| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
We’ve uncovered a new exploit kit in the wild through a malvertising campaign we’ve dubbed “ProMediads”. We call this new exploit kit Sundown-Pirate, as it’s indeed a bootleg of its precursors and actually named so by its back panel.
ProMediads has been active as early as 2016, employing Rig and Sundown exploit kits to deliver malware. Its activities dropped off in mid-February this year, but suddenly welled on June 16 via Rig. However, we noticed that ProMediads eschewed Rig in favor of Sundown-Pirate on June 25.
It’s worth noting that Sundown-Pirate is only employed by ProMediads so far. This could mean that it’s yet another private exploit kit, like the similarly styled GreenFlash Sundown exploit kit that was exclusively used by the ShadowGate campaign.
Our analysis and monitoring revealed that Sundown-Pirate borrowed code from predecessors Hunter and Terror exploit kits. Its JavaScript obfuscation, however, is similar to Sundown’s. This mishmash of scrounged capabilities is what made us think it’s new.
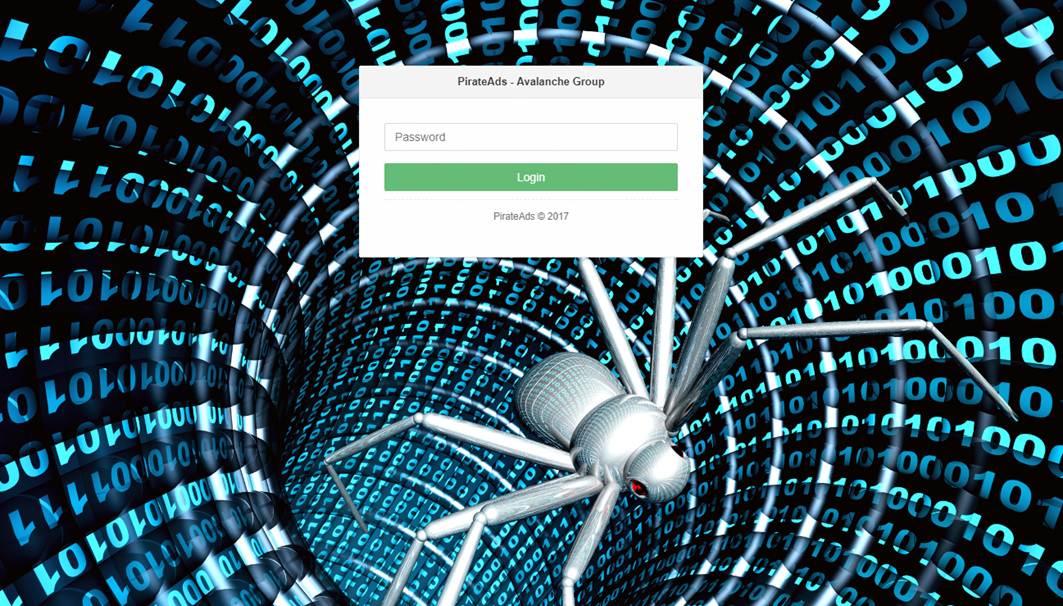
ProMediads’ backend panel further cements its name. Together with researcher kafeine, we saw that ProMediads’ panel has a login prompt with “PirateAds – Avalanche Group” on it.
 [出自:jiwo.org]
[出自:jiwo.org]
Figure 1: ProMediads’ backend panel

Figure 2: Example of ProMediads’ malvertisement
From botnet/info stealer and PoS malware to ransomware
ProMediads diverted would-be victims to Sundown-Pirate that then delivered various malware to the affected machine. On June 25, for instance, Sundown-Pirate dropped the Trojan SmokeLoader (TROJ_SMOKELOAD.A), which installed the information-stealing botnet infector Zyklon (TSPY_ZYKLON.C).
By July 12, the exploit kit’s payload changed to point-of-sale (PoS) malware LockPOS. It’s a knownconspirator of Flokibot’s campaigns, another threat that targets point-of-sale/credit card data.
We also found that LockPOS delivered via Sundown-Pirate had cryptocurrency-mining softwareCPUMiner-Multi as an additional payload. We don’t think CPUMiner specifically targets PoS systems; it merely uses LockPOS as a vector or conduit to zombify the infected system for cryptocurrency mining. LockPOS will serve as a hidden backdoor polling its C&C server for additional commands from the bot master.
