| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
 [出自:jiwo.org]
[出自:jiwo.org]
On Monday, officials from Matanuska-Susitna (Mat-Su), a borough part of the Anchorage Metropolitan Statistical Area, said they are still recovering from a ransomware infection that took place last week, on July 24.
The ransomware infection crippled the Borough's government networks and has led to the IT staff shutting down a large swath of affected IT systems.
"Last Tues., July 24, the Borough first disconnected servers from each other, then disconnected the Borough itself from the Internet, phones, and email, as it recognized it was under cyber attack," said Mat-Su Public Affairs Director Patty Sullivan.
"Since then, infrastructure is steadily being rebuilt, computers cleaned and returned, and email, phones, and Internet connection becoming restored."
Mat-Su plans to clean and rebuild 650 PCs and servers
Officials said they were planning to clean and reinstall 650 desktop computers and servers located on the parts of the Mat-Su network believed to be affected.
"A new, clean network is being built," Sullivan said last Friday. By Monday, Mat-Su officials managed to clean and return to service 110 of employee workstations.
The phone server was rebuilt Sunday night, and some Mat-Su phones started coming back online on Monday. The Mat-Su email server is still being rebuilt, officials said on Monday. Sullivan said that 20 different agencies and private sector vendors have assisted the government reconstruct its IT infrastructure in the past week, through the weekend.
Payment card data was deemed safe because it was stored with third-party providers and not on the Borough's servers. Mat-Su officials said they hadn't seen any evidence attackers exfiltrated user personal data, something that regularly doesn't happen in a ransomware attack.
The Mat-Su official website was never affected, and officials kept the public informed about affected/working public services via their Facebook page. The Mat-Su door lock card swipe system also had its data encrypted, but continued to work regardless.
"Without computers and files, Borough employees acted resourcefully," Sullivan said last week. "They re-enlisted typewriters from closets, and wrote by hand receipts and lists of library book patrons and landfill fees at some of the 73 different buildings."
Mat-Su hit by "multi-pronged, multi-vectored attack"
Mat-Su IT Director Eric Wyatt met with FBI agents last Wednesday to isolate and identify the "virus" and gather information that "will help in the FBI's work to identify the criminals for prosecution."
Wyatt called the virus "a multi-pronged, multi-vectored attack." He also described it as "not a single virus but multiple aspects of viruses together including trojan horse, Cryptolocker, time bomb, and dead man’s switch." Wyatt also said the "virus" also searched and tried to corrupt the borough's backups, which he says, it failed.
"This is a very insidious, very well-organized attack," Wyatt said. "It's not a kid in his mom’s basement."
