| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
[出自:jiwo.org]
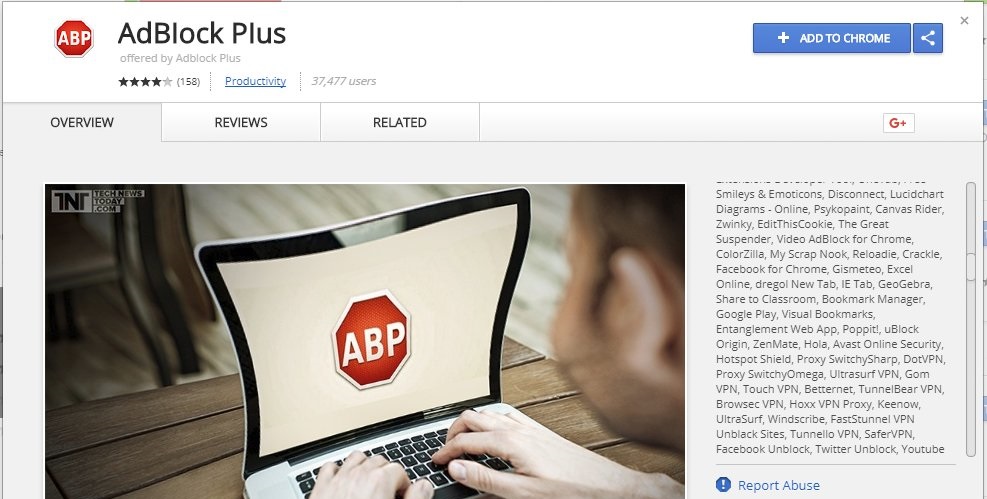
Google has removed a malicious extension from its Chrome Web Store that posed as the popular AdBlock Plus ad blocker but forcibly opened new tabs to show ads to users.
Discovered by a security researcher going by the pseudonym of SwiftOnSecurity, the extension [1, 2] had over 37,000 users at the time it was taken down late last night.
Fake Extension Page Had Obvious Issues
As the researcher points out in a Twitter tirade aimed at Google's staff, the problem is that Google allowed another developer to upload an extension using the same name as AdBlock Plus, a very popular ad blocker for Chrome.
"Google allows 37,000 Chrome users to be tricked with a fake extension by [a] fraudulent developer who clones popular name and spams keywords," the expert said. "Legitimate developers just have to sit back and watch as Google smears them with fake extensions that steal their good name."
Users could have spotted the fake extension based on the blob of unrelated keywords the fraudulent developer added to the extension's description. These popular keywords allowed the fake extension to pop up in unrelated search queries.
Also, if users checked the extension's Reviews tab they may have avoided this extension as most users reported the extension's abusive tab-opening behavior.
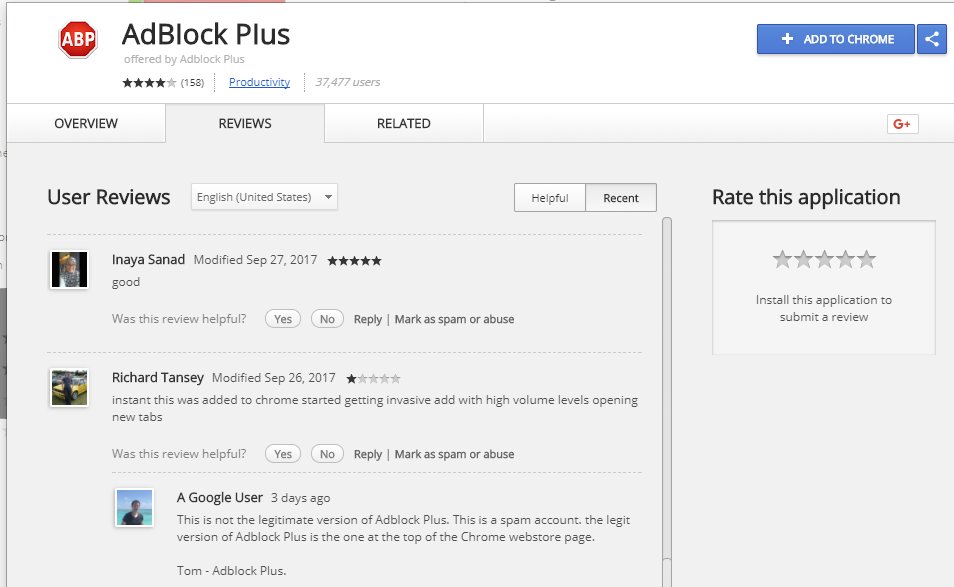
Happened before in 2015
This is not the first time that Google allowed a fake, adware-laden AdBlock Plus extension on its Chrome Web Store. Something similar happened two years ago, in 2015. That extension, too, was caught delivering adware.
Situations like this happen because the process of uploading extensions on the Chrome Web Store is automated and Google employees only intervene when the extension is reported. This automated process has allowed Google to quickly build up its Web Store, which has surpassed Mozilla's add-ons repository to become the biggest browser extensions portal among all browsers.
In this particular case, it appears that the extension's developer used a different ID than the one used by the original AdBlock Plus extension that may have taken advatange of a homograph attack using Cyrilic characters in the extension's ID to bypass Google's Web Store checks.
Image credits: SwiftOnSecurity