On July 13, Sundown-Pirate started dropping Stampado ransomware (RANSOM_STAMPADO.K).

Figure 3: Sundown-Pirate delivering LockPOS on July 12, 2017
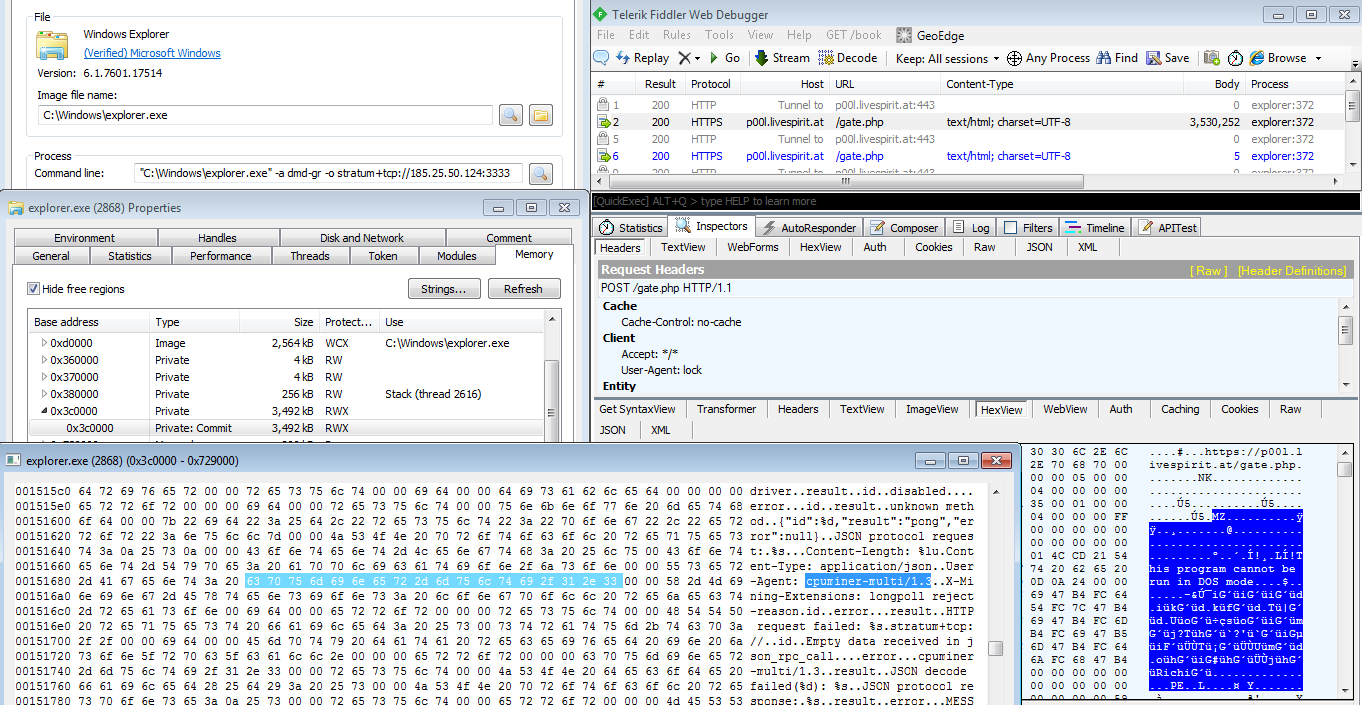
Figure 4. LockPOS downloads CPUMiner and injects into an explorer process
ProMediads, SmokeLoader, and Flokibot/LockPOS: No Prey, No Pay?
Since 2016, we’ve seen ProMediads deliver a specific SmokeLoader botnet through exploit kits, the latter of which is considered to have a close relationship with ProMediads’ operators. Recently though, the botnet started deploying the same LockPOS variant that Sundown-Pirate drops.
kafeine shared that in August 2016, ProMediads’ operators distributed Flokibot before it was sold in underground forums in September 2016. Both the Flokibot campaign and ProMediads currently distribute LockPOS. These connections appear to be influenced by relationships between these cybercriminals—at least as far as their malware are concerned.
