| 关联规则 | 关联知识 | 关联工具 | 关联文档 | 关联抓包 |
| 参考 |
A new method of carrying out DDoS attacks named Pulse Wave is causing problems to certain DDoS mitigation solutions, allowing attackers to down servers previously thought to be secured. [出自:jiwo.org]
Discovered by DDoS mitigation firm Imperva Incapsula, the name of this new technique comes from the look of its attack chart, shaped in the form of abrupt repeating pulses.
Classic attacks usually have the shape of a sloping triangle going up and down as an attacker slowly assembles bots and aims them at a desired target.
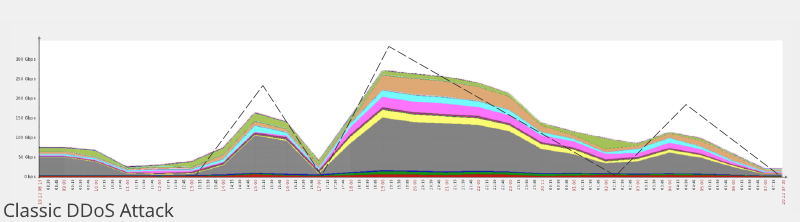
The new pulse wave attacks start from zero and go to maximum values in a very short time span, then go back to zero, and back to maximum, repeating in continuous cycles at short clocked intervals.
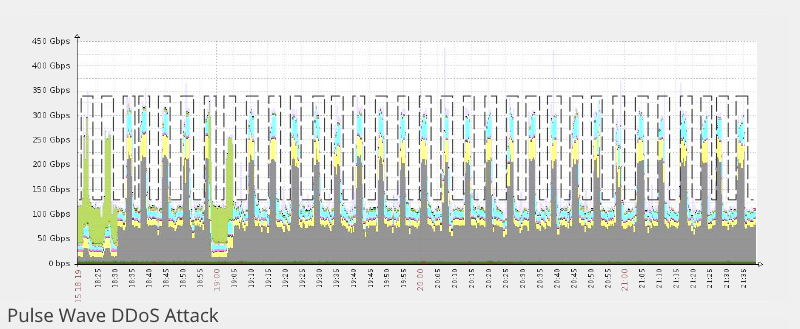
One botnet leveraging the technique
Experts say they've seen pulse wave attacks in the past, but a recent botnet that has been active in the second quarter of 2017 has been using this technique on a regular basis.
"Whoever was on the other end of these assaults, they were able to mobilize a 300Gbps botnet within a matter of seconds," said Igal Zeifman, director of marketing at Incapsula. The biggest pulse wave DDoS attacks from this botnet peaked at 350 Gbps, a value way above the average of ~1 Gbps per normal DDoS attack.
Imperva analysts say that during the pulse wave attack's short downtime period, the botnet doesn't shut down and restart again a few minutes later.
Instead, experts say, the botnet switches to another target. When the down pulse period finishes, the botnet switches back to the first target executes a short pulse wave cycle and then changes to another target.
Pulse wave attacks cause problems to hybrid mitigation solutions
Pulse wave attacks have not been seen from different actors, but this is about to change. Experts say that these types of DDoS attacks can cause problems to "hybrid" mitigation solutions and are bound to become attractive to other botnet herders.
Hybrid mitigation solutions are a mixture between on-premise hardware and cloud-based solutions. The on-location hardware works as the default mitigation solution but is configured to trigger a customer's cloud-based DDoS protection whenever the equipment is about to get flooded with traffic.
This DDoS protection topology is suitable for dealing with classic DDoS attacks that build over time. Because pulse wave attacks come in fast and furious, the local equipment is quickly flooded, having no time, or the necessary bandwidth, to call for the cloud-based solution.
Organizations eventually recover, but after some downtime
The equipment and the targeted organization are shut down when one pulse hits. Experts say that recovering from one pulse usually takes a few minutes, by which time another pulse jams the network. Using this new technique, attackers can shut down organizations for extended periods of time, while also carrying out DDoS attacks on other targets.
"Additionally, the lack of communication prohibits the appliance from providing information required to create an attack signature," Zeifman adds. "Even if the cloud does eventually come online, it still has to resample the traffic from scratch before initiating the filtering process."
Nonetheless, organizations have been seen to recover from pulse wave assaults, but only some prolonged downtime that usually affects the company's bottom line.
The new pulse wave DDoS attack technique is detailed in an Incapsula Imperva report, available for download here.

