| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
ID-Ransomware的安全研究人员发现勒索软件勒索软件的变种,新版本会将.cobra扩展名附加到加密文件中。该勒索软件可以对网络驱动器加密,暂时不能解密该勒索软件。 [出自:jiwo.org]
This week, ID-Ransomware's Michael Gillespie noticed what appeared to be a new variant of the Crysis/Dharma Ransomware uploaded to his ID-Ransomware site. Jakub Kroustek then discovered a sample to confirm that it was indeed a new Crysis variant. This new version will append the .cobra extension to encrypted files. It is not known exactly how this variant is being distributed, but in the past Crysis was typically spread by hacking into Remote Desktop Services and manually installing the ransomware.
When this Cobra ransomware variant is installed, it will scan a
computer for data files and encrypt them. When encrypting a file it will append an extension in the format of .id-[id].[email].cobra. For example, a file called test.jpg would be encrypted and renamed to test.jpg.id-BCBEF350.[cranbery@colorendgrace.com].cobra.
It should be noted that this ransomware will encrypt mapped network drives and unmapped network shares. So it is important to make sure your network's shares are locked down so that only those who actually need access have permission.
You can see an example of a folder encrypted by the Cobra Ransomware variant below.
When this variant encrypts a computer, it will also delete all of the shadow volume copes on the machine so that they can not be used to recover unencrypted files. It deletes them by running the vssadmin delete shadows /all /quiet command.
This ransomware will also create two different ransom notes on the infected the computer. One is theinfo.hta file, which is launched by an autorun when a user logs into the computer.
The other note is called Files encrypted!!.txt and can be found on the desktop.
Both of these ransom notes contain instructions to contact cranbery@colorendgrace.com in order to get payment instructions.
