For the past few months, Unit 42 researchers have investigated a relatively unknown coin mining Trojan that goes by the name ‘Rarog’.
Rarog has been sold on various underground forums since June 2017 and has been used by countless criminals since then. To date, Palo Alto Networks has observed roughly 2,500 unique samples, connecting to 161 different command and control (C2) servers.
Rarog has been seen primarily used to mine the Monero cryptocurrency, however, it has the capability to mine others. It comes equipped with a number of features, including providing mining statistics to users, configuring various processor loads for the running miner, the ability to infect USB devices, and the ability to load additional DLLs on the victim.
Rarog is in line with the overall trends we’ve seen regarding the rapidly increasing use of cryptocurrency miners. Additionally, Rarog provides an affordable way for new criminals to gain entry into this particular type of malware.
To date, we have confirmed over 166,000 Rarog-related infections worldwide. The majority of these occur in the Philippines, Russia, and Indonesia. While a large number of infections have been recorded by various criminals who have used this mining Trojan, we have seen very little recorded profits: the highest profits we have observed amount to roughly US $120.
The Trojan itself is likely named after a “Raróg”, a fire demon that originates in Slavic mythology and is typically represented as a fiery falcon.
Rarog on the Underground
The Rarog Trojan originated on various Russian-speaking criminal underground sites in June 2017, as shown in the image below:

Figure 1 Posting in Russian underground forum for Rarog malware
The malware sells for 6,000 Rubles, or roughly US $104 at today’s exchange rates. Additionally, a guest administration panel is provided to allow potential buyers the chance to do a “test drive” by interacting with the interface. This interface may be seen below:

Figure 2 Rarog administration panel
Note the two Twitter handles shown in the administration panel above. The first handle, “arsenkooo135”, is the same handle used in various postings for this malware family, including the one shown in Figure 1. We observed the second handle, “foxovsky”, interacting with other security researchers online. We also tied this handle to a GitHub repository with the same handle that hosts various other malware families. Evidence suggests that these two individuals are the ones behind this threat.

Figure 3 Foxovsky handle on Twitter interacting with security researchers regarding the Rarog malware family

Figure 4 Foxovsky’s GitHub profile, hosting various malware families
Additionally, we have seen the “foxovsky” account on GitHub host the Rarog malware family on his or her GitHub account.
Rarog Malware Family
At a very high level, the Rarog Mining Trojan performs the following actions:

Figure 5 Rarog flow of execution
The malware comes equipped with a number of features. It uses multiple mechanisms to maintain persistence on the victim’s machine, including the use of the Run registry key, scheduled tasks, and shortcut links in the startup folder. At its core, Rarog is a coin mining Trojan and gives the attackers the ability to not only download mining software but configure it with any parameters they wish. They’re also able to easily throttle the mining software based on the victim machine’s characteristics.
In addition to coin mining, Rarog also employs a number of botnet techniques. It allows the attackers to perform a number of actions, such as downloading and executing other malware, levying DDoS attacks against others, and updating the Trojan, to name a few. Throughout the malware’s execution, a number of HTTP requests are made to a remote C2 server. An overview of all of these URIs and their description may be found below:
|
URI
|
Description
|
|
/2.0/method/checkConnection
|
To ensure the remote server is responding as expected.
|
|
/2.0/method/config
|
Get arguments to supply to miner program.
|
|
/2.0/method/delay
|
Retrieve time to sleep before executing miner program.
|
|
/2.0/method/error
|
Retrieve information about error message to display to the victim.
|
|
/2.0/method/get
|
Get location of miner file based on CPU architecture of victim.
|
|
/2.0/method/info
|
Get exe name of miner program.
|
|
/2.0/method/setOnline
|
Update statistics for victim on C2 server.
|
|
/2.0/method/update
|
Used for updating the Rarog Trojan
|
|
/4.0/method/blacklist
|
Retrieve a list of process names to check against. Should any be running in the foreground, Rarog will suspend mining operations.
|
|
/4.0/method/check
|
Query remote C2 server to determine if ID exists.
|
|
/4.0/method/cores
|
Retrieve percentage of CPU to use on victim machines for mining.
|
|
/4.0/method/installSuccess
|
Query the C2 server for botnet instructions.
|
|
/4.0/method/modules
|
Retrieve third-party modules to load on victim.
|
|
/4.0/method/threads
|
Determine what tasks to run on the victim machine (USB spreading, helper executables, etc.)
|
For additional information on how the Rarog malware family operations, please refer to the Appendix.
Victim Telemetry
We identified a total of 161 C2 servers communicating with the Rarog malware family. A full list may be found in the Appendix.Looking at the geographic distribution of these C2 servers, we see a high concentration of them located in Russia and Germany.
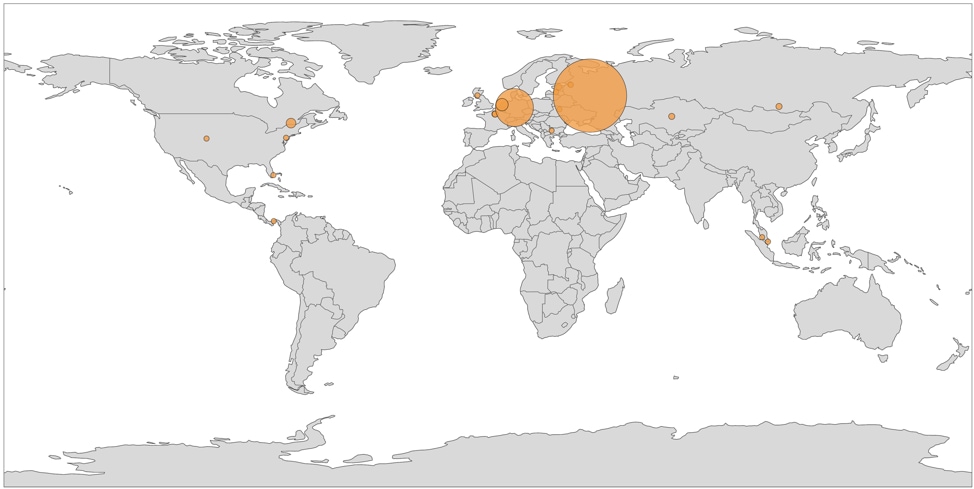
Figure 6 Distribution of C2 servers hosting Rarog malware
The distribution rate of new Rarog samples has varied in the past nine months, with a large spike occurring between late August to late September of 2017. At its peak, we encountered 187 unique Rarog samples during the week of September 11, 2017.

