| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
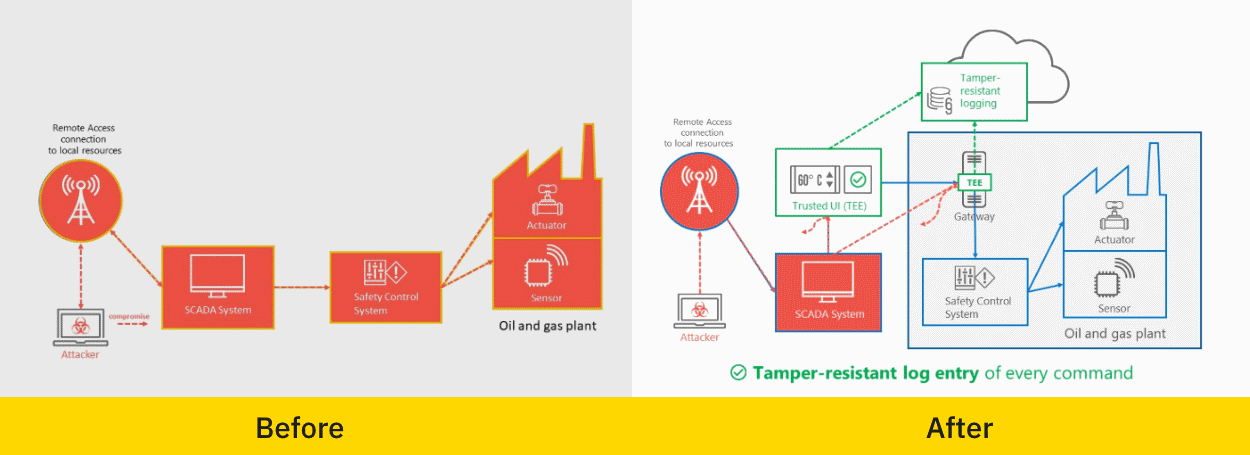
微软发布一个代号为TCPS-short的物联网项目,为物联网和工控系统设备提供一个强化系统,从三个方面进行捕获或者阻止入侵。第一个是硬件级可信执行环境;第二个组件是一个图形用户界面,提供安全确认终端;第三个是基于云的平台,可用于配置,密钥管理。证书颁发,补丁管理和防篡改日志记录。
 [出自:jiwo.org]
[出自:jiwo.org]
Microsoft engineers have started working on a new project codenamed TCPS —short for Trusted Cyber Physical Systems— that is intended to provide a hardened system for securing Internet of Things (IoT) and Industrial Control Systems (ICS) devices.
Microsoft formally announced TCPS at the Hannover Messe 2018, a trade show for industrial technology that took place last week.
According to Microsoft, TCPS systems are designed to utilize three elements to catch and block intrusions.
The first is a hardware-level Trusted Execution Environments (TEEs) such as Intel SGX, ARM TrustZone, and SecureElements. Such systems are found on processors and are hardware-separated areas of modern CPUs meant to process highly-sensitive information.
If low-resource ICS or IoT devices don't come with support for a hardware-level TEE component, then companies are supposed to deploy a so-called "brownfield gateway," an intermediary point that funnels all commands from upstream equipment to IoT devices, sensors, actuators, or safety control systems through one server/host (that supports a TEE).
The second component is a graphical user interface (GUI) that is meant to appear on what Microsoft considers a "Secure Confirmation Terminal," operated by a trusted employee.
Whenever a TEE gateway receives a command to execute certain operations, a GUI prompt will appear on the trusted terminal. No code executes unless it gets approval from the human operator.
If the operator confirms an operation, then the TEE cryptographically signs the command that is then forwarded for use by the rest of the system.
But if a command to execute came out of nowhere, the operator can easily detect when malware might be trying to interact with IoT/ICS systems, and block the attempt before it can cause any harm.
The third and last component of Microsoft's TCPS is a cloud-based platform that could be used for provisioning, key management, certificate authority, patch management, and tamper-proof logging. Since we're talking about a Microsoft project, Azure will be the default go-to solution.
Normally, good IoT and ICS systems utilize various security features to protect data in transit (data moving between devices — e.g., use of HTTPS encryption) and data at rest (data stored on a device — e.g., cryptographic file signatures).
According to Microsoft, the purpose of its new TCPS project is to add support for the last missing piece in IoT and ICS systems design —protection for data in execution— by utilizing TEEs, similar to how they're used on desktops and laptops.
Microsoft cited the recent attacks with the Trisis/Triton malware as the reason it started working on TCPS. This malware has been used in a cyber-attack last year when hackers attempted to intentionally damage safety systems at an Aramco gas and oil plant in order to cause an explosion that could lead to physical damage and even loss of human life.
TCPS is a tri-component system
TCPS meant to provide protection for "data in execution"

