| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
研究人员发现一个将.velso扩展名附加到加密文件的,新的勒索软件Velso。虽然没有100%确认,但研究人员表示攻击者可能是通过远程桌面服务RDP入侵受害者机器,然后手动安装勒索软件。
A new ransomware is actively infecting victims called the Velso Ransomware. This ransomware appends the.velso extension to encrypted files and then drops a ransom note that contains an email address that a victim can use to contact the developer.
In this article I will provide a brief summary of what we know about the velso ransomware and how you can protect yourself from it. You can also discuss or receive support for the Velso Ransomware in our dedicated Velso Ransomware Help & Support Topic.
The Velso Ransomware was first discovered by Michael Gillespie when saw a submission to his ID-Ransomware site. After tweeting about the sample, another researcher named Martin Stopka was able to find a sample of the infection.
While it is not 100% confirmed, it appears that the Velso Ransomware is installed manually by an attacker hacking into a victim's computer via remote desktop services. The attacker then manually executes the ransomware file. This causes it to display the victim's ID and then the decryption key while it pauses waiting for the attacker to press a key on the keyboard.
Once the attacker has finished copying the two strings, they can press any key and start the process of encrypting the computer. You can see below what the ransomware looks like when it was executed by BleepingComputer.
When encrypting files, it will modify the filename by appending the .velso extension to the encrypted file's name. For example, a file named test.jpg would be encrypted and renamed to test.jpg.velso.
A ransom note will also be created in every folder that a file is encrypted. This ransom note is namedget_my_files.txt and contains an email address that a victim can contact for payment instructions and the victim's unique ID. The current email address is MerlinVelso@protonmail.com.
The get_my_files.txt will be copied in the Windows Startup folder so that it is automatically displayed when a user logs into the computer.
Unfortunately, at this time there are no known weaknesses that could allow a victim to recover their files for free.
To protect yourself from the Velso Ransomware, it is particularly important that you do not have any computers running remote desktop services connected directly to the Internet. Instead place computers running remote desktop behind VPNs so that they are only accessible to those who have VPN accounts on your network.
In order to protect yourself from ransomware in general, it is important that you use good computing habits and security software. First and foremost, you should always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
You should also have security software that incorporates behavioral detections to combat ransomware and not just signature detections or heuristics. For example, Emsisoft Anti-Malware and Malwarebytes Anti-Malware both contain behavioral detection that can prevent many, if not most, ransomware infections from encrypting a computer.
Last, but not least, make sure you practice the following security habits, which in many cases are the most important steps of all:
For a complete guide on ransomware protection, you visit our How to Protect and Harden a Computer against Ransomware article.
What we know about the Velso Ransomware
— Martin Stopka (@stopka_martin) January 17, 2018
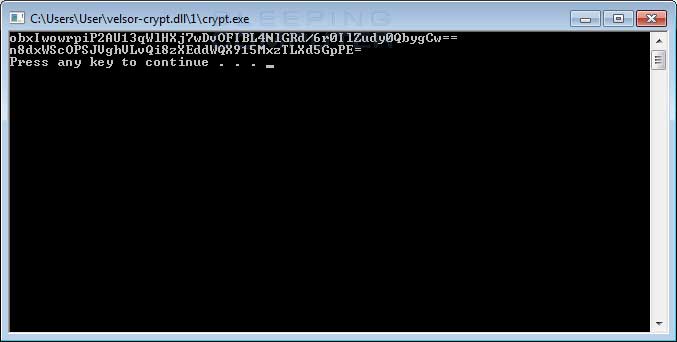 Velso Ransomware
Velso Ransomware
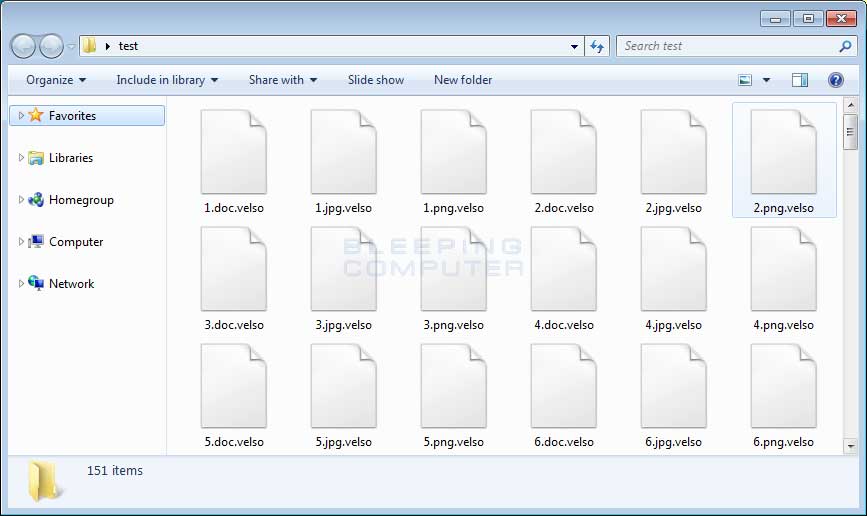 Folder of Encrypted Velso Files
Folder of Encrypted Velso Files
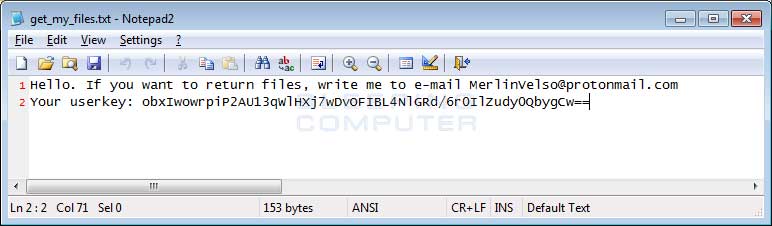 Velso Ransom Note
Velso Ransom Note
How to protect yourself from the Velso Ransomware
IOCs
Server Hashes:
SHA256: 4c8cf7ce3836edceb540edeccae97ef182331f6ed93e678d2e33105d01e809bf
Filenames associated with the Server Cryptomix Variant:
get_my_files.txt
Server Ransom Note Text:
Hello. If you want to return files, write me to e-mail MerlinVelso@protonmail.com
Your userkey: obxIwowrpiP2AU13qWlHXj7wDvOFIBL4NlGRd/6r0IlZudy0QbygCw==
Emails Associated with the Server Ransomware:
MerlinVelso@protonmail.com
[出自:jiwo.org]

