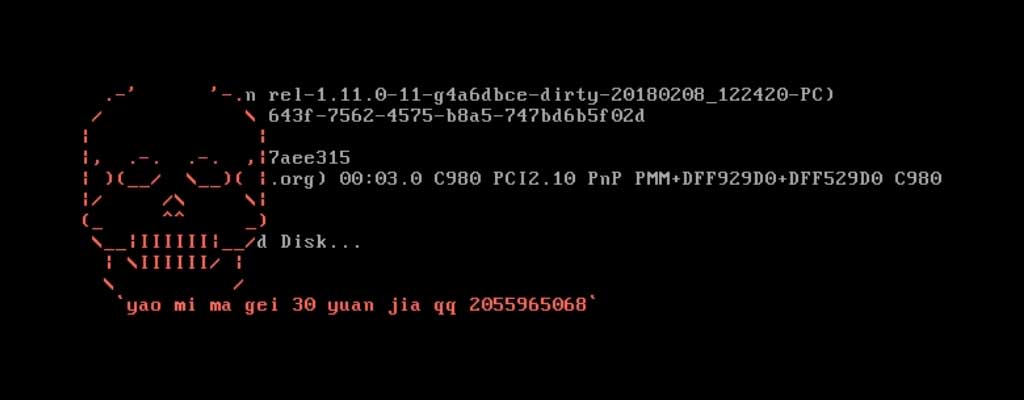 DexCrypt Lock Screen
DexCrypt Lock Screen
bootrec /RebuildBcd
bootrec /fixMbr
bootrec /fixboot
IOCs
Hashes:
dfc56a704b5e031f3b0d2d0ea1d06f9157758ad950483b44ac4b77d33293cb38
Ransom Note:
.-' '-.
/ \
| |
|, .-. .-. ,|
| )(__/ \__)( |
|/ /\ \|
(_ ^^ _)
\__|IIIIII|__/
| \IIIIII/ |
\ /
`yao mi ma gei 30 yuan jia qq 2055965068`