In a PDF report published yesterday, Wyatt finally identified the "virus" as the BitPaymer ransomware. This ransomware strain was first spotted in July 2017, and it first made news headlines in August 2017 when it hit a string of Scottish hospitals.
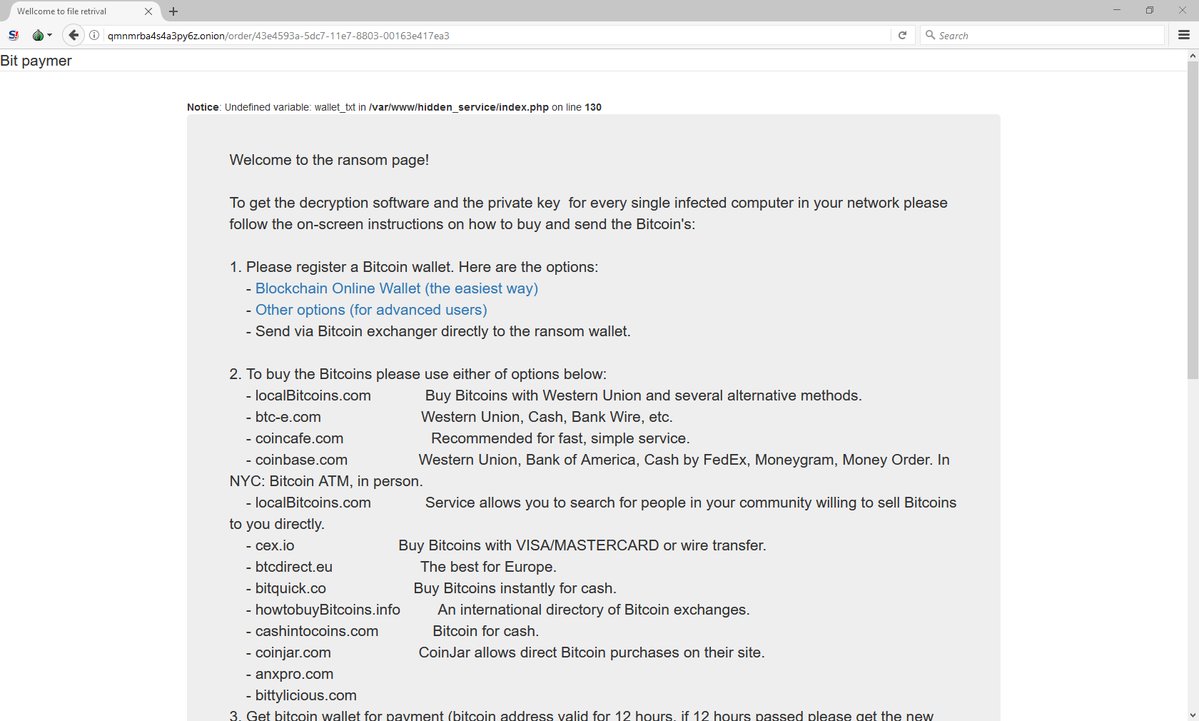
Typical Tor-based ransom payment site for BitPaymer infections
An ESET report from January 2018 claimed the ransomware —also known as FriedEx— contained evidence linking it to the same criminal group running the infamous Necurs spam botnet and the Dridex banking trojan.
BitPaymer dormant on Mat-Su network since May
"This attack appears to have been lying dormant and/or undiscovered within our network since as early as May 3rd" Wyatt said in the report.
Wyatt says that their McAfee antivirus installations started to pick up the "trojan" part of the BitPaymer ransomware on July 17.
"This was only seen on Windows 7 machines," Wyatt said. "McAfee was then doing its job of detecting and deleting the Trojan, but continued to miss all other components."
"We developed a script to remove the discovered components that McAfee was leaving behind from all machines and planned to launch this on Monday evening, July 23rd. We also expired all user passwords to force password changes and changed passwords for all admin and service accounts," Wyatt said.
"This action, of attacking back, seemed to trigger the virus to launch the Crypto Locker component. This trigger may have been automated, a Dead Man’s Switch, or there may have been a person manually monitoring activity and executed their Command and Control (C2) to launch the attack."
Wyatt said the ransomware then encrypted all 500 Mat-Su desktop workstations and 120 of 150 Mat-Su servers. At this point, Wyatt took the Mat-Su network offline, notified the FBI, and started the network rebuilding operation. Wyatt didn't say if they paid ransoms for any of the infected systems, but he said that some data was recovered from backups.
Mat-Su borough is victim #210
Investigators who aided the Mat-Su IT staff told Wyatt that not that many organizations have been hit by this threat until today. They said the Mat-Su Borough was victim number 210.
Wyatt also said in the report that the Mat-Su government wasn't the only one affected, revealing that the city of Valdez, Alaska is also dealing with a similar attack, which also appears to be a BitPaymer infection. This turned out to be true, according to a statement Valdez city officials published on Facebook on July 28, who acknowledged dealing with with a "computer virus," albeit they did not specify it was a ransomware infection.

Wyatt also said "there are reports that on Friday multiple other locations in Alaska and around the US were hit." Bleeping Computer was unable to surface any other similar public domain reports about BitPaymer or other ransomware infections with similar patterns last week.
The Fairbanks North Star Borough also admitted to a ransomware incident last Wednesday, but this appears to be unrelated, as it took place in April and the point of intrusion was a third-party responsible for EMS ambulance billing.
原文链接:https://www.bleepingcomputer.com/news/security/bitpaymer-ransomware-infection-forces-alaskan-town-to-use-typewriters-for-a-week/

