| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
Summary
 Axis M3004 security camera
Axis M3004 security camera
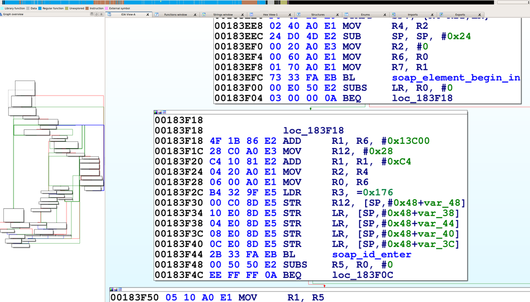
When we began a security analysis of remote configuration services last year, we had no idea it would lead us to uncover vulnerabilities that affect so many users. We have been studying the prevalence and nature of the vulnerabilities that arise in remote configuration services, so when we approached the M3004, we specifically sought out such a service. We began by enumerating all open ports and examined the code which handled incoming data. The service we found was wsd, a service that imports a third party library from gSOAP by Genivia. We discovered the vulnerability by using IDA Pro, a reverse engineering tool, to examine all code that wrote incoming data to stack buffers.
[出自:jiwo.org]
We reached the vulnerable code by sending a POST command to the ONVIF service available on port 80. We were able to observe the internals of the service and the results of our code by activating ssh through the webserver and then remotely debugging the service with gdbserver, which was already installed on the camera. After verifying the vulnerability by observing it crash at a value we set when the overflow overwrote the stored return pointer on the stack, our next challenge was to gain code execution.
Although there was no limit to how many bytes we could write to the stack, we could not execute code on it, and a filter required that all the values we sent be greater than 31. We used a technique called Return Oriented Programming (ROP) to write addresses to the stack to force the program to execute code snippets in libc so we could circumvent the non-executable stack. Through this technique, we allocated executable space, copied our shellcode to that space, and directed execution to it. Although the requirement that all the addresses we used needed to have values greater than 31 restricted us somewhat, we were still able to gain code execution.
Once we reached this step, we wrote shellcode, which again contained all values greater than 31, to open a port and allow a remote user to connect to a shell. At this point we had gained code execution by exploiting Devil's Ivy (CVE-2017-9765). Due to Axis's security settings, this exploit only grants access to a shell as an unprivileged user on the M3004. However, we were able to execute commands from the ONVIF specification that only a privileged user would normally be allowed. We were able to reset the camera to its factory defaults and take control of the camera, reboot it to prevent an operator from viewing the feed, and change network settings.
Read on for the full technical details or scroll to the bottom to see a video demonstration.
Access

Analysis
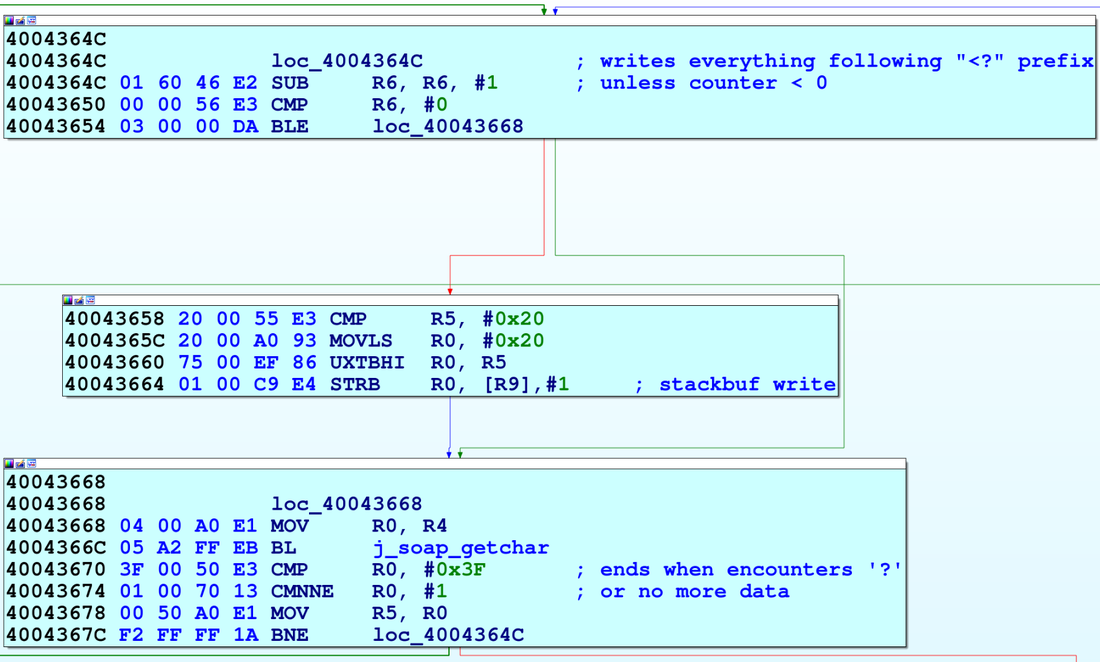
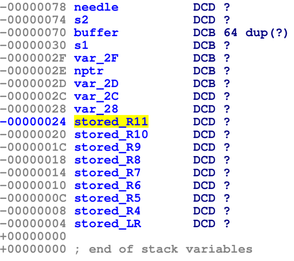 soap_get() stack
soap_get() stack
We reached this vulnerability by sending a POST command to “/onvif/device_service” on port 80, which was handed off from the webserver to the wsd service. To send 0x80000070 bytes, we generated a text file beginning with “POST /onvif/device_service” followed by a new line and “