Figure 7 New Rarog malware samples encountered over time
These samples confirm at least 166,000 victims spread across the globe. While infections occur in most regions of the world, high concentrations occur in the Philippines, Russia, and Indonesia, as seen in the figure below:

Figure 8 Rarog infections across the globe
Rarog is able to provide telemetry those that have purchased it using the third-party MinerGate mining service. A number of MinerGate API keys were able to be retrieved, however, the profits made by these attackers were minimal at best. The most profitable attacker was found to generate roughly 0.58 Monero (XMR), and 54 ByteCoin (BCN). By today’s exchange rates, this amounts to $123.68 total. After factoring in the cost of the malware itself at $104, the attackers in question have generated very little income. In most cases, they’ve lost money.
Ties to Previous Malware Families
In late October 2017, Kaspersky wrote a blog post about a malware family named ‘DiscordiaMiner’. In this blog post, they describe a cryptocurrency miner that shared a number of characteristics with Rarog. Upon further inspection, they mention the author of the program, who is none other than the previously mentioned “foxovsky” user. Indeed, when looking at this user’s GitHub account in Figure 4, we saw the source code to this mining Trojan. The last time the source code to this particular malware was updated was on May 25th, 2017.
Looking at the source code to DiscordiaMiner, we see a large number of similarities with Rarog. So many in fact, that we might reach the conclusion that Rarog is an evolution of Discordia. Kaspersky’s blog post discussed some drama concerning this particular malware family on various underground forums. Accusations were made against the Trojan’s author with substituting customer’s cryptocurrency wallet addresses with his own. This dispute is what ultimately led foxovsky to open-source the DiscordiaMiner program on GitHub. The timeline of when Rarog was first advertised in June 2017, as well as the time DiscordiaMiner was last updated in May 2017, paints, and interesting picture. Based on this information, as well as the heavy code overlap made between the malware families, I suspect that foxovsky rebranded DiscordiaMiner to Rarog and continued development on this newly named malware family. This re-branding allowed him to get away from the negativity that was associated with DiscordiaMiner.
Conclusion
The Rarog malware family represents a continued trend toward the use of cryptocurrency miners and their demand on the criminal underground. While not incredibly sophisticated, Rarog provides an easy entry for many criminals into running a cryptocurrency mining botnet. The malware has remained relatively unknown for the past nine months barring a few exceptions. As the value of various cryptocurrencies continues to remain high, it is likely that we’ll continue to see additional malware families with mining functionality surface.
Palo Alto Networks customers are protected against this threat in the following ways:
-
All samples referenced in this blog post are appropriately marked as malicious in WildFire and Traps
-
All domains used as C2 servers for Rarog are flagged as malicious
-
Tracking of the Rarog malware family may be done through the AutoFocus Rarog tag