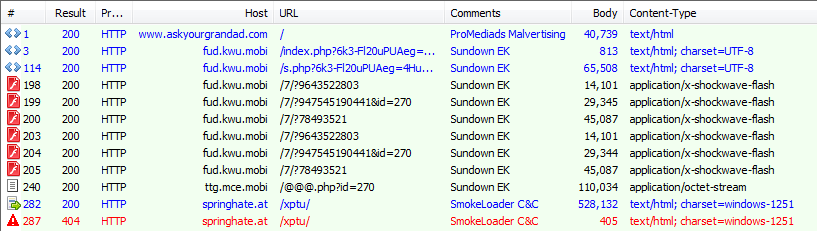
Figure 5. ProMediads delivering SmokeLoader on January 24, 2017

Figure 6. The SmokeLoader botnet installing LockPOS by mid-July, 2017
Old wine in new bottle?
Sundown-Pirate uses three Internet Explorer exploits and another one in Flash:
- CVE-2013-2551, patched in May 2013 via MS13-037
- CVE-2014-6332, patched in November 2014 via MS14-064
- CVE-2016-0189, patched in May 2016 via MS16-051
- CVE-2015-7645, patched by Adobe in October 2015 via APSA15-05
Fortunately, there is a silver lining. The more vulnerabilities are disclosed, the faster they can be patched. And these exploits are going to be less successful as users and business become more proactive and security-savvy. This has been demonstrated by the recent decline of exploit kits, especially the use of zero-days and relatively new vulnerabilities.
Additionally, these exploits won’t work on Chrome and Firefox browsers. Flash content on these browsers are disabled by default, but even if Flash is enabled, their security mechanisms can still deter malicious content—e.g., Firefox’s Web Application Program Interfaces (APIs) and Protected Mode, and Chrome’s Sandbox.
The plethora of malware Sundown-Pirate delivers, however, still makes it a credible threat. More than ever, exploit kits highlight the real-life significance of keeping systems updated. Systems and networks that remain vulnerable to security flaws (for which patches have long been available) give bad guys a bigger window of exposure to attack them.
Information security and IT/system administrators are also recommended to incorporate additional layers of security to their enterprise’s systems and networks. Firewalls, intrusion detection and prevention systems, virtual patching, URL categorization, and enforcing robust patch management policies are just some of the best practices against attacks that exploit vulnerabilities.
Trend Micro Solutions
Exploit kits take advantage of security flaws within system or software, which is why a multilayered approach to security is important—from the gateway, endpoints, networks, and servers. Trend Micro™ OfficeScan™ with XGen™ endpoint security has Vulnerability Protection that shields endpoints from identified and unknown vulnerability exploits even before patches are even deployed. Trend Micro’s endpoint solutions such as Trend Micro™ Smart Protection Suites, andWorry-Free™ Business Security protect end users and businesses from these threats by detecting and blocking malicious files and all related malicious URLs.
Indicators of Compromise (IoCs):
Domain/IP address related to Sundown-Pirate:
- 7wu93ksh29qpl70nas0[.]win
- 178[.]159[.]36[.]91
SmokeLoader C&C Domains:
- livespirit[.]at
- springhate[.]at
LockPOS C&C Domain:
- p00l[.]livespirit[.]at
Domain related to ProMediads:
- multiplus[.]site
Related Hashes (SHA-256):
- 4199d766cee6014fd7a9a987b4ccea3f8d0ed0fba808de08b76cda71e40886b5 (TROJ_SMOKELOAD.A)
- f569172166a19c06b3efa1f75d02b143539cd63a53d67bc066d28f8fd553ba8e (TSPY_ZYKLON.C)
- 3fa54156ae496a40298668911e243c3b7896e42fe2f83bc68e96ccf0c6d59e72 (BKDR_LOCKPOS.A)
- 931092a92ffaa492586495db9ab62dd011ce2b6286e31e322496f72687c2b4ef (HKTL_COINMINER)
- 109e89148945d792620f4fc4f75e6a1901ba96cc017ffd6b3b67429d84e29a3c (Ransom_STAMPADO.K)

