| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考1(官网) | |
| 参考2 | |
| 参考3 |
Chrome扩展程序Archive Poster将挖矿代码,推送给105,000未知情用户。当Chrome浏览器打开时,扩展程序劫持用户CPU来挖掘Monero加密货币。 [出自:jiwo.org]
A Chrome extension with over 105,000 users has been deploying an in-browser cryptocurrency miner to unsuspecting users for the past few weeks.
The extension does not ask for user permission before hijacking their CPUs to mine Monero all the time the Chrome browser is open.
Named "Archive Poster," the extension is advertised as a mod for Tumblr that allows users an easier way to "reblog, queue, draft, and like posts right from another blog's archive."
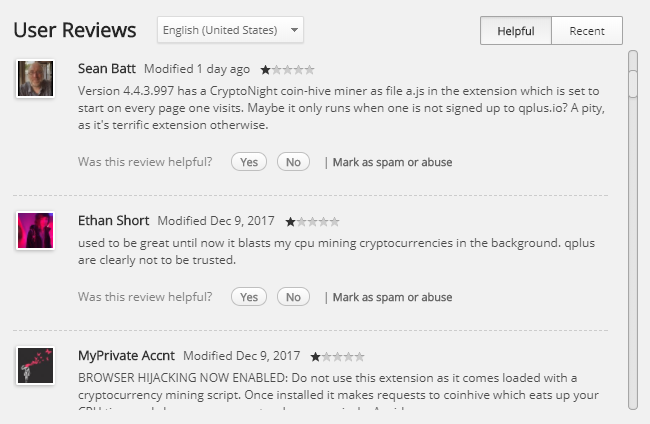
According to users reviews, around the start of December the extension has incorporated the infamous Coinhive in-browser miner in its source code.
Troy Mursch, a US-based security researcher who's been keeping a close eye on the cryptojacking scene, alerted Bleeping Computer of this threat today.
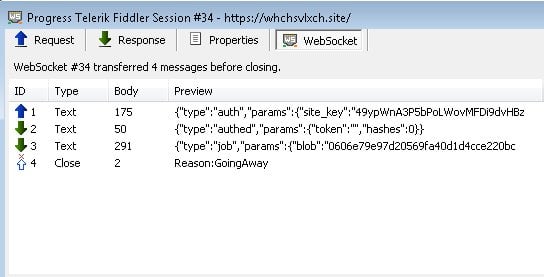
According to Mursch, the Coinhive cryptojacking code is hidden in a JavaScript file loaded from the following URL:
"b.js summons whchsvlxch[.]site which invokes three websocket sessions (c.wasm) to start the #cryptojacking process," Mursch says. These three sessions contain Coinhive configuration options.
The Archive Poster extension has been shipping the hidden Coinhive cryptojacker for at least four versions —from 4.4.3.994 to 4.4.3.998.
Users have been reporting the extension and giving it bad reviews for the past weeks but to no avail.
Google doesn't seem to care, allowing the extension to continue to be available on the official Chrome Web Store. A user even reported Archive Poster on the Google Chrome Help Forum, but a Google staffer told the user "to get in touch with the extension developer for further assistance."
Over the spring and summer, Chrome extension developers have been under a barrage of phishing attacks. Miscreants were trying to take over extensions, adding adware code and pushing a tainted update to the extension's userbase when successful.
Some of these phishing attacks were successful, and several cases were reported when high-profile extensions with large userbases were hijacked to push adware [1, 2, 3].
The company behind Archive Poster does not have a contact method listed on its website, so Bleeping Computer wasn't able to confirm this was intentional or another case of a hijacked extension.
https://c7e935.netlify[.]com/b.js
Another case of a hijacked extensions? or is it intentional?