Finally, the ransomware will configure itself to automatically start when you login to Windows. This allows it to encrypt new files that are created since it was last executed.
Unfortunately, at this time it is not possible to decrypt .cobra files encrypted by the Crysis Ransomware for free.
The only way to recover encrypted files is via a backup, or if you are incredibly lucky, through Shadow Volume Copies. Though Crysis does attempt to remove Shadow Volume Copies, in rare cases ransomware infections fail to do so for whatever reason. Due to this, if you do not have a viable backup, I always suggest people try as a last resort to restore encrypted files from Shadow Volume Copies as well.
For those who wish to discuss the Crysis ransomware or need support, you can use our dedicated Crysis Ransomware Help & Support Topic.
In order to protect yourself from Crysis, or from any ransomware, it is important that you use good computing habits and security software. First and foremost, you should always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
You should also have security software that contains behavioral detections such as Emsisoft Anti-Malware, Malwarebytes, or HitmanPro.Alert.
Last, but not least, make sure you practice the following good online security habits, which in many cases are the most important steps of all:
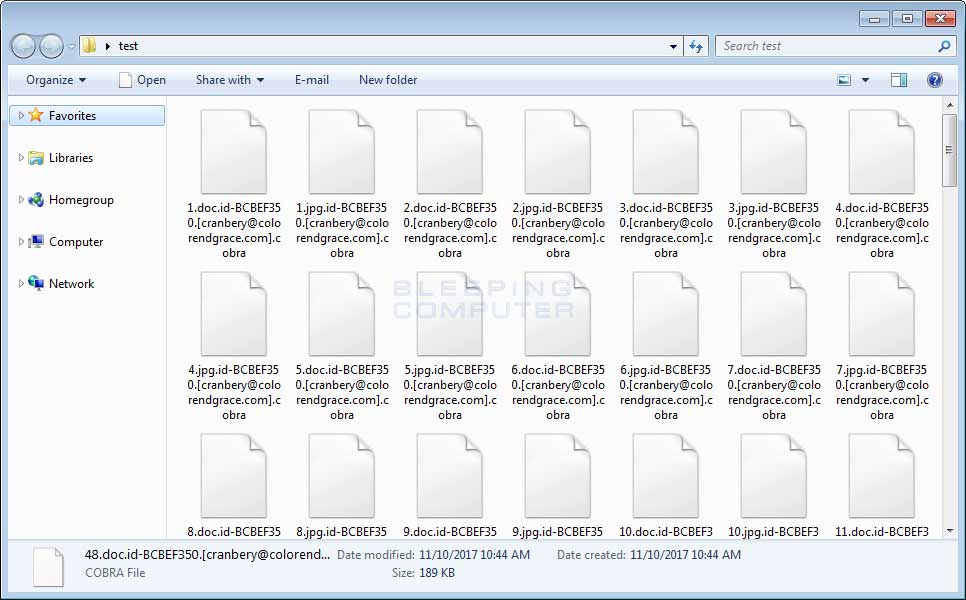 Files encrypted with the Crysis Cobra Ransomware Variant
Files encrypted with the Crysis Cobra Ransomware Variant
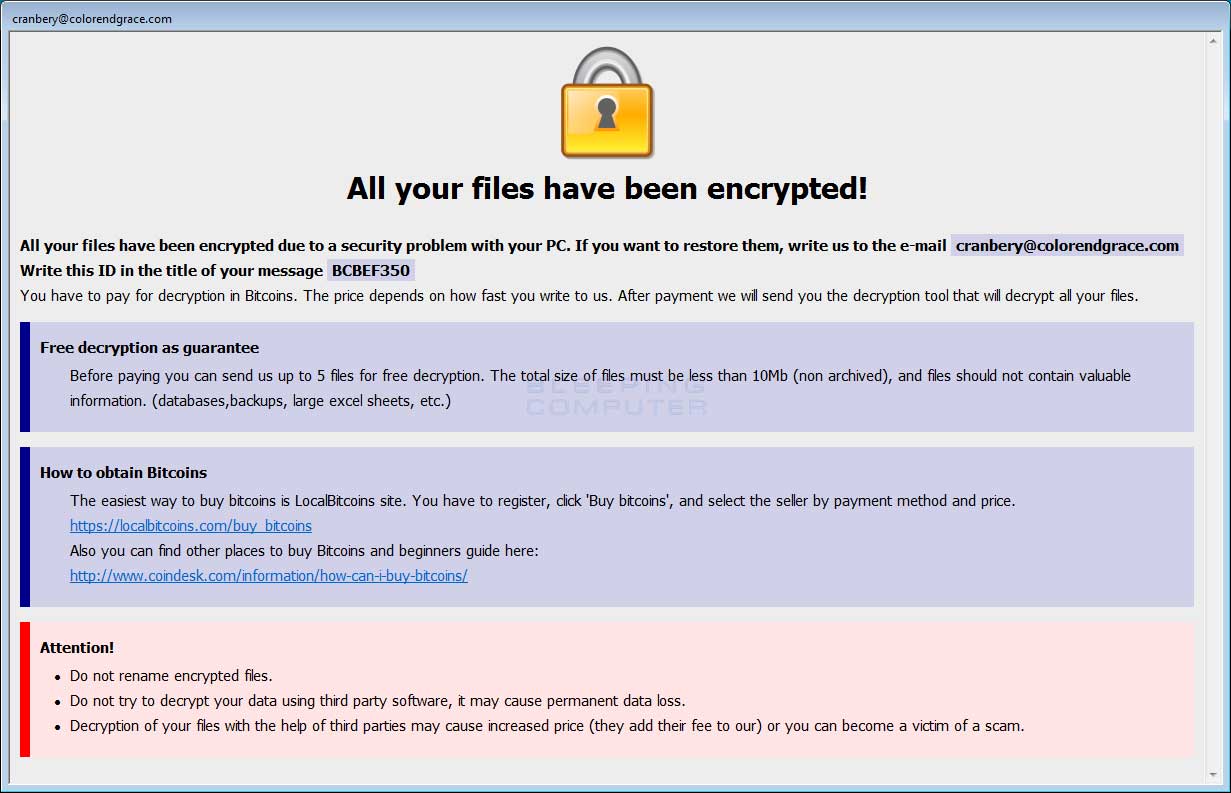 Crysis Cobra Ransom Note
Crysis Cobra Ransom Note
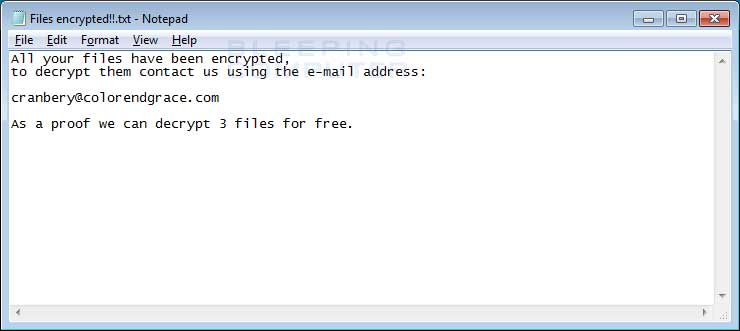 FILES Encrypted Ransom Note
FILES Encrypted Ransom Note
It is not possible to decrypt the Crysis Cobra Ransomware Variant
How to protect yourself from the Crysis Ransomware

