| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
A seven-year old vulnerability in Samba—an open-source implementation of the SMB protocol used by Windows for file and printer sharing—was patched last May but continues to be exploited. According to a security advisory released by the company, the vulnerability allows a malicious actor to upload a shared library to a writable share, causing the server to load and execute it. If leveraged successfully, an attacker could open a command shell in a vulnerable device and take control of it. It affects all versions of Samba since 3.5.0.
The vulnerability (CVE-2017-7494) was dubbed SambaCry because of passing similarities to the SMB vulnerability exploited by WannaCry. It was detected June 2017 when the cryptocurrency miner EternalMiner/CPUMiner used it to compromise Linux machines and mine Monero. The previous sample we obtained revealed that SambaCry was only used to target servers, and the payload was simply the cryptocurrency mining malware. Now, recent data shows that attackers are leveraging SambaCry for other purposes.
This more recent malware is detected as ELF_SHELLBIND.A and was found on July 3. Similar to the previous reports of SambaCry being used in the wild, it also opens a command shell on the target system. But ELF_SHELLBIND.A has marked differences that separate it from the earlier malware leveraging SambaCry. For one, it targets internet of things (IoT) devices—particularly the Network Attached Storage (NAS) devices favored by small to medium businesses. ELF_SHELLBIND also targets different architectures, such as MIPS, ARM, and PowerPC. This is the first time we’ve seen SambaCry being exploited without the cryptocurrency miner as a payload.
Malware analysis
It is quite easy to find devices that use Samba in Shodan: searching for port 445 with a ‘samba’ string will turn up a viable IP list. An attacker would then simply need to create a tool that can automatically write malicious files to every IP address on the list. Once they write the files into the public folders, the devices with the SambaCry vulnerability could become ELF_SHELLBIND.A victims.
As we see in Figure 1 below, ELF_SHELLBIND.A typically arrives in public folders as a malicious shared object (.SO) file, which is similar to the previous miner malware’s routine of exploiting the SambaCry vulnerability. We can also see that it attempts to exploit SambaCry because it is invoked via the Export function samba_init_module, which is how the vulnerable Samba server would load this library automatically.
After uploading the .SO file to the Samba public shared folder, the attacker needs to guess the absolute local filename and send an IPC request to trick the server into loading and running the locally-stored program file.
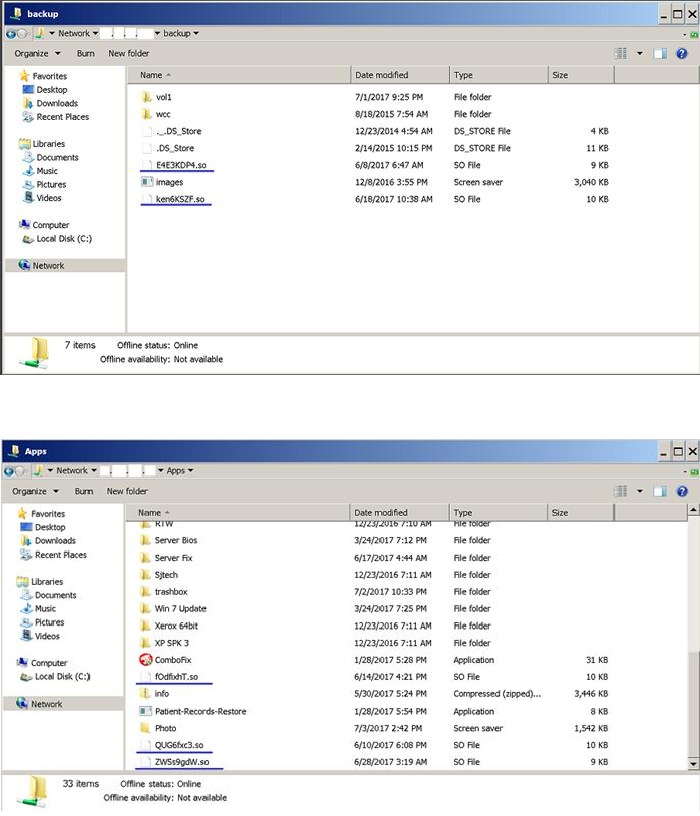
Figure 1. Samples of the malware files on a public shared folder
Once the malware is loaded via said Export function, it starts by calling the functionchange_to_root_user, which is required by the Samba daemon (specific to SMBv2) to run as root or as the EUID of the current user. The malware then detaches itself from whatever parent process it is running under (a Samba server process) and daemonizes its process (via the functiondetach_from_parent). This is followed by the malware sending what is known as a Knock message to what we assume is its Command and Control (C&C) server in East Africa “169[.]239[.]128[.]123” over TCP, port 80. The knock message simply consists of:
HEAD / HTTP/1.0
The server reads the response but never consumes it in any way. This socket is closed at this point. At this stage, the attacker has already obtained the system’s IP address.
The malware then deletes the chain rule that matches all accepted communications over TCP/61422 from the iptable, and adds it again so the firewall accepts all TCP communications over the said port. The malware then opens a TCP socket in listening mode over port 61422, accepting a connection from the attacker. Once the attacker connects to this socket, the malware sends the message:
Welc0me to shell[出自:jiwo.org]
Enter password:
The malware expects the attacker to enter the password:
Q8pGZFS7N1MObJHf
If the attacker responds with said password, the malware sends the message:
Access granted
If the response is not the correct password, it bails out.
Once the connection is successfully established and authentication is confirmed, then the attacker will have an open command shell in the infected systems where he can issue any number of system commands and essentially take control of the device. The malware executes whatever it receives over this socket (stdin, stdout, and stderr all redirected to the socket) using the system’s shell located at /bin/sh.
Conclusion and solutions
The OS patch has already been released for this vulnerability, which may limit the number of victims. Attackers also need to have writable access to a shared location in the target system to deliver the payload—another limiting factor that might stem the rate of infection.
Since this vulnerability was patched in May, users who regularly update have no issue. However, Unix or Linux based devices (which comprise most IoT devices) are harder to protect. If Samba is enabled and the manufacturers have not sent out patches, then the devices are vulnerable. Users should proactively update or consult with the specific manufacturers.
Trend Micro™ Deep Security™ and virtual patching protect endpoints from threats such as fileless infections and those that abuse unpatched vulnerabilities. User systems are protected from any threats that may target the SambaCry vulnerability via the following DPI rule:
- 1008420-Samba Shared Library Remote Code Execution Vulnerability (CVE-2017-7494)
Trend Micro™ Deep Discovery™ provides detection, in-depth analysis, and proactive response to attacks using exploits and other similar threats through specialized engines, custom sandboxing, and seamless correlation across the entire attack lifecycle, allowing it to detect these kinds of attacks even without any engine or pattern update. Deep Discovery Inspector protects customers from this threat via this DDI Rule:
- 3733 SHELLBIND – TCP (Request)
TippingPoint customers are protected under the filter:
- 29058: TCP: SambaShell Checkin
SHA256 for ELF_SHELLBIND.A:
c27594b1a1ecee6a62adbaee5b00bad8e3540fe98ff3bac17fef03e0ebd62914
516bafdede5e7a019a71028a7125f98190ee7ab71d03bc3041c9943324a78df5
11f47c90393082e7fdc4213d3b888ef8b7c121a86658077465b03bb7857bc540